Protecting corporate data on unmanaged devices like personal cell phones is extremely important in today’s remote workforce. App protection policies that are part of Microsoft Intune provide an easy way to start containerizing corporate data without inhibiting user productivity. It also provides flexibility so that the device does not need to be unenrolled in a management solution. In this article, I will be breaking down the high level components of App protection policies and show some of the end user experience.
Main Goals

- Do not let corporate data reside in untrusted or unmanaged locations
- Provide end-to-end compliance in the case of a lost or stolen device
- Provide access to corporate data with restrictions on sharing
Configuring Policies
1. Sign into Endpoint Manager Admin Center
2. Apps>App Protection Policies>Create Policy
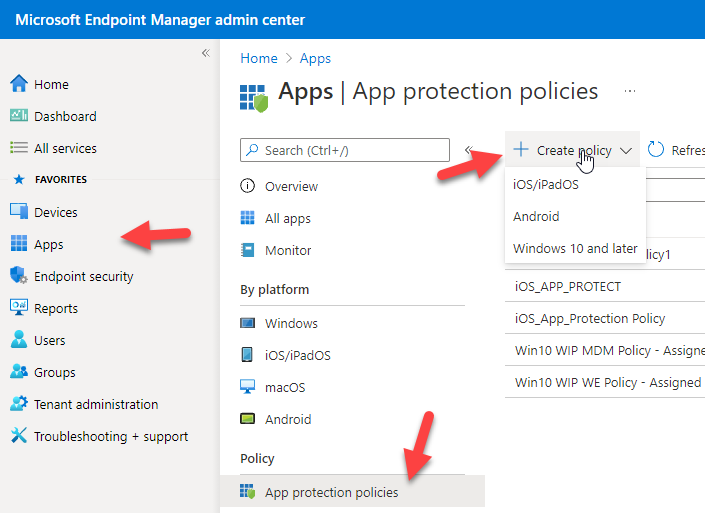
In this example, I will walk through setting up an App protection policy for iOS. Android policies mirror iOS with a few obvious differences native to the OS nomenclature.
3. Provide a name
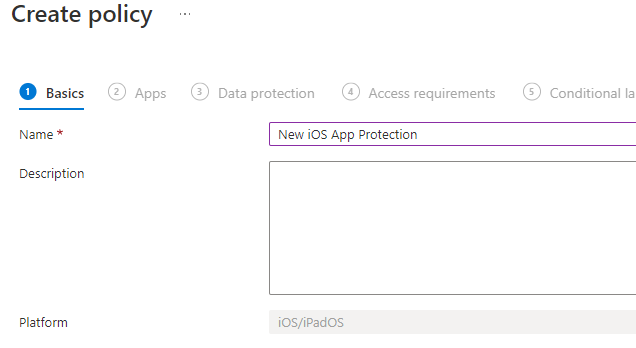
4. Under the apps section, for device types, you can choose to have this policy apply to both managed and unmanaged devices. It may be that you have two different policies with the one for unmanaged devices being more restrictive. In this example I am going to scope this to unmanaged devices.
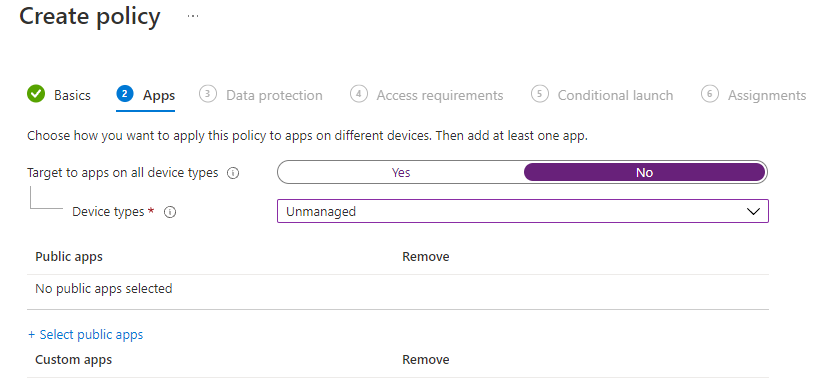
5. Click on +Select Public Apps. This is where you can decide what apps are sanctioned (trusted) in your org. Microsoft has a preset library and I would recommend at least including the basic office suite. These are the apps you are saying are managed and can then provide further protection on like restricting cut/copy/paste or save as permissions. Custom Apps can also be uploaded as well for further protection outside of Microsoft offerings.
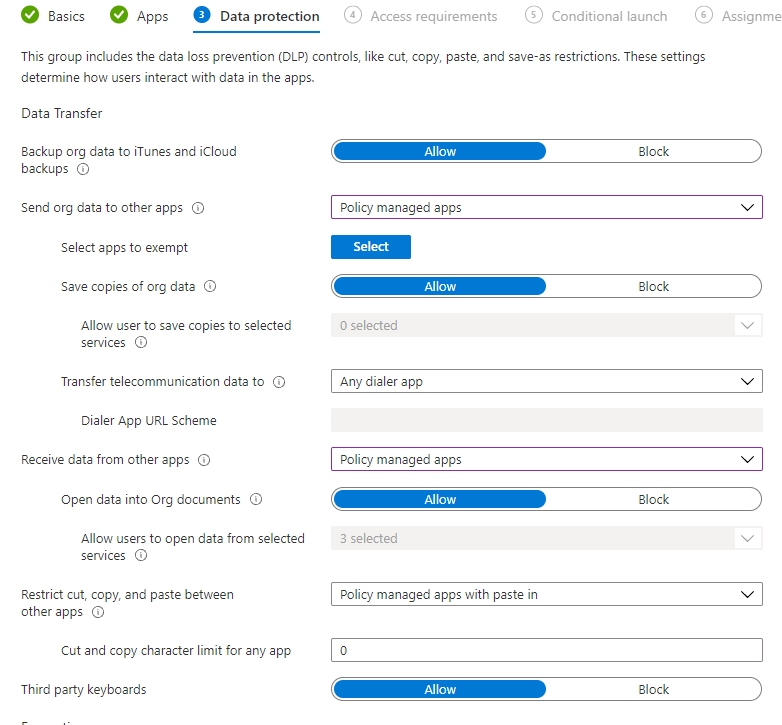
6. In the Data Protection section, you can define all of your security settings for managed apps. I won’t be covering all of these in depth but just note that you would want to restrict these permissions to other policy managed apps like you see below:
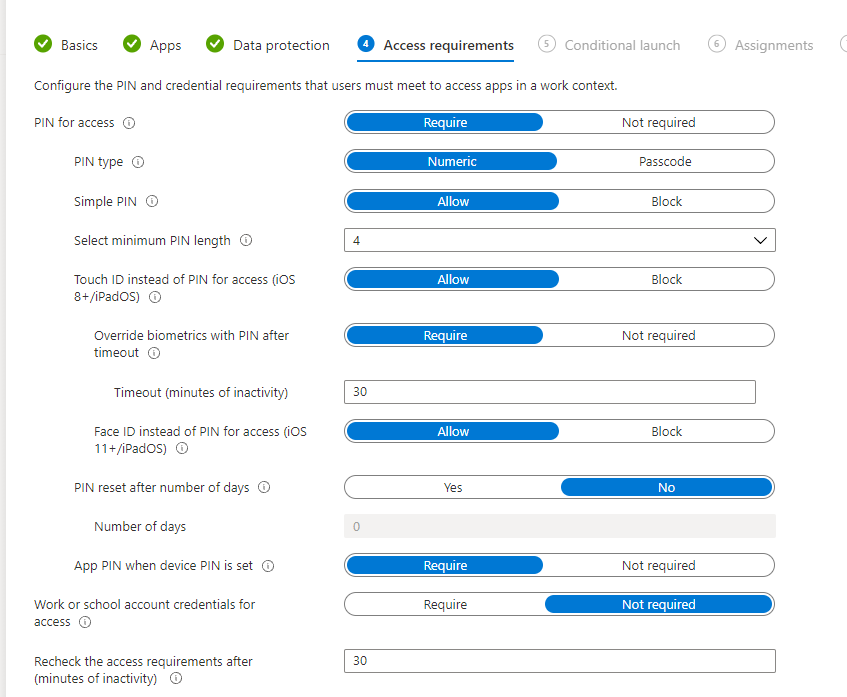
7. Access Requirements allow you do define security settings like a pin or additional login at the application level. This way if a device is stolen or broken into, there is a further layer of protection against corporate data.
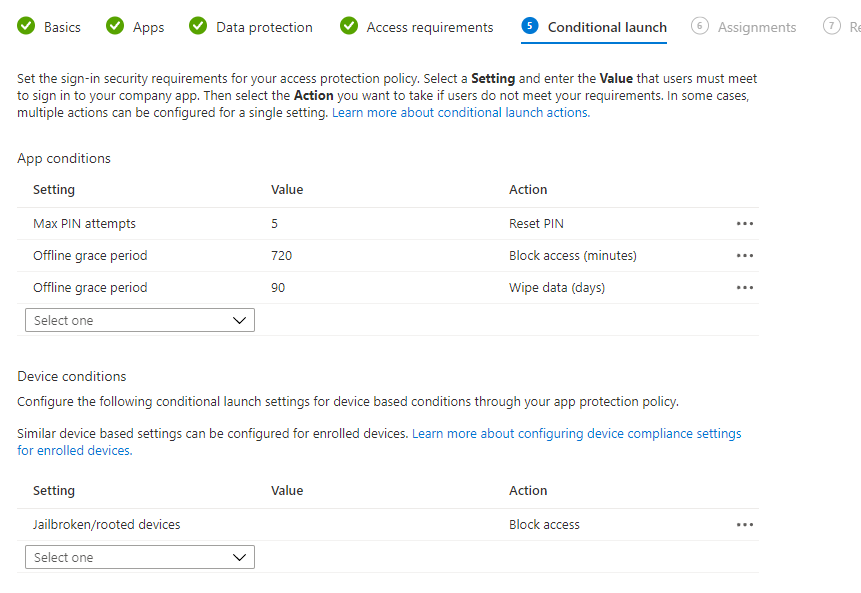
8. The conditional launch section is basically if then statements that you are declaring if a device reaches a certain state.
10. The final tabs just let you scope this policy to certain users or groups. This policy will begin to take effect immediately and users accessing these apps on an iOS devices will be told the the data is being protected. On that note, let’s walk through some of the end-user experience.
End User Experience
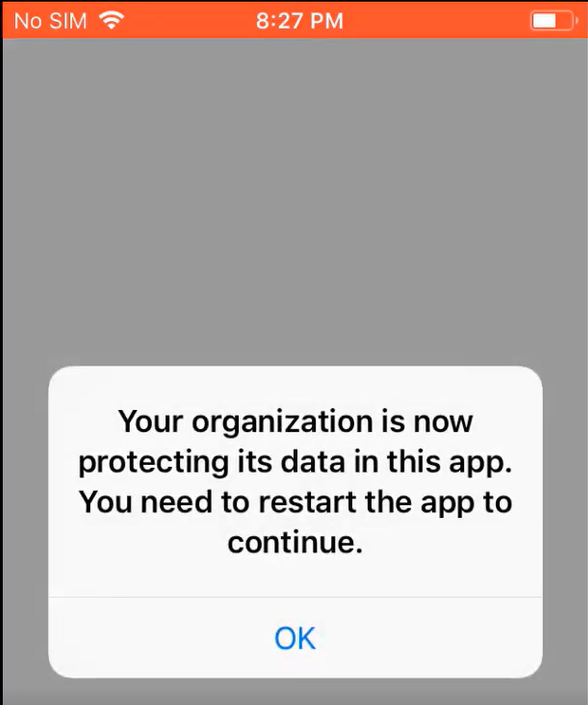
When a user signs into one of your protected apps like outlook for instance, they will get a prompt about the org protecting data:
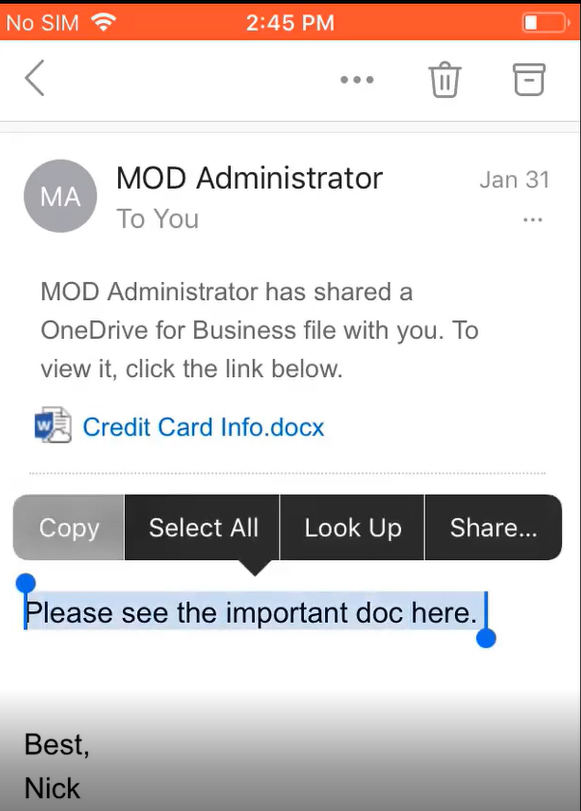
Cut, Copy, Paste Restrictions to unmanaged applications. Example here trying to copy email message to notepad:
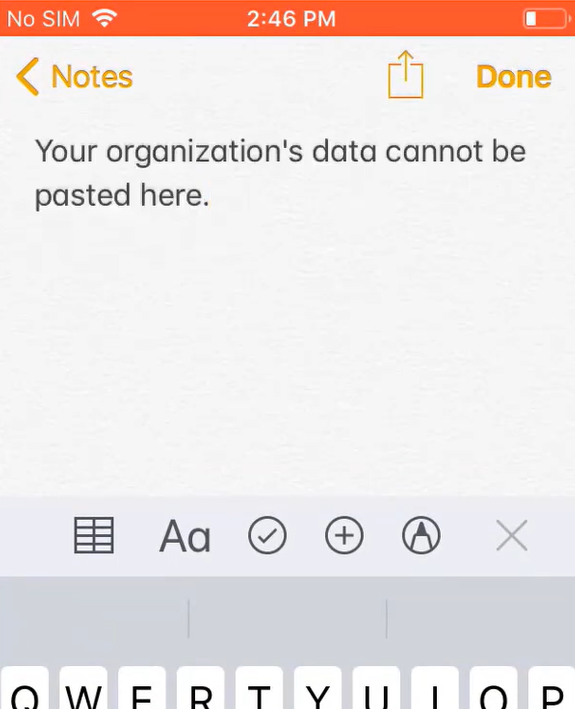
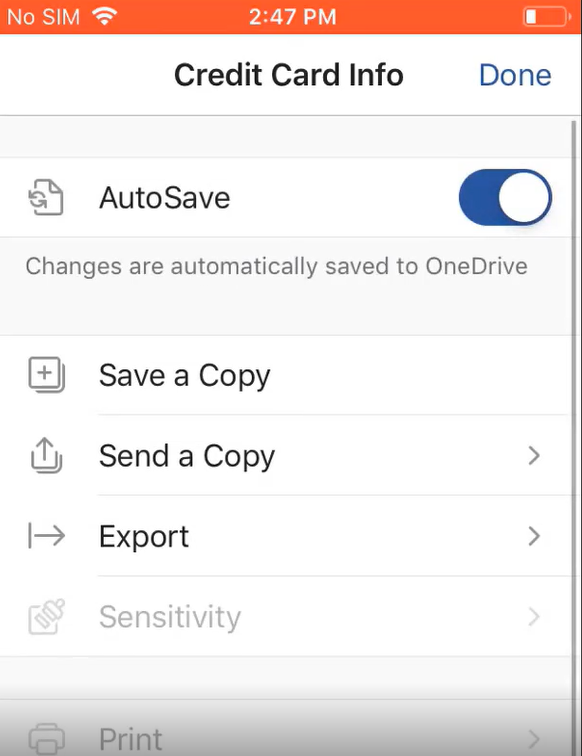
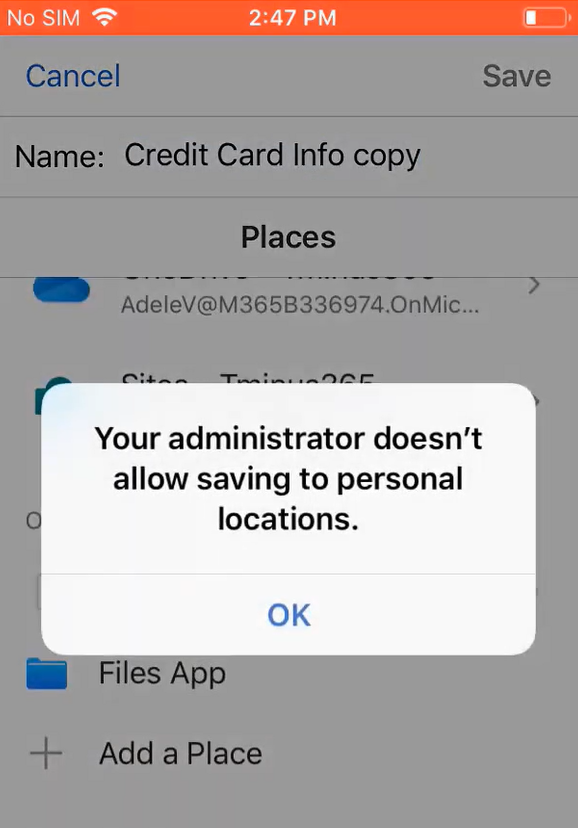
Save as permissions are limited as well. Example here trying to save a word doc to a personal location on an iOS Device
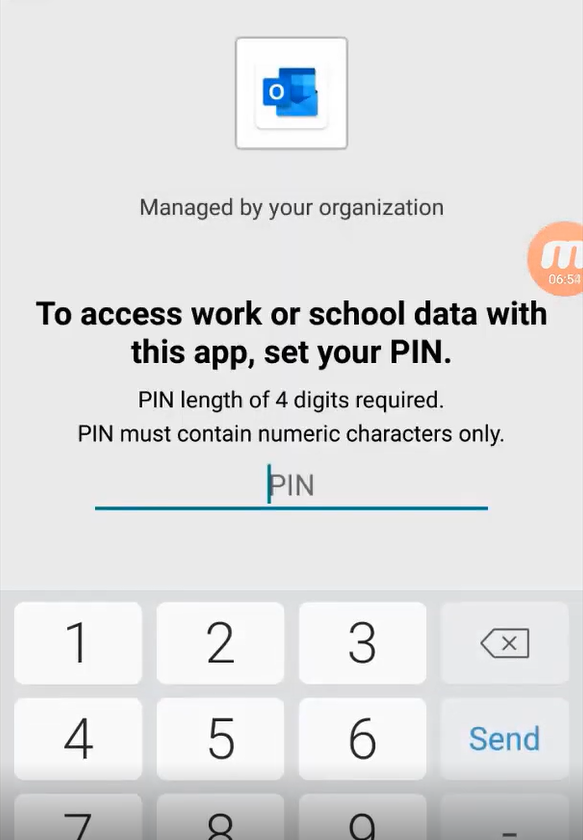
Finally, if you put in additional access controls such as a pin, the user will be asked to establish this pin when accessing a managed application for the first time after policy creation
Conclusion
I hope this article provided more targeted insight into app protection policies with Microsoft Intune. These policies require light administrative work to set up and can greatly increase the protection of corporate data on unmanaged devices. Please leave any questions or comments below!
