Checklist do not equal compliance
One of the major gaps I hear when talking to MSPs about security and compliance is a lack of understanding the “why” behind the security checklist being instituted in client environments. Many of us out there follow some checklist, especially for Microsoft 365, that we try to implement in our customer environments upon onboarding. From there, we may use the secure score recommendations to help fill in the gaps and relay this to the customer to showcase some value on improving their security posture.
The gap comes when we start talking about policy definitions you have in place and your “north star” or framework that you follow that provides a more organized structure to understand your cybersecurity posture. Time and resources are often a large constraint to increasing our posture so we need to understand what actions we can take that will be the most impactful to our MSP and, subsequently, to our downstream customers. Here are some questions you can begin to ask yourself to understand your operational maturity in this area:
- Do we follow some type of framework or standard that provides us a consistent approach to our cybersecurity strategy?
- Do we have policy definitions written and implemented across our customers such as our incident response plan, vulnerability management, backup and disaster recovery, etc.?
- Do we have base policy definitions that can be modified dependent on the uniqueness of each customer environments?
- Do we have a formal review process for the policies and controls we have in place?
- Do we set current and target profiles for our organization as it relates to improvements in cybersecurity?
In many cases, MSPs do not have formal policy definitions in place and the lifecycle around cybersecurity is very ad-hoc or reactive in nature. If you are looking to level up in this area, check out the template I built that leverages NIST CSF 2.0 as a north star to help you begin to get organized today along with putting a WHY behind the policies and controls you are implementing.
About NIST CSF 2.0
NIST has released the official publication of NIST CSF 2.0 so I wanted to create a new enablement guide that maps Microsoft security controls to the framework and provide a self-scoring assessment to help you begin to organize your policy definitions. The Framework has been used widely to reduce cybersecurity risks since its initial publication in 2014. Many organizations have told NIST that CSF 1.1 remains an effective framework for addressing cybersecurity risks. One of the major changes in 2.0 is that the scope of the Framework has been updated to reflect use by all organizations vs just critical infrastructure.
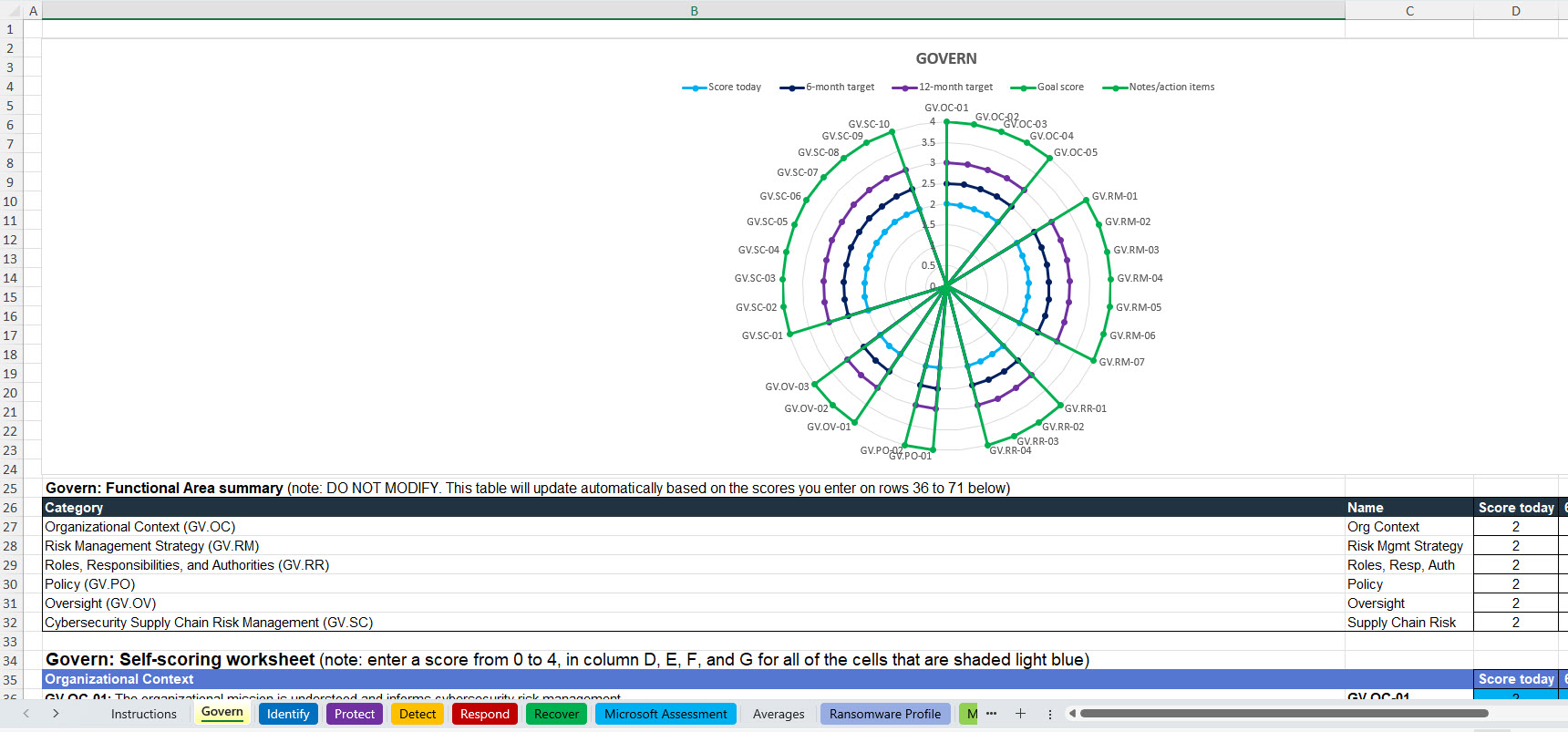
Compliance Optimization Assessment
I built in a basic self-scoring assessment for the framework that you can leverage to understand where your gaps might exist today in your cybersecurity posture. The goal of this self-assessment is to rank yourself across the NIST CSF functions based on a current and target profile. There are sheets for Gover, Identify, Protect, Detect, Respond, and Recover that you can fill out as part of the self-assessment. Scores are based on the following profile logic which is a derivative of the CSF Tiers.

There are tabs in the assessment across the CSF functions you can leverage that provide the self-assessment including a current score and target scores.
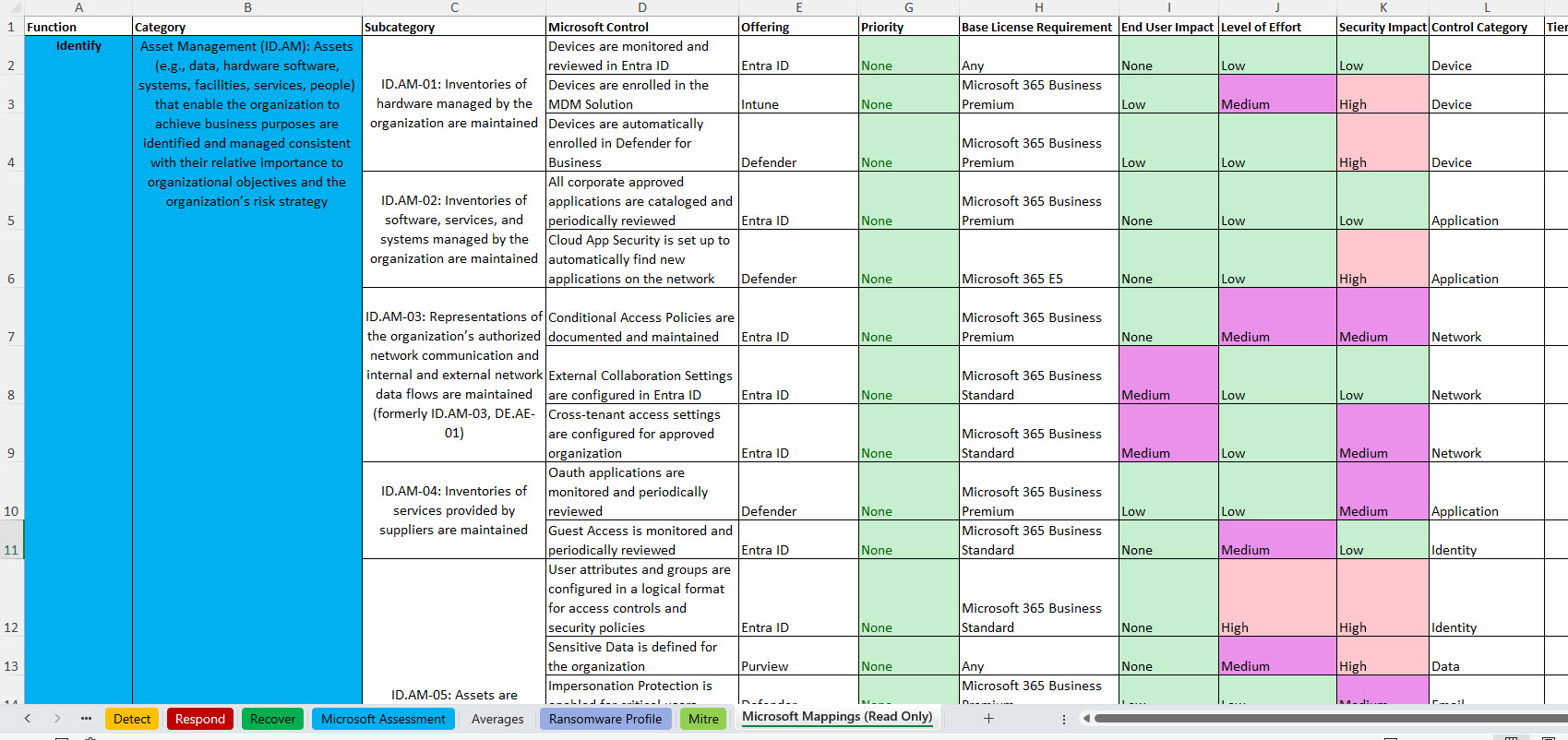
Finally, I have also mapped recommended Microsoft security controls across Entra ID, Intune, Exchange, Teams, SharePoint, OneDrive, Defender, and Purview that map to NIST CSF Functions as well. This matrix includes the base license requirements for the controls along with checklist columns so you can track your progress implementing these controls across customers.
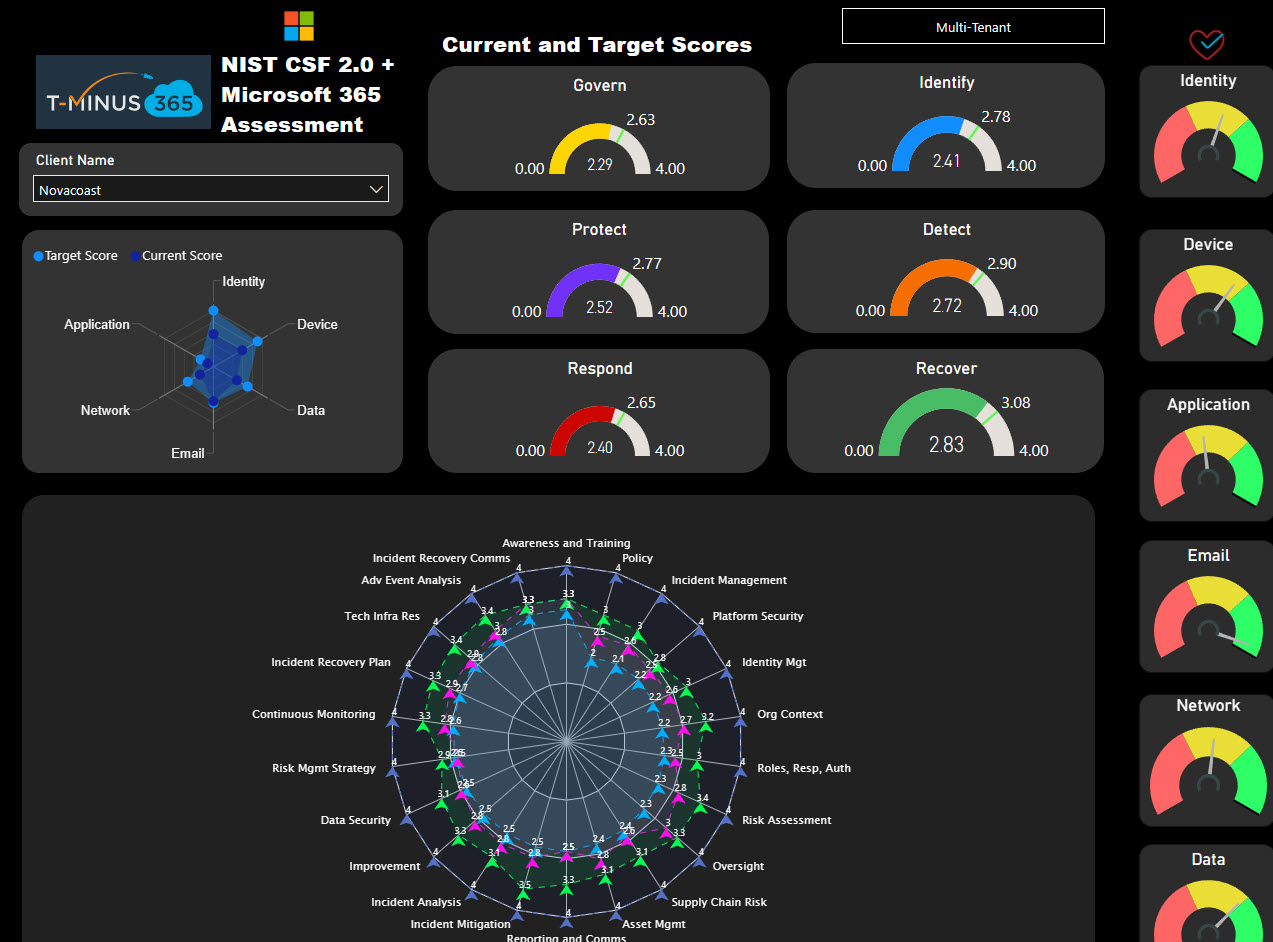
Power BI Template and Ebook
If you wanted to level up beyond the self-scoring assessment, I have also created an enablement ebook and multi-tenant Power BI template you can leverage to track these assessments over time, across all of your customers. The ebook contains other helpful resources such as:
- Set-up instructions for each Microsoft control
- PowerShell Scripts
- Video Tutorials
- 40+ End-User notification templates for controls that impact end-users
Get this copy at a discount (25%) for a limited time. Use discount code NISTMATRIX at checkout
