MFA settings in Azure AD have evolved so much over the past few years and I believe that will continue at an even greater pace with the introduction of Microsoft Entra. I believe if you are a progressive MSP, you have moved your customers to licensing that supports Conditional Access over the legacy “per user” MFA settings within their Microsoft environments. Most of us are enforcing MFA for all users as a baseline policy and are using Microsoft Authenticator or Duo MFA to perform the MFA request. Usually this is just a push request to the app to satisfy the MFA prompt.
In this article, I am going to show you some MFA settings that you might not know about that I believe are game changers for security.
1. Number Matching with Microsoft Authenticator
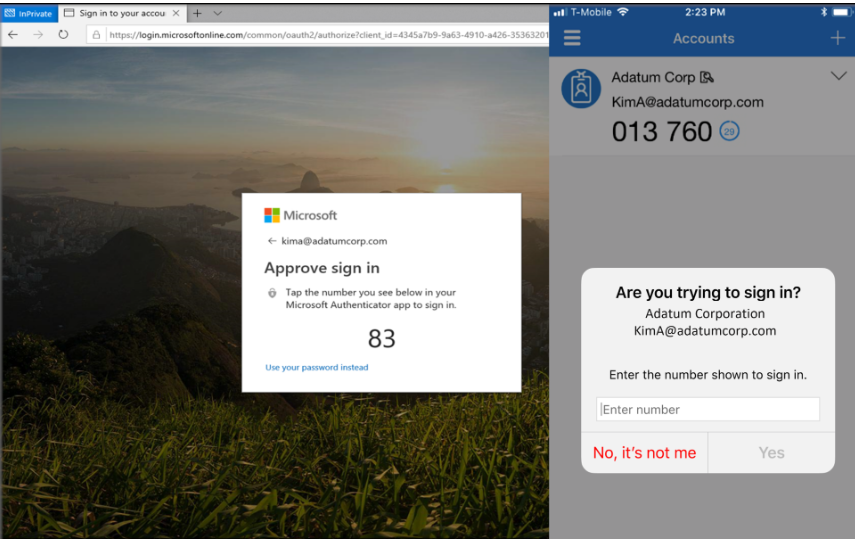
Functionality
Users are prompted to type in the number they see on their screen into the authenticator app to approve an MFA push
Why it matters
Number matching may not seem too different compared to the MFA push on the authenticator app but it is a big deal when we look at common attacks today. MFA fatigue is an attack method where a bad actor has compromised credentials to a user account and attempts to overload the user with MFA prompts. We saw this in the recent Uber breach. The compromised user could easily accept a push notification and grant access to this bad actor whereas with number matching, they wouldn’t be seeing any number to type in to approve the request.
Steps to Configure
2. Geographic Location with Microsoft Authenticator
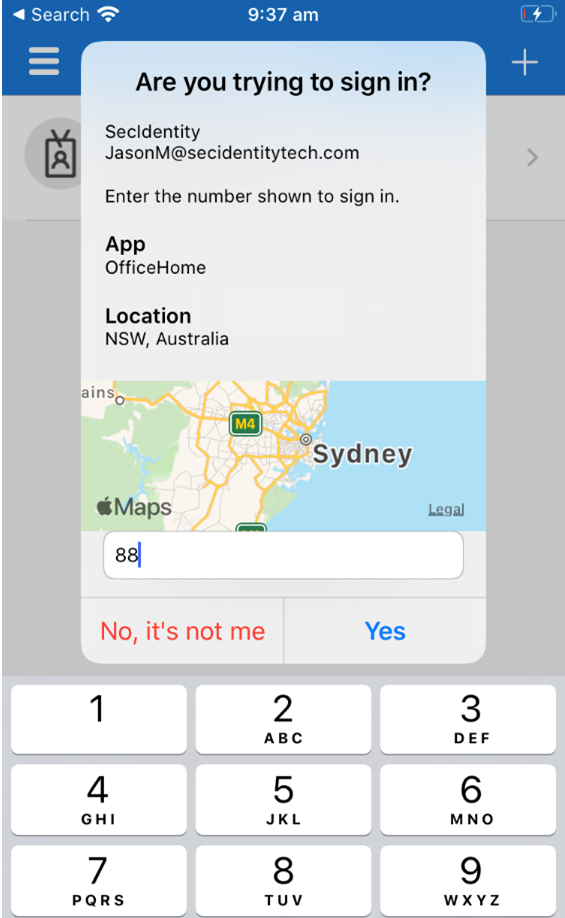
Functionality
Users are prompted to approve any MFA request but can see the geographic location the request is coming from
Why it matters
Like number matching, seeing the geographic location can help prevent against non-authorized MFA prompts and give the end user something that is an easy red flag to not approve the MFA prompt.
Steps to Configure
3. Authentication Strengths | Phishing Resistant MFA
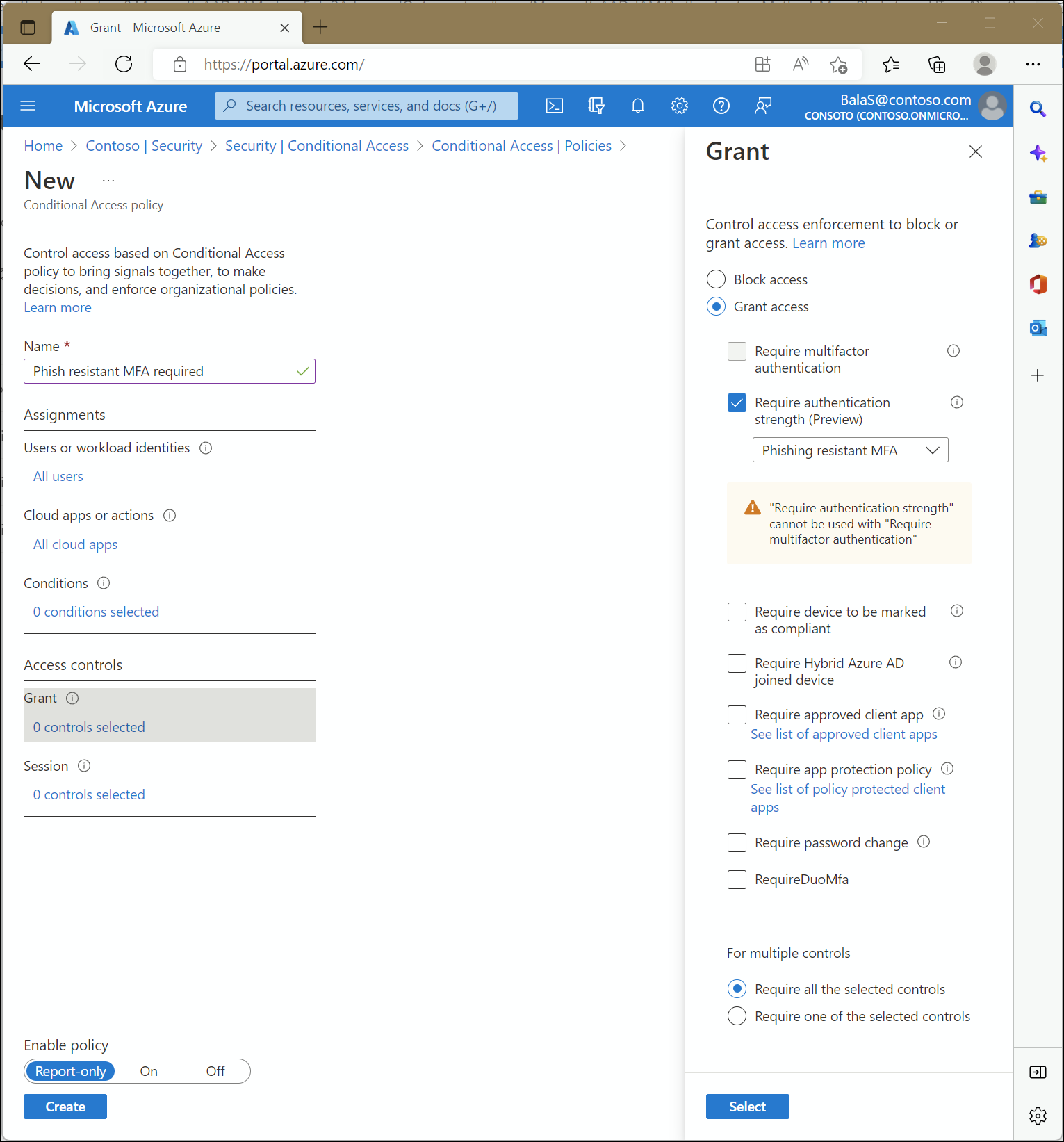
Functionality
Authentication strength is a Conditional Access control that allows administrators to specify which combination of authentication methods can be used to access a resource. For example, they can make only phishing-resistant authentication methods available to access a sensitive resource. But to access a non-sensitive resource, they can allow less secure multifactor authentication (MFA) combinations, such as password + SMS.
Why it matters
We have seen in the previous two examples that MFA enabled users can still be compromised with MFA fatigue. As an MSP, we are also trying to find a right mix between enforcing security without inhibiting user productivity. This is a great way to enforce a stronger 2nd factor for very sensitive resources at the company. It could also be used when thinking of allowing users to access corporate resources on personal devices. Stronger methods like FIDO2 keys, Windows Hello, and Certificates are a much better defense against man in the middle attacks. Combining these methods with a passwordless approach is another way with reduce your attack surface.
Steps to Configure
4. Registration Details
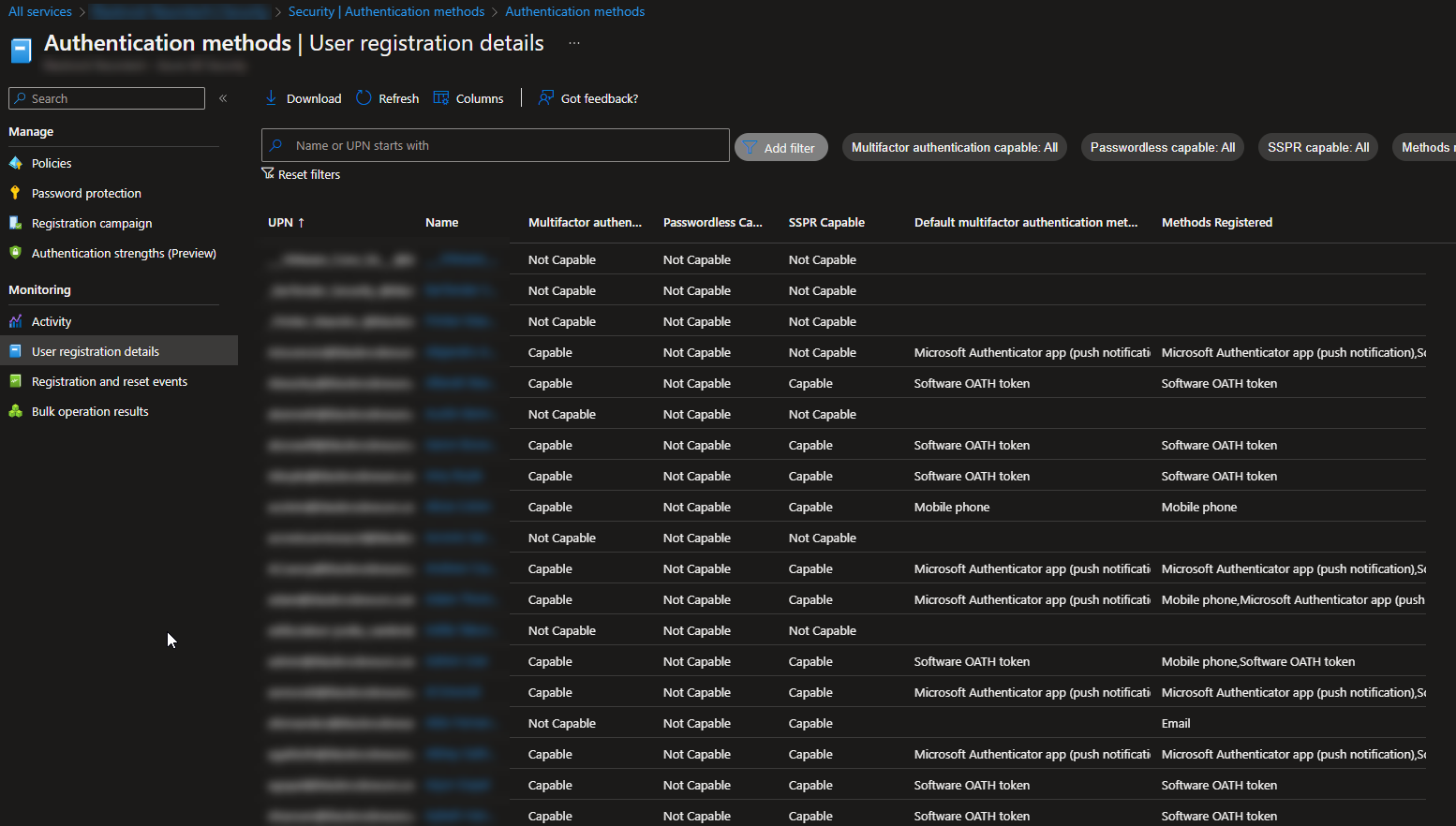
Report in Azure AD to show:
- Users registered for MFA
- Users registered for SSPR
- Users registered for Passwordless
- Default MFA method used
- MFA registration methods registered
Why it matters
This is a great report to audit periodically to ensure all users are conforming to the MFA standards set by your MSP. You can use this report to ensure 100% compliance on the MFA methods you want to enforce across the company. It could also be useful in support cases where you are troubleshooting MFA issues.
Viewing Details
Authentication Methods Activity – Azure Active Directory – Microsoft Entra | Microsoft Learn
5. Registration and reset events
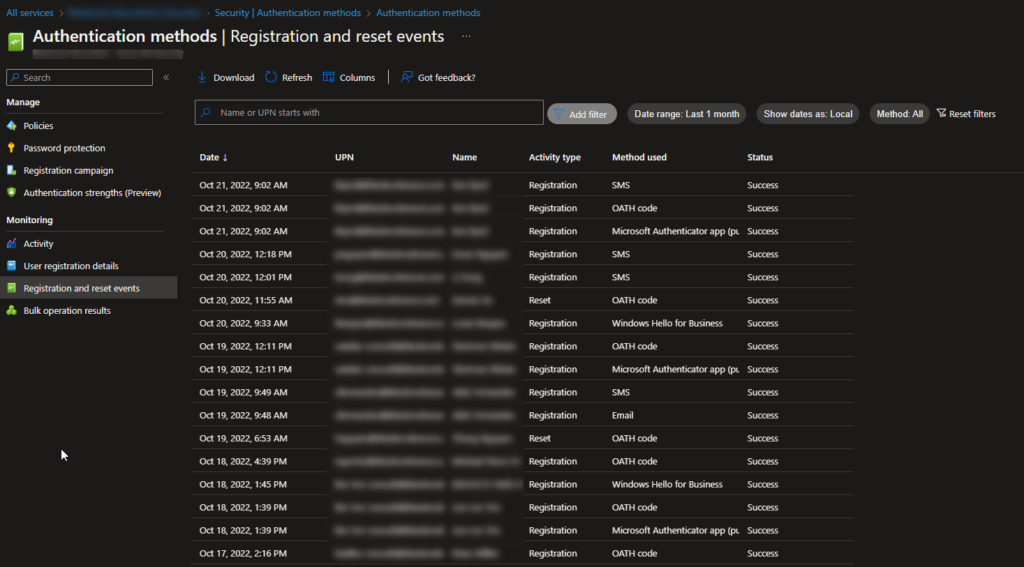
Functionality
Shows MFA registration and reset events for up to the past 30 days.
Why it matters
If a user is compromised, an attacker can register their own MFA registration method on that users account by going to aka.ms/mysecurityinfo. This is actually very common. Attackers can even register their own FIDO2 Key if the method is available in the tenant. If you suspect a user is compromised, either through the Risky Users Report or otherwise, this is a great spot to look to see if a new registration event has occurred for the user recently. If this is the case, you should be revoking their sessions, resetting their password, and requiring them to re-register for MFA.
Viewing Details
Authentication Methods Activity – Azure Active Directory – Microsoft Entra | Microsoft Learn
