We can leverage logic apps in Azure to build workflows across our 365 customers. This allows us to create triggers that cause other actions to take place. Recently, Microsoft introduced the Microsoft Graph API to our list of apps we can connect to. In this article we will primarily be focusing on the security components of the API.
The Microsoft Graph Security API connects multiple security solutions to enable easier correlation of alerts, provide access to rich contextual information, simplify automations and investigations. Here are some of the benefits to MSPs for when using Microsoft Graph:
- Streamlined integration with security operations tools, workflows, and reporting.
- Security alerts spanning across both Microsoft 365 and Azure
- Reduced deployment and maintenance time and efforts.
- Automated response to alerts by taking action on threats.
- Ability to deliver more value to customers.
- Real-time alerts in Microsoft Teams
In this article, I will be showing the steps for creating a new Logic App that post security alerts across M365 and Azure to a teams channel.
Key Factors
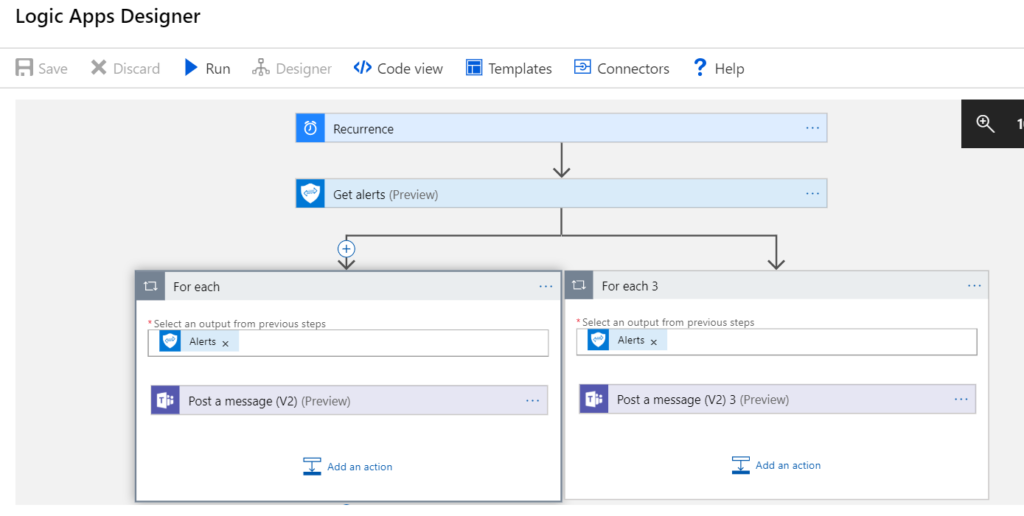
With the app you are basically selecting triggers for workflows to occur. In the above diagram I created a trigger that occurs every 15 minutes which pulls security alerts from the Microsoft graph and writes them in a Teams channel I designate. Through my testing, if you use the 15min interval for a trigger, you will be spending about $1/day. Here are some key factors with the Logic App
Money
As i mentioned above, you will accumulate charges for the # of recurrences you set but it’s not that much per month. You can do this for free by creating a powershell webhook. I have a complete guide you can checkout here
WorkFlows
.
Easy to configure workflows across both internal and external applications(external apps cost more)
Configuration
The output is not as configurable as I would like. It comes over as one blob of info rather than concise line items
Limitless Potential for Automation
You are able to easily build on top of the existing configuration. An example would be getting an email notification at the end of the day of all the alerts that occurred.
Configuration Steps
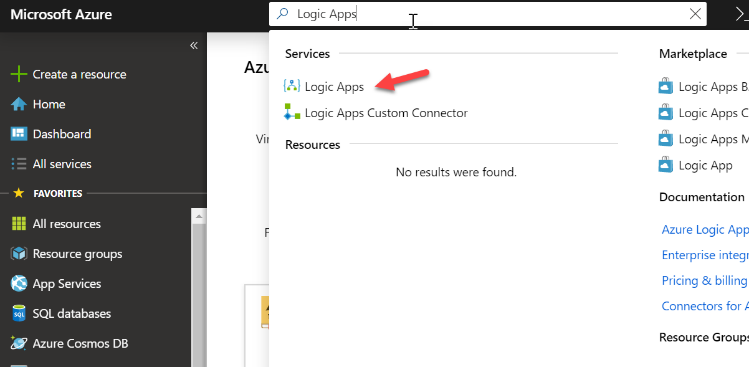
Add the App
Sign-in to https://portal.azure.com with a global admin and search for Logic Apps
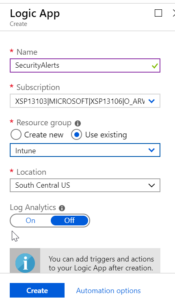
Customize Settings
Click Add and then customize your settings
Select Recurrence
After the app is created, scroll down and select Recurrence to start the design
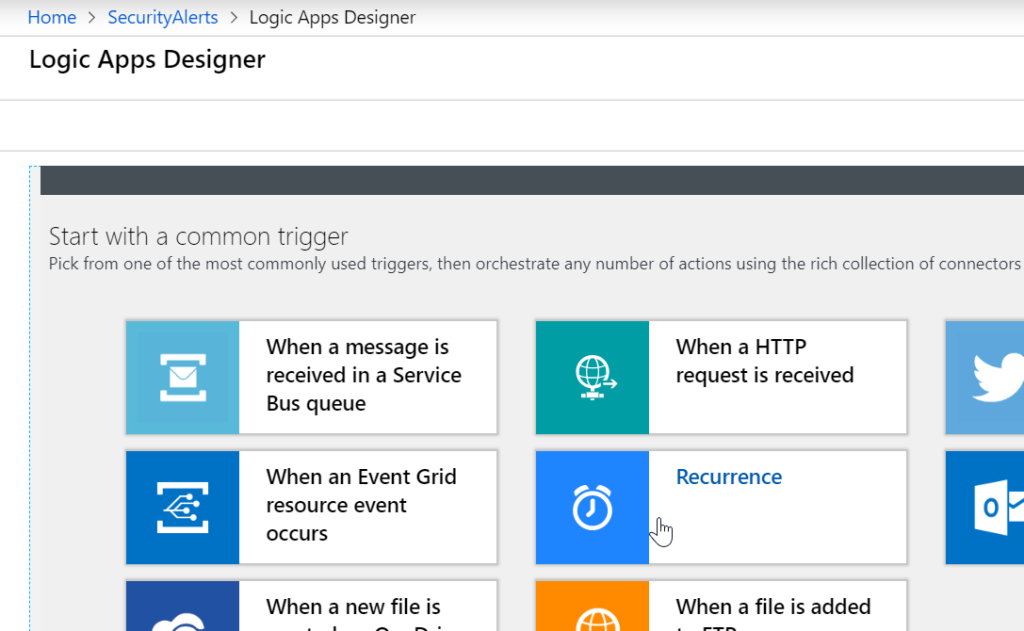
Select Trigger Time frame
Here you can add a custom time frame. I will be selecting 15 minutes. Click New step after
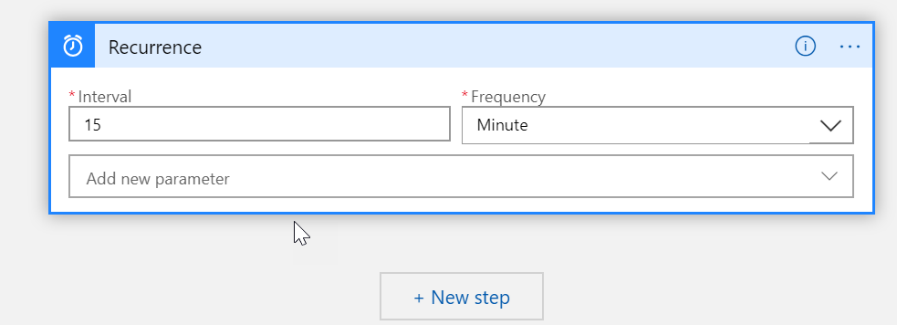
Microsoft Graph
Search for Microsoft Graph and then select Get Alerts after the you click on the icon

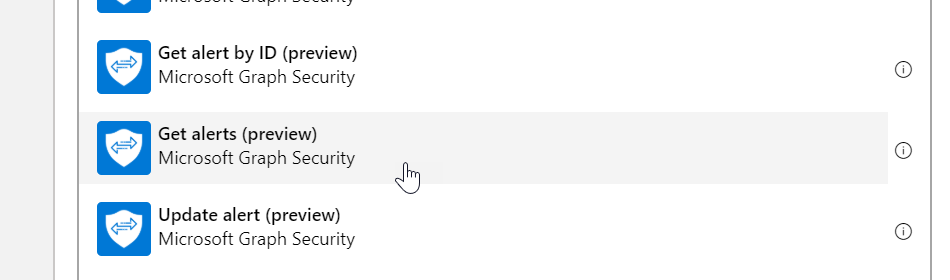
Choose Top Alerts
Click on the Add Parameter button and select top alerts. **NOTE** here you could select the filter alerts as well if you only want to see a certain severity level such as High
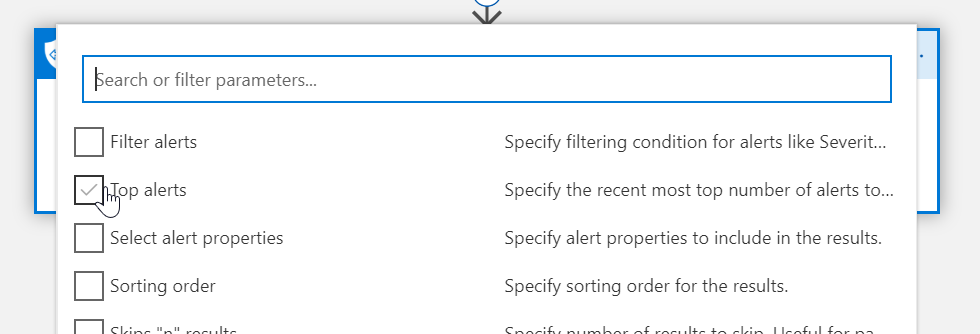
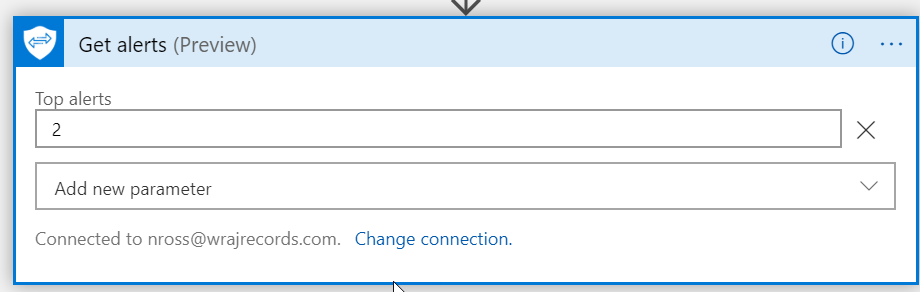
Choose # of Alerts
After you select Top Alerts, enter the number of them you want to see. I will only want to see the top 2 since its running every 15 minutes
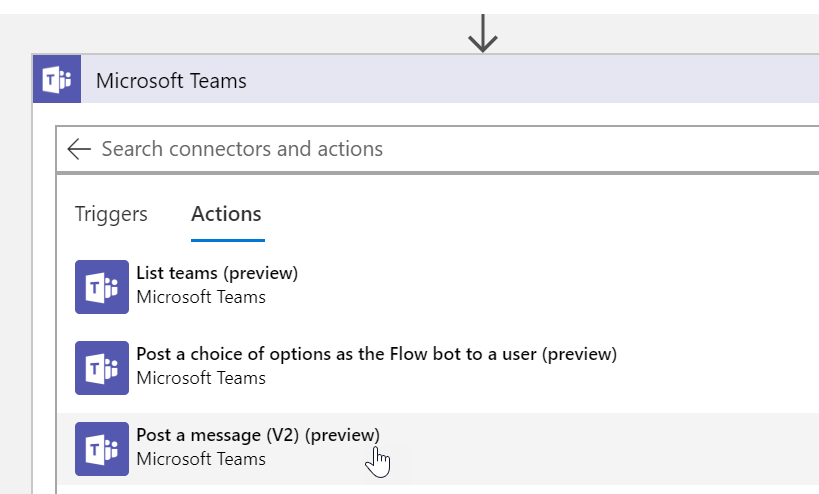
Add Teams
Click New Step and Search for Microsoft Teams. After you select it, choose to Post new message

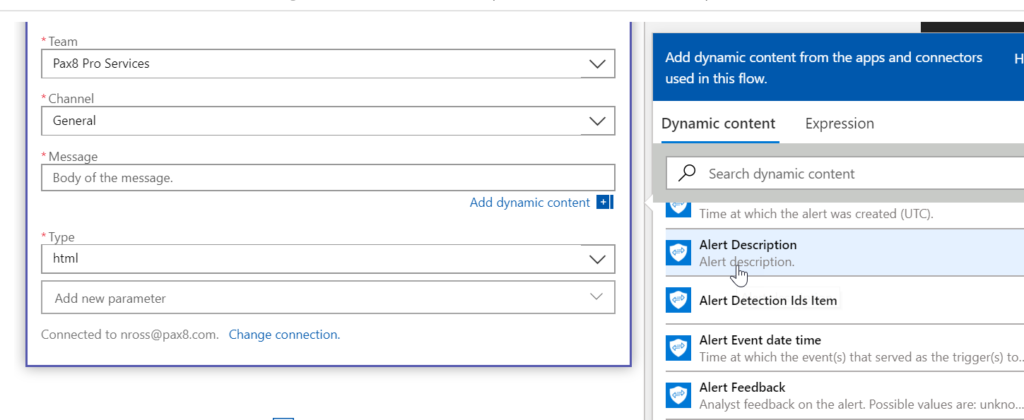
Add Variables
Add your teams channel and in the message field, we can choose what variables we want to see. I typically select Title, Description, Severity, EventDateTime, and RecommendedActions.
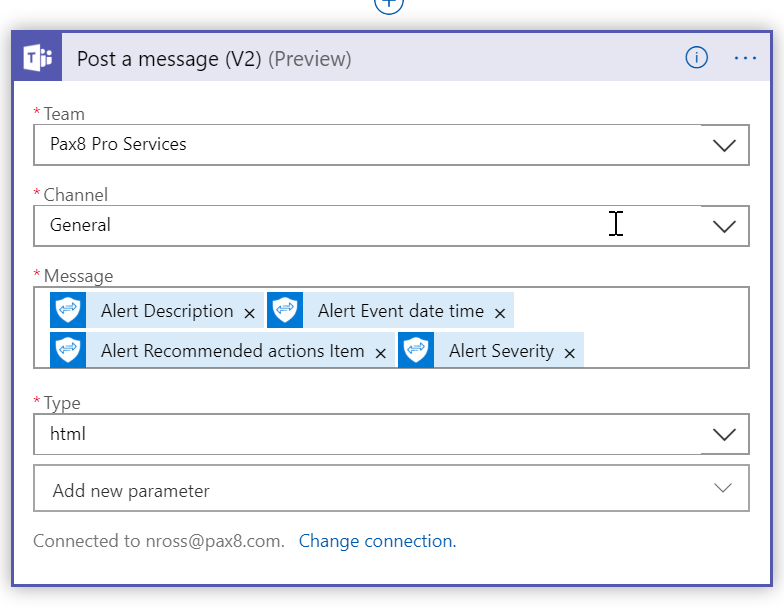
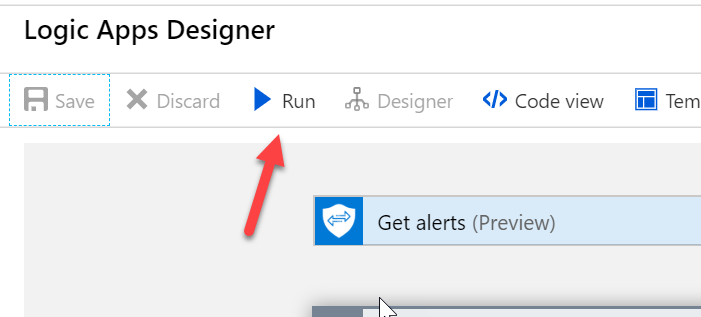
Run the Task
After you are done, you can select Save>Run to see it in action. View the message in your Teams channel
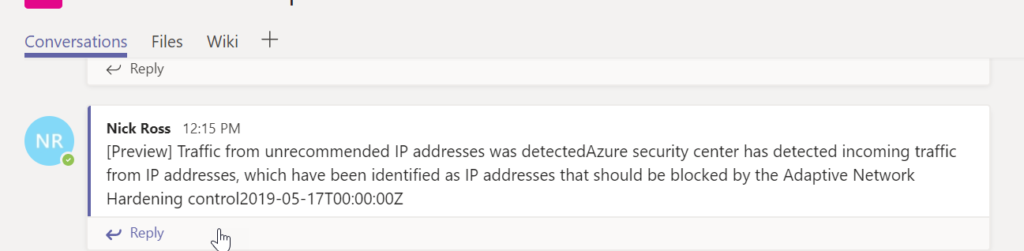
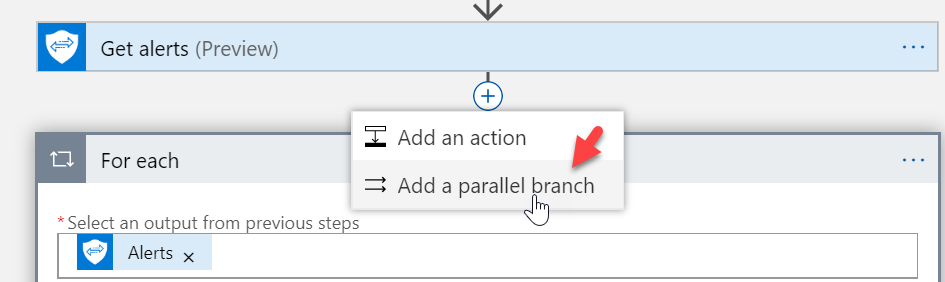
Separate into different Branch
As I mentioned before, it comes across a little jumbled so you may want to add a parallel branch after the Microsoft Graph title to separate things into different messages
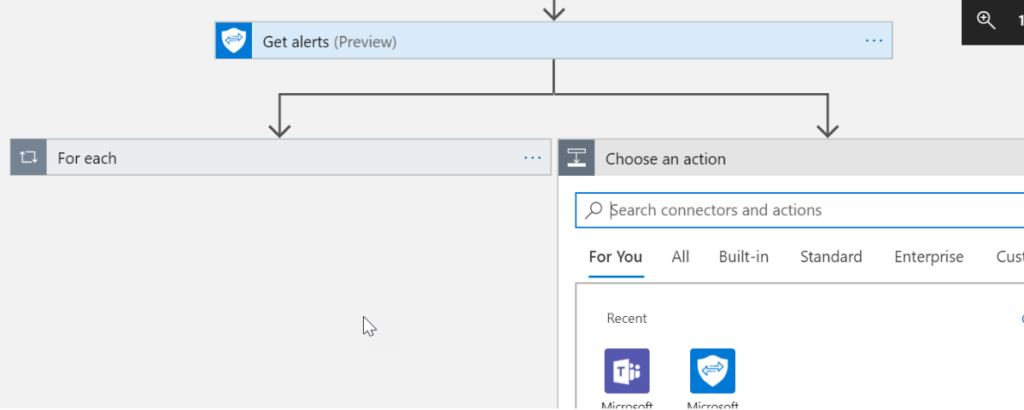
Experiment
- I recommend playing around with the other apps available at no additional charge. You can continue the flow of the diagram if you want addition actions to take place. The below example is extended to outlook to get an email message. An example of this flow would be that we make the recurrence once a day. It populates the message in teams of the alerts that happened that day as well as give us a summary email: