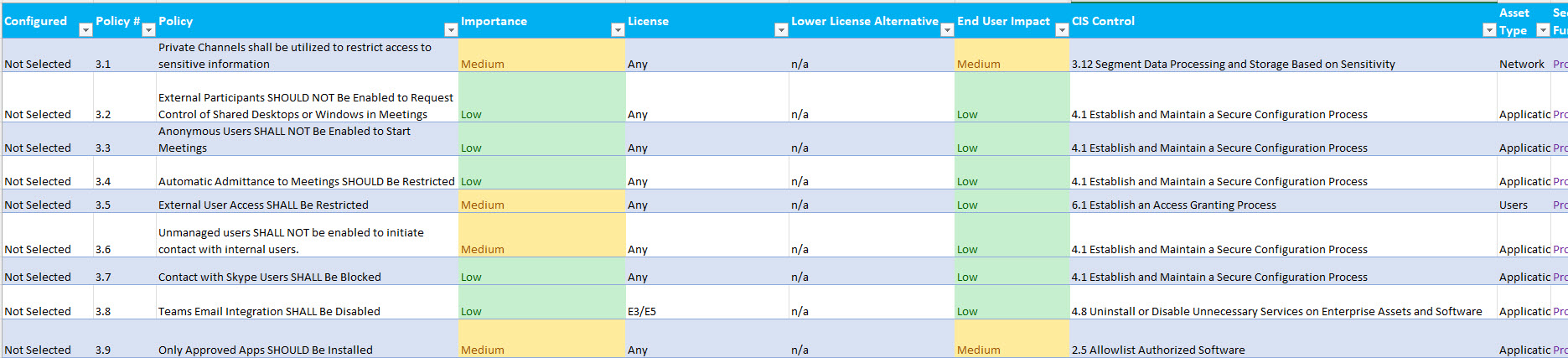
Many of us out there are using Microsoft Teams as our main source of collaboration. This includes chats, meetings, and even file sharing. As an organization, its where we are potentially sharing tons, if not all, of our sensitive information which is why it is SO important to protect. I wanted to walk you through my top security recommendations that are mapped to the CIS Controls. If you are not familiar with the CIS Controls, they are basically a set of best practices to follow for cybersecurity and can provide a lot of assistance on what to prioritize.
I do have a more extensive list of security recommendations outside the ones I will be showing today along with the steps for configuring these settings, end-user impact, and enablement content. You can get the full guide below. Feel free to also check out a sample of the guide first: Security Baselines_CIS Controls_Sample
Top Tips
1. Leverage Private Teams and Shared Channels
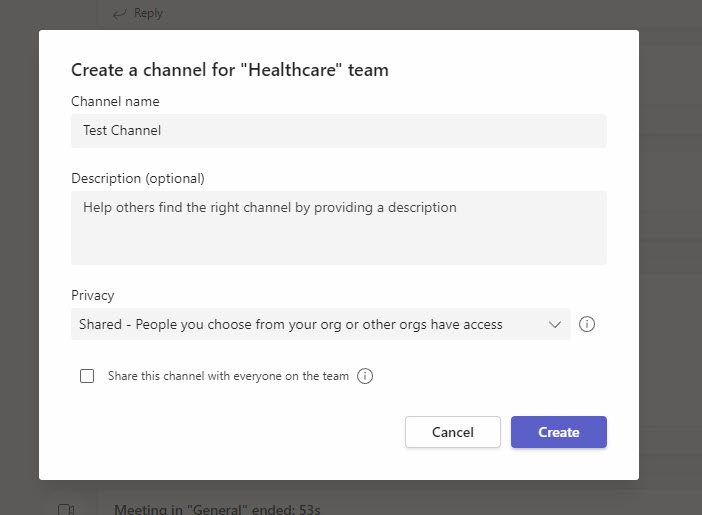
Access controls are a fundamental part of any compliance regulation. Giving access to certain Teams channels where users are collaborating on sensitive topics or sharing critical documents should follow a model of least privilege. Microsoft Teams allows you to create private channels where users can request access to the owners and all other users are prohibited from seeing the content.
Additionally, Shared Channels allow you to explicitly grant access to a channel for users both inside AND OUTSIDE your organization. This is a great way to securely collaborate with external users.
Both of these options differ from a public channel, where anyone in the org can gain access. A formal process should be in place for when new Teams or channels are created.


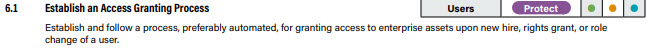
2. External User access shall be restricted
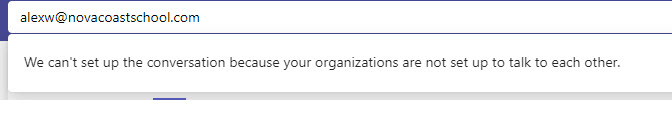
External access allows external users to look up internal users by their email address to initiate chats and calls entirely within Teams. Blocking external access prevents external users from using Teams as an avenue for reconnaissance or phishing. Even with external access disabled, external users will still be able to join Teams calls, assuming anonymous join is enabled. Depending on organizational need, if both external access and anonymous join need to be blocked— neither required nor recommended by this baseline—external collaborators would only be able to attend meetings if added as a B2B guest user. External access may be granted on a per-domain basis. This may be desirable in some cases, e.g., for agency-to-agency collaboration

3. Only Allow Approved Apps
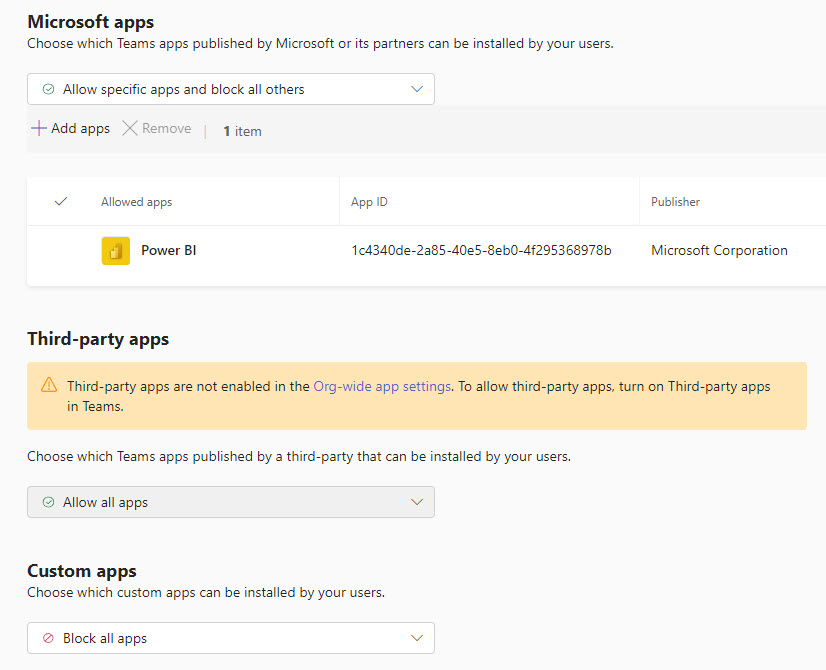
Teams can integrate with the following classes of apps:
- Microsoft apps: apps published by Microsoft.
- Third-party apps: apps not authored by Microsoft, published to the Teams store.
- Custom apps: apps not published to the Teams store, such as apps under development, that users “sideload” into Teams
Only authorized and approved applications should be available to end-users to manage exfiltration of corporate data. Additionally, unmanaged applications may have certain vulnerabilities that exploit users, devices, or data.


4. Create DLP Policies
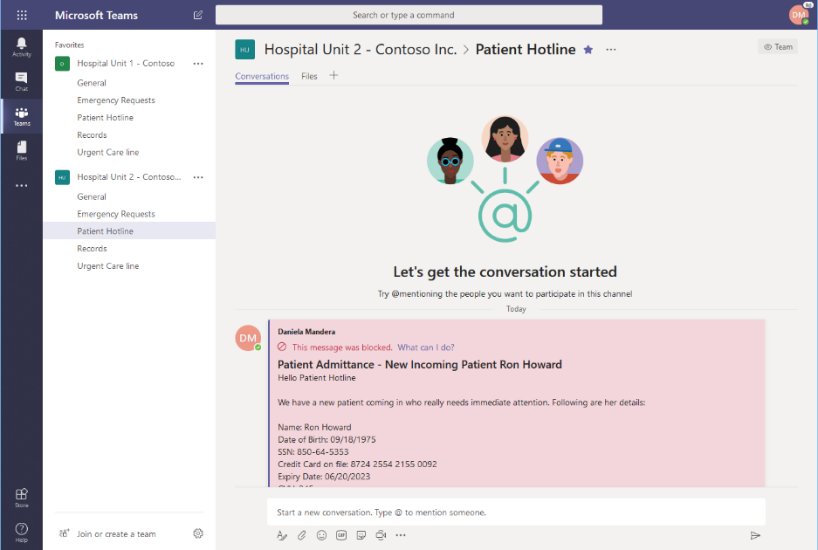
Data loss prevention (DLP) helps prevent both accidental leakage of sensitive information as well as intentional exfiltration of data. DLP forms an integral part of securing Microsoft Teams. By creating DLP policies scoped to Teams, you can prevent the sharing of sensitive information or PII such as Credit Cards, SSN, Bank Account info, etc.


5. Restrict Teams Creation
Users within a tenant have the ability to create a public or private Team by default. Behind the scenes, creating a Team also creates a Microsoft 365 or Office 365 Group and a SharePoint site with a document library that stores all documents shared within Teams channels. Over time, if this is not managed, the environment could quickly get out of hand with the number of Teams being created. This could lead to data loss, insecure sharing of documentation, and overall confusion across the organization. We recommend limiting the creation of Teams channels to certain members within the organization and creating a formal request process for new channels. To configure this setting, you will be restricting access for who can create a group as that is the backend to a Teams channel.


6. Restrict Automatic Meeting Admittance
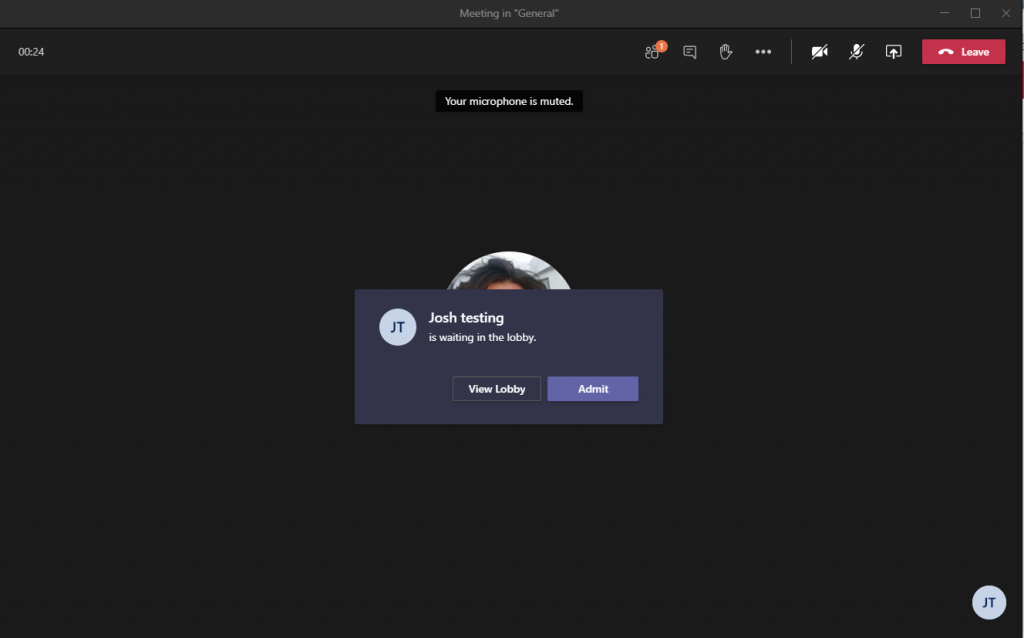
This setting controls which meeting participants wait in the lobby before they are admitted to the meeting. Anonymous users, including dial-in users, SHOULD not be admitted automatically.


7. Enforce Safe Links and Safe Attachments
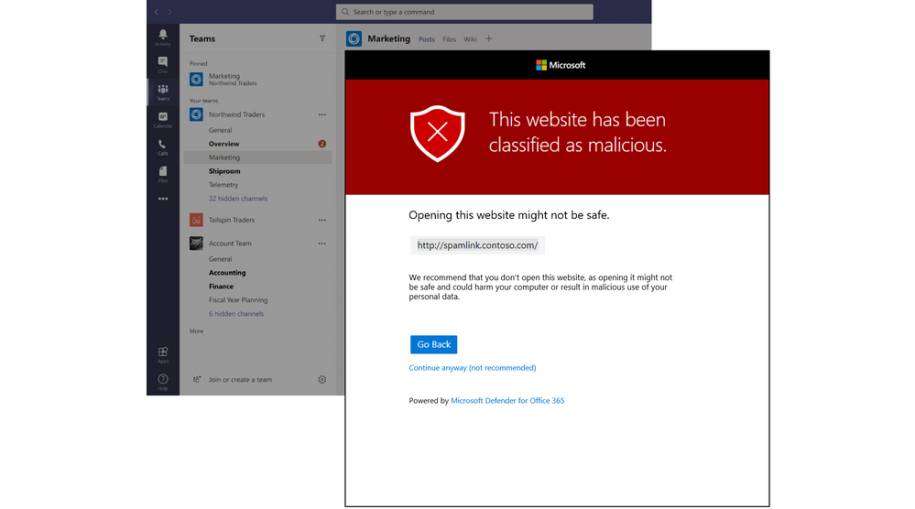
Safe attachment protection policies from Defender for Office 365 should be enabled and configured for Teams. Attachments should be scanned in a sandbox for malware upon opening or downloading.
Microsoft Defender protects users from malicious links included in Teams messages by prepending https://*.safelinks.protection.outlook.com/?url= to URLs included in the messages.
By prepending the safe links URL, Microsoft can proxy the initial URL through their scanning service. Their proxy performs the following checks:
- Compares the URL with a block list
- Compares the URL with a list of know malicious sites
- If the URL points to a downloadable file, applies real-time file scanning
If all checks pass, the user is redirected to the original URL.

8. Block 3rd party file storage
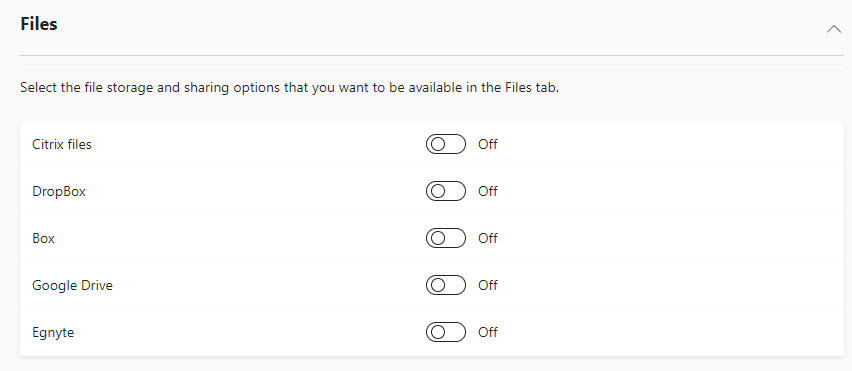
By default, users can add external third-party storage providers like Google and Drobox to their Teams channels for file storage. Only managed, trusted providers should be allowed for data loss prevention purposes.


Conclusion
In conclusion, implementing effective security measures in Microsoft Teams is crucial to safeguarding sensitive information and maintaining the privacy of your organization. Remember, security is a continuous process, and staying vigilant against evolving threats is paramount. By prioritizing security and implementing these best practices, you can confidently leverage Microsoft Teams as a powerful collaboration tool while keeping your data and communications safe.
