Microsoft Intune can be extremely powerful because of its MDM and MAM capabilities. Mobile Application Management (MAM) enables MSPs to securely protect corporate data on personal or BYOD devices without having to enroll in the full MDM solution. This is significant so that all administration is scoped only to devices that the company owns. For end-users, this is significant because devices like cell phone can still be used to access corporate data without fear of getting all data wiped remotely.
The autoenrollment settings chosen in Endpoint Manager, can significantly change if a user enrolled a device under just a MAM scope vs under a MDM scope. In this article, I will be breaking this down to bring clarity on best practices when configuring these settings.
Default Settings
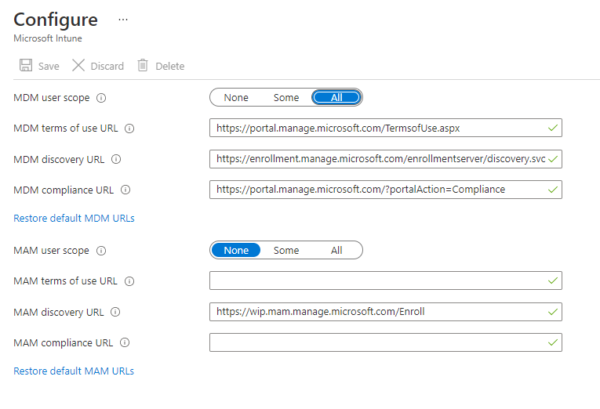
Out of the box on new tenants, the default settings have the MDM scope at all and the MAM scope at none. Some older tenants might have both Microsoft Intune and Microsoft Intune Enrollment under Mobility (Azure AD Admin Center). Make sure that your auto-enrollment settings are configured under Microsoft Intune instead of Microsoft Intune Enrollment.
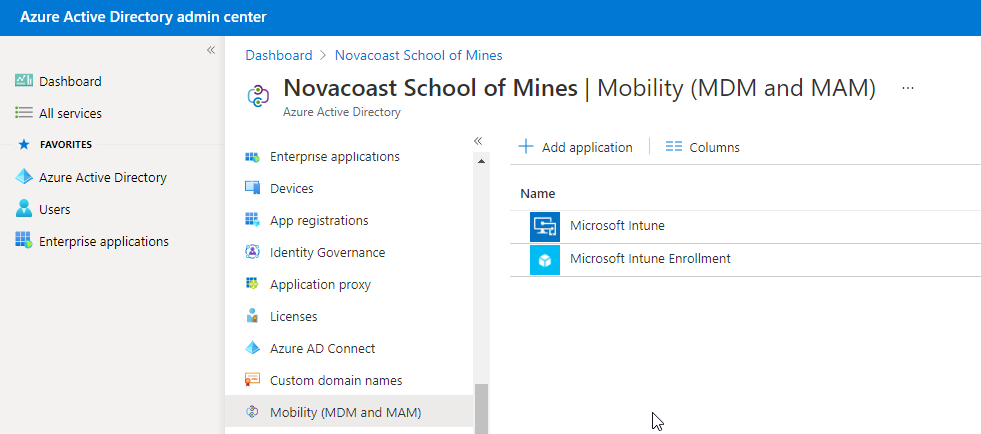
So what exactly do these default settings mean? Essentially this configuration is saying that any time any user enrolls their device (whether or not it is corporate or personal) they will always be enrolling into the full MDM solution. This means you have full control over that device, with all of the following features:
- Remote Wipe Capabilities
- Policy Configuration
- Patch Management
- Device Restrictions
- App Deployment
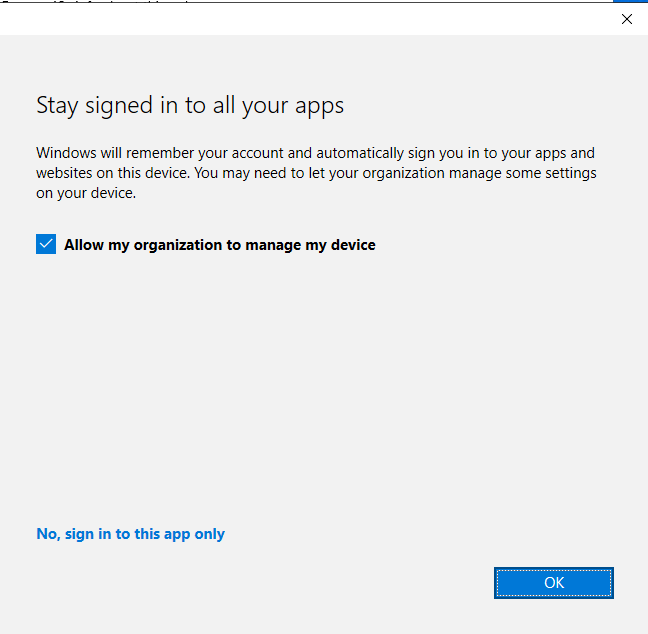
The experience for Android and iOS users is slightly different. They would be redirected to the app store to download the company portal app to enroll in the MDM solution.
This is all great in theory and ensures that all devices touching corporate data are under management. Do we really want that though? You are going to get end users who do NOT want their cell phones under management and I strongly encourage you to only manage devices that are corporate owned. This is where MAM policies come into play which we will look at next. First though, I think it’s important to uncover how devices get classified as Corporate or Personal.
Corporate vs Personal Devices
Corporate vs personal labeling in Microsoft Intune ultimately decides which enrollment scope (MDM or MAM) a user will get if you have both scopes set to all. There is tons of information from Microsoft about how devices get classified but at the highest level for MSPs, I like to think of it as follows:
Corporate Devices =
- Devices enrolled via a program (Autopilot, DEM, ADE)
- Hybrid Joined Devices enrolled via GPO
- Azure AD Joined Devices
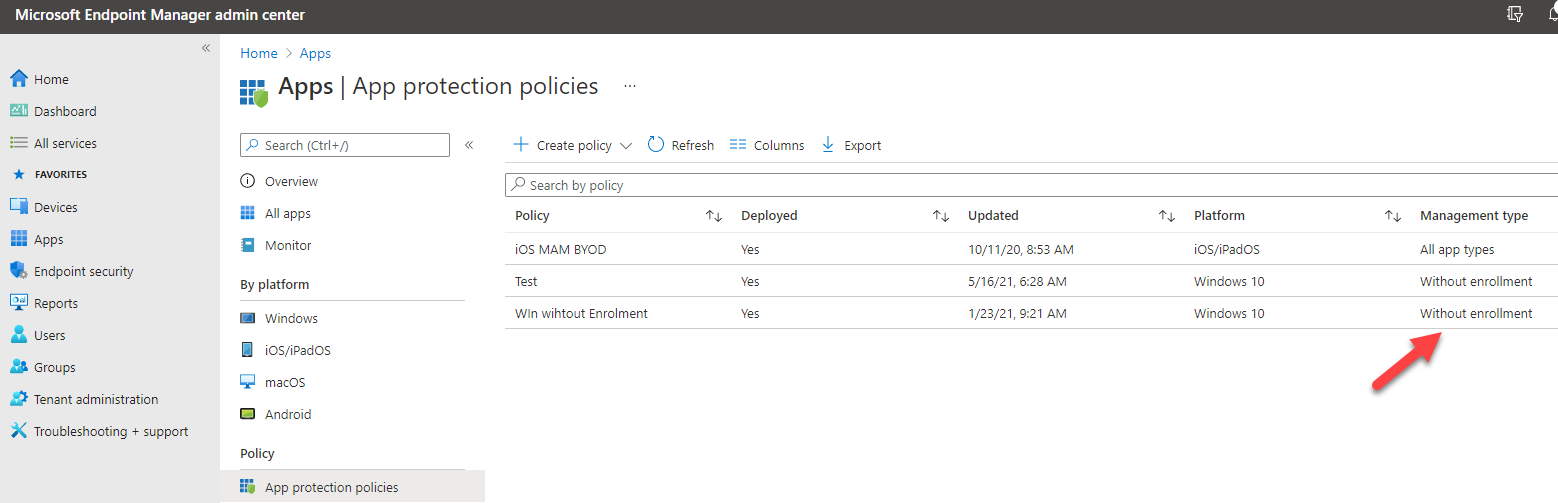
All other devices come in as personal. If you want to have personal devices protected with MAM, you need to create App protection policies for all platforms you want to support. These are also known as Windows Information Protection (WIP) policies (for Windows devices). These policies allow you to prevent cut, copy, paste and save as permissions to non-managed applications. For iOS and Android, you can additionally put extra security in place such as a pin to access corporate applications (like Teams).
Key Takeaway
Once these concepts are understood, you are better prepared to rollout Intune to your customer environments. For remote workers, you may need to enroll their existing laptops using just the MDM scope and then use Autopilot for all future devices that are procured. I hope this article provided some guidance on the autoenrollment settings in Endpoint manager. Please feel free to post and questions or comments below.
