CISA has recently released a project called SCuBA which is providing a security baseline for Microsoft 365. This project is currently in the alpha stages but there is a ton of great recommendations that span across the suite offerings like Azure AD, Exchange, Teams, Defender, OneDrive, SharePoint, and even Power Platform. If you are someone who is looking for a “security checklist” then this is a great project to look into. CISA has provided a tool on GitHub called SCuBA gear, which performs automatic evidence collection of where a M365 tenant matches up against the recommended baselines. In this article, I am going to show you how to run the tool and introduce you to a fork I created which additionally maps these recommendations to the CIS Controls.
Assessment Overview
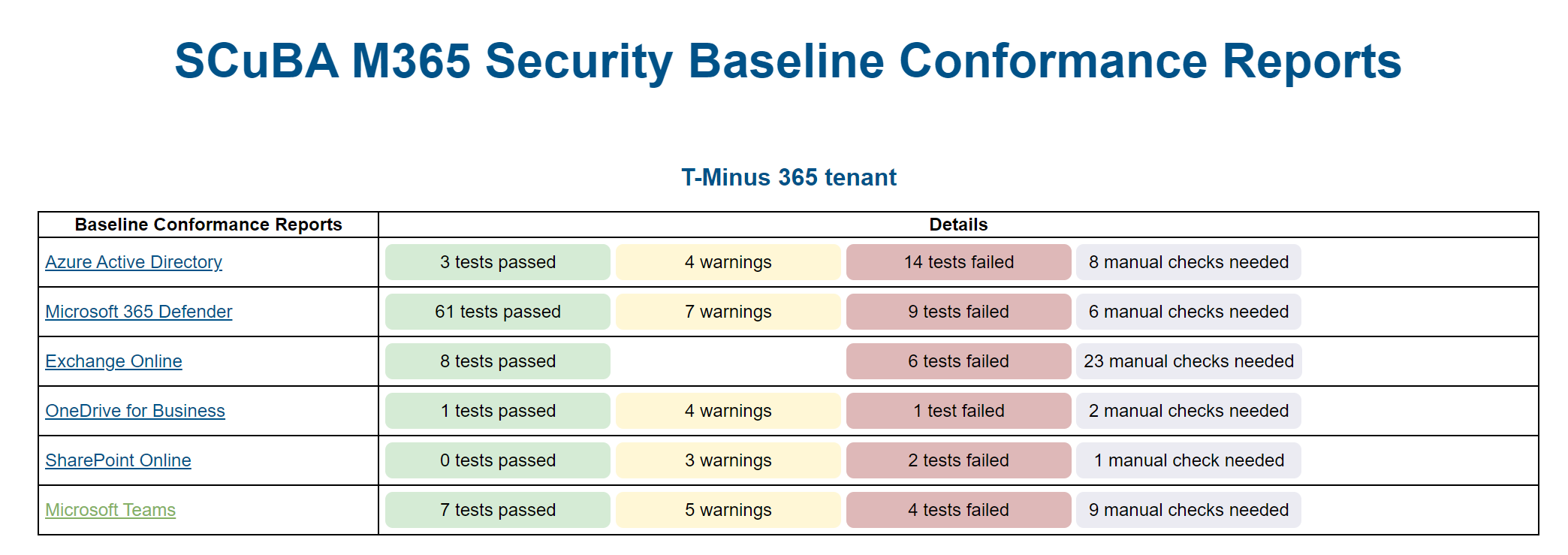
The project can be found on GitHub which includes the powershell scripts you will run to perform the assessment. The output you can see above where you can get reports generated for each product you specify in the script.
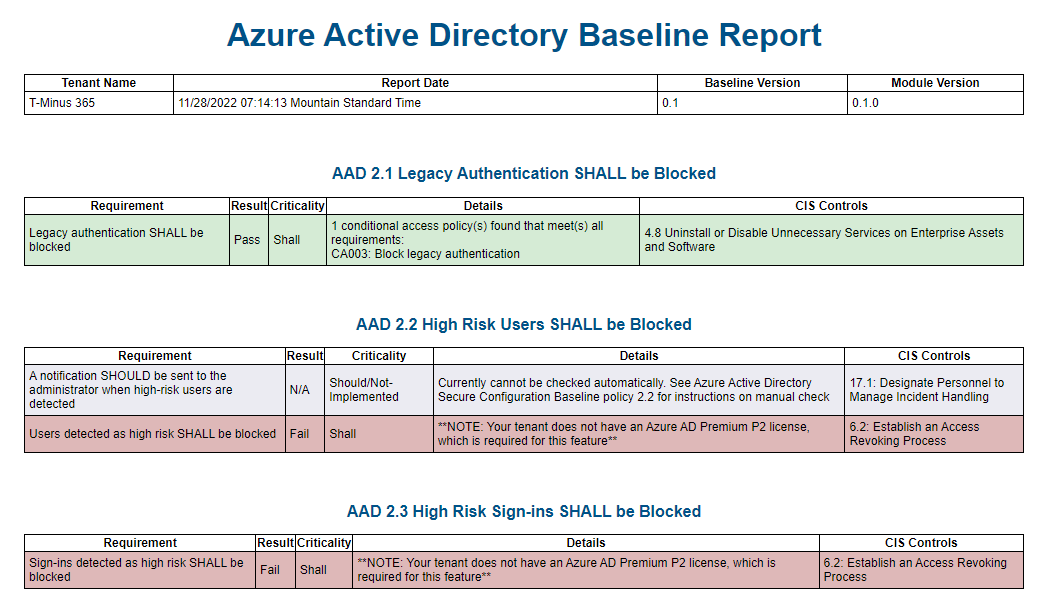
Each report contains all of the recommended baselines and is color coated based on a pass, warning, fail, or not evaluated. This is the report from my fork which is why you also see the CIS Controls.
Running the Assessment
- Download the ZIP File from the repository
- Run the Setup.ps1 file (you need to have your execution policy set to unrestricted in powershell)
- Modify the RunScuba.ps1 file to change the output file location, products to run assessments on, and the endpoint variable if you want to get an output for Power Platform
- Run the RunScuba.ps1 script
You will then have to authenticate multiple times. At a high level, this needs to be a global admin with MFA enabled. The ReadMe file provides the least privileged role per product if you would rather follow that.
After the assessment has run, a browser window will automatically open with the report. If you did not change the output path, a Reports folder will be created in your Scubagear-main folder that you downloaded originally.
Full Video Tutorial:
Notable Highlights
- The script is not built for multi-tenancy
- The script can show you if you are lacking the licensing needed for certain controls as seen in the screenshot for Azure Active Directory in Assessment overview section. (This is a tenant that has Business Premium)
- Endpoint Manager is not evaluated
- Some of the recommendations have a larger end-user impact. Make sure you understand the implications of configuring these policies
- The policy recommendations can also be found standalone here: Secure Cloud Business Applications (SCuBA) | CISA
Mapping to the CIS Controls
I wanted the CIS Controls to be part of the output so I forked the repository and built that into the script. The entries I made here were built from a combination of the existing CIS Microsoft 365 Foundations Benchmark: CIS_Microsoft_365_Foundations_Benchmark_v1.5.0 as well as the existing v8 standard CIS_Controls_v8_Online.22.02
Troubleshooting
So far, the only problem I ran into was trying to run this against multiple tenants, consecutively. I was getting some errors here and found out that I had to run Disconnect-MgGraph
This was the case even if I opened a new PowerShell window.
Final Thoughts
Overall, I think this is a great assessment that could even be used for prospecting. I am bummed the assessment isn’t pulling any information in from Endpoint Manager (Intune) as that has many critical configurations for us as well. The tool is definitely worth checking out, even in this alpha stage.
