Below you will find a list of security controls for Microsoft Intune that will help secure your environment. Keep in mind these are recommendations and will not be able to be used in all environments due to unique constraints. Each control should be evaluated and tested appropriately. I have also written security baselines across the Microsoft Suite offerings (Azure AD, Teams, Exchange, SharePoint, OneDrive, Intune) and mapped them to CIS Controls. If you would be interested in seeing this content, check out this post.
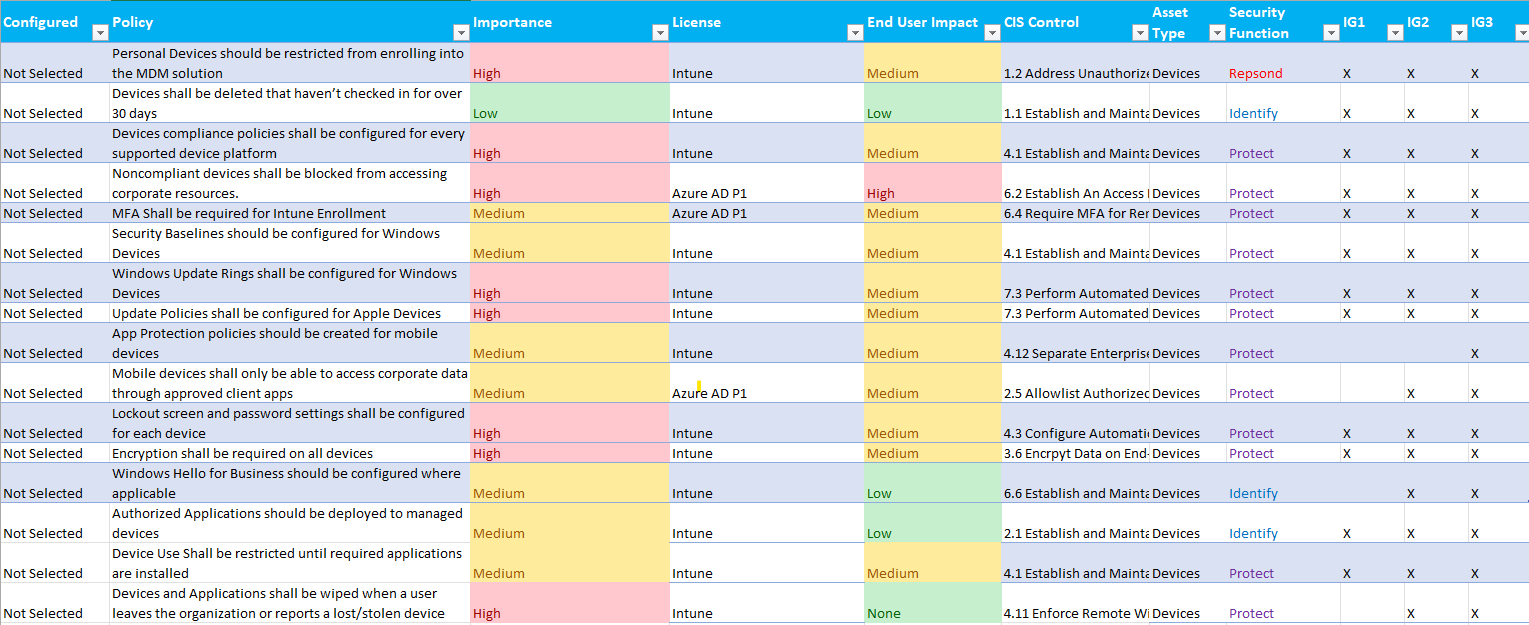
Matrix: Intune Baselines v1.xlsx
1. Personal Devices should be restricted from enrolling into the MDM solution
By default, any device can enroll into Intune whether or not it is classified as corporate or personal. To prevent device users from accidently enrolling their personal device, device restrictions should be configured. Users should only be enrolling corporate owned devices that have specifications that meet corporate standards.
Policy
- Device restrictions should be configured to restrict personal devices from enrolling in the MDM solution
- Only device types (i.e. Windows, Linux, macOS, etc.) defined by the corporation shall be supported for Intune enrollment
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Overview of enrollment restrictions – Microsoft Intune | Microsoft Learn
Create device platform restrictions – Microsoft Intune | Microsoft Learn
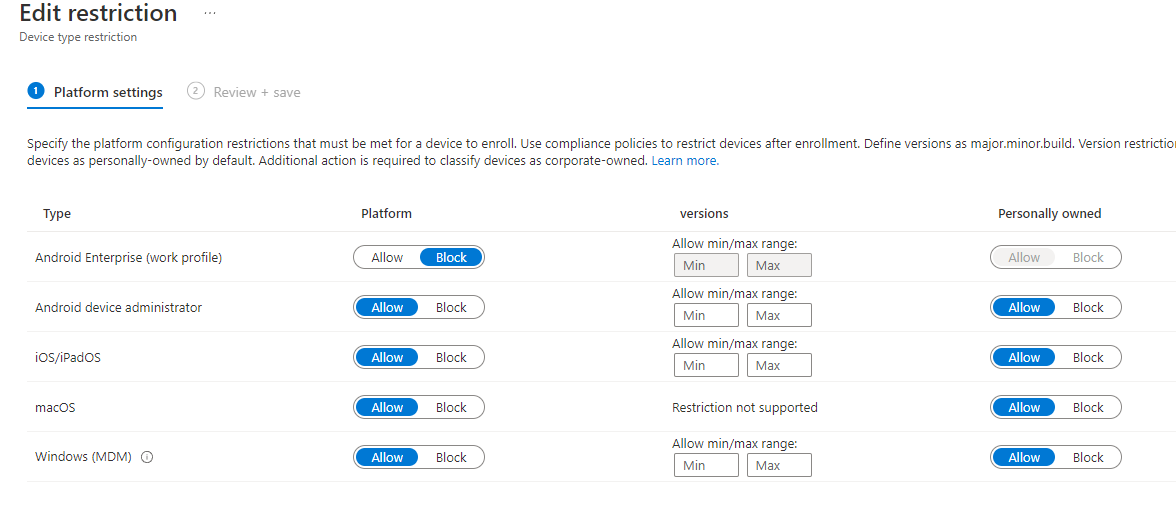
To block personally owned devices from enrolling into Intune:
- Follow the steps outlined here
- Under Personally-Owned, select Block for each device type
End-User Impact
Level: Medium
Users will not be able to enroll any device that is classified as personal. If you have Windows autoenrollment enabled, users will be prompted to enroll their devices when access common office applications like Teams. If they select Yes to enroll the device and the device is personally owned, they will be prevented from enrolling that device.
PowerShell Scripts
Videos
MIH07 – Setup your Microsoft Intune Tenant – Enrolment restrictions and device settings – YouTube
CIS Control

2. Devices shall be deleted that haven’t checked in for over 30 days
By default, no devices are removed from Intune no matter the level of inactivity. In order to ensure an inventory of active authorized devices, device clean-up rules should be configured to automatically delete devices that have not checked in for over 30 days.
Policy
Devices are deleted from Intune if they have not checked in for over 30 days
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Overview of enrollment restrictions – Microsoft Intune | Microsoft Learn
Create device platform restrictions – Microsoft Intune | Microsoft Learn
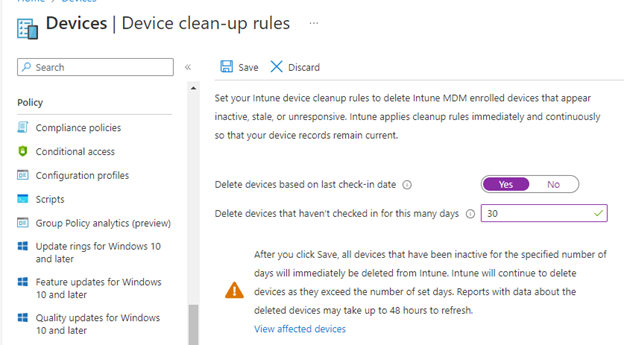
To set the device clean-up rule:
- Go to the Intune Admin Center
- Click on Devices
- Scroll down to Other and select Device Clean-up rules
- Select Yes for the first option
- Set the time period to 30 days
- Click Save
End-User Impact
Level: Low
If users have a device that does no check in for over 30 days it would be removed from Intune. Devices can be recovered if someone were to take an extended leave for up to 180 days.
Tips
If you are leveraging Intune as a source of truth for your asset inventory, you may want to change this setting to 60 or 90 days so that devices are not removed as quickly. This would give you more time to identify stale devices and take the proper action to reissue or retire the device.
PowerShell Scripts
Microsoft Intune: Device Cleanup rules | Neeraj Kumar
Videos
How to Setup Automatic Device Cleanup Rule in Intune – YouTube
CIS Controls
3. Devices compliance policies shall be configured for every supported device platform
Device compliance policies allow us to define the necessary settings on a particular platform that meets corporate requirements. Device compliance policies paired with conditional access policies allow us to prevent access to corporate resources on noncompliant devices. Devices should be constantly monitored to ensure compliance with corporate policies.
Policy
- A device compliance policy is configured for each device platform that is supported by the corporation.
- Devices that do not meet the compliance standards shall be marked as noncompliant immediately
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Device compliance policies in Microsoft Intune | Microsoft Learn
To configure device compliance policies by platform:
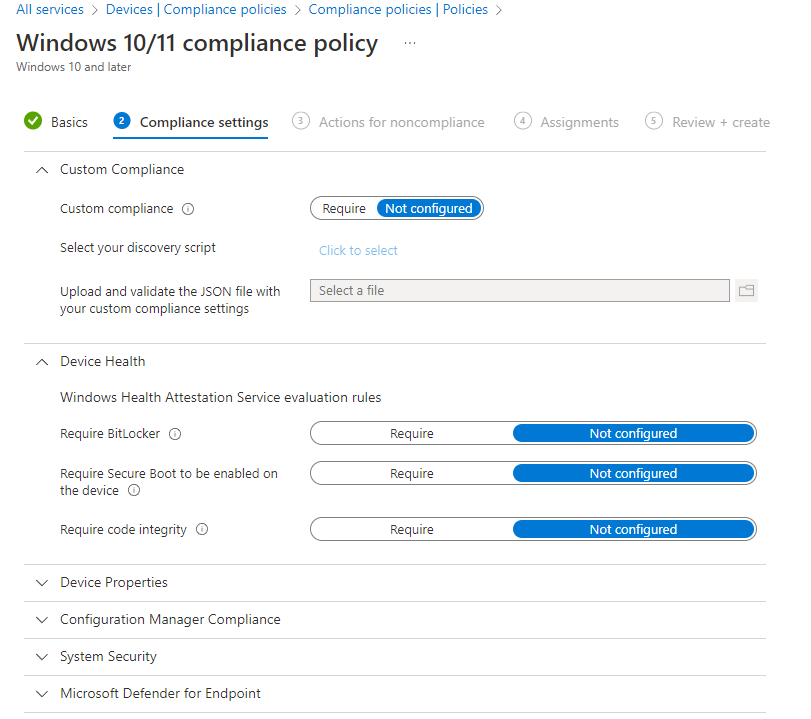
End-User Impact
Level: Medium
Device compliance policies will have no impact to end-users unless they are paired with conditional access policies to block access on noncompliant devices. Devices not in compliance will show up in the Intune admin center from a reporting standpoint. There are certain device compliance policy settings that will prompt the end-user for certain action. For instance, configuring Encryption of data storage on the device will prompt the user to configure Bitlocker encryption if it is not already enabled. It is recommended to push out a configuration profile to automatically configure encryption in this use case to avoid help desk calls.
Tips
Device compliance policy settings might vary depending on the organization but should be standardized where possible.
PowerShell Scripts
Videos
- iOS Device Compliance Policy Intune – YouTube
- Windows 10 Compliance Policy Intune – YouTube
- S04E08 – Custom Compliance policies (I.T) – YouTube

4. Noncompliant devices shall be blocked from accessing corporate resources.
Device compliance policies allow us to define the necessary settings on a particular platform that meets corporate requirements. Device compliance policies paired with conditional access policies allow us to prevent access to corporate resources on noncompliant devices. Devices that are not in compliance should not have access to corporate resources.
Policy
Noncompliant devices shall not be able to access corporate resources
Licensing Considerations
This setting requires at least an Azure AD P1 license which comes standalone or as part of the following bundles:
- EMS+E3/E5
- Microsoft 365 Business Premium
- Microsoft 365 E3
- Microsoft 365 E5
Set-Up Instructions
Device compliance policies in Microsoft Intune | Microsoft Learn
To configure a conditional access policy for compliant devices:
- Follow the steps outlined here to create a conditional access policy
- Under the assignments section, Include all users. Be sure to Exclude a break-glass account to ensure you never lock yourself out.
- Under the Cloud Apps section, include all cloud apps
- Do not configure anything in the conditions section
- Under the Grant section, choose Require device to be marked as compliant
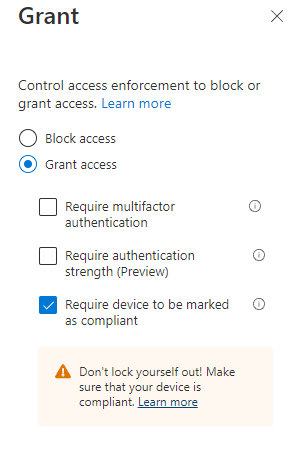
End-User Impact
Level: High
Any user that is trying to access corporate data on a device not marked as compliant shall receive a message letting them know they are blocked and will be told to contact IT. This includes both devices enrolled into Intune and marked as noncompliant as well as devices that are not enrolled at all into the solution.
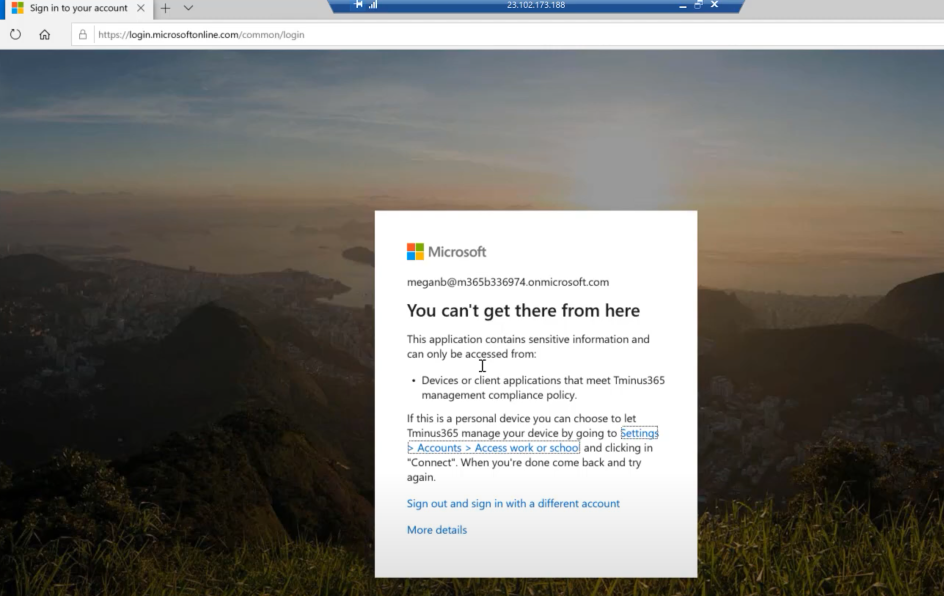
Tips
- A formal process definition should be in place for investigating noncompliant devices. Common use cases for noncompliant triggers should be documented to expedite resolution
- Automation should be put in place where possible to alert on noncompliant devices in order to be more proactive.
- Users should have way to readily contact support that is not through email as they will not have access to enter outlook
PowerShell Scripts
Videos
Preventing Access on Noncompliant Devices – YouTube
CIS Controls
5. MFA Shall be required for Intune Enrollment
You can use Intune together with Azure Active Directory (Azure AD) conditional access policies to require multifactor authentication (MFA) during device enrollment. If you require MFA, employees and students wanting to enroll devices must first authenticate with a second device and two forms of credentials. We do not want unauthorized users joining devices to our network.
Policy
MFA Shall be required to enroll devices into Intune
Licensing Considerations
This setting requires at least an Azure AD P1 license which comes standalone or as part of the following bundles:
- EMS+E3/E5
- Microsoft 365 Business Premium
- Microsoft 365 E3
- Microsoft 365 E5
Set-Up Instructions
Require multifactor authentication for Intune device enrollment – Microsoft Intune | Microsoft Learn
End-User Impact
Level: Medium
Users must satisfy the MFA prompt in order to be able to successfully enroll a device. For users signing in for the very first time who have not configured MFA methods, a temporary access pass can be used: Configure a Temporary Access Pass in Azure AD to register Passwordless authentication methods – Microsoft Entra | Microsoft Learn
Tips
For users signing in for the very first time who have not configured MFA methods, a temporary access pass can be used: Configure a Temporary Access Pass in Azure AD to register Passwordless authentication methods – Microsoft Entra | Microsoft Learn
PowerShell Scripts
Videos
Enabling MFA when Joining a Device to Azure AD – YouTube
CIS Controls

6. Security Baselines should be configured for Windows Devices
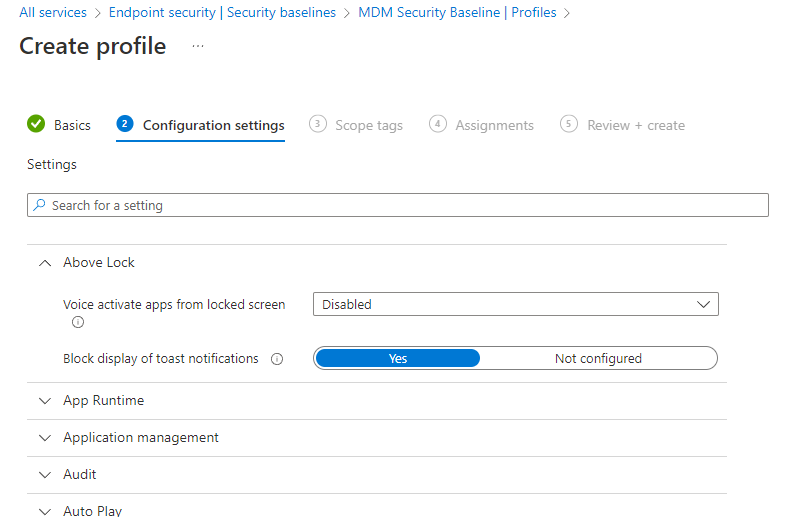
Security baselines in Intune are pre-configured groups of settings that are best practice recommendations from the relevant Microsoft security teams for the product. Intune supports security baselines for Windows 10/11 device settings, Microsoft Edge, Microsoft Defender for Endpoint Protection, and more.
You can use security baselines to rapidly deploy a best practice configuration of device and application settings to protect your users and devices. Security baselines are supported for devices that run Windows 10 version 1809 and later, and Windows 11. These baselines allow you to configure common security settings such as:
- Password Requirements
- Lock screen settings
- App Installation
Policy
Security Baselines should be configured for Windows Devices
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Require multifactor authentication for Intune device enrollment – Microsoft Intune | Microsoft Learn
End-User Impact
Level: Medium
Its possible that some of the settings pre-configured as part of the security baseline profile will be disruptive to end-users. As a best practice, proper testing should be done leveraging a device on the corporate network and testing this out with a pilot group of users before broad deployment.
Tips
Security baselines are one of several methods in Intune to configure settings on devices. When managing settings, it’s important to understand what other methods are in use in your environment that can configure your devices so you can avoid conflicts. See Avoid policy conflictslater in this article.
PowerShell Scripts
Creating Endpoint Security Policies with PowerShell | Powers Hell (powers-hell.com)
Videos
Microsoft Endpoint Manager: Security baselines – YouTube
Microsoft Endpoint Manager Intune Endpoint Protection Part IV Security Baselines – YouTube
CIS Controls

7. Windows Update Rings shall be configured for Windows Devices
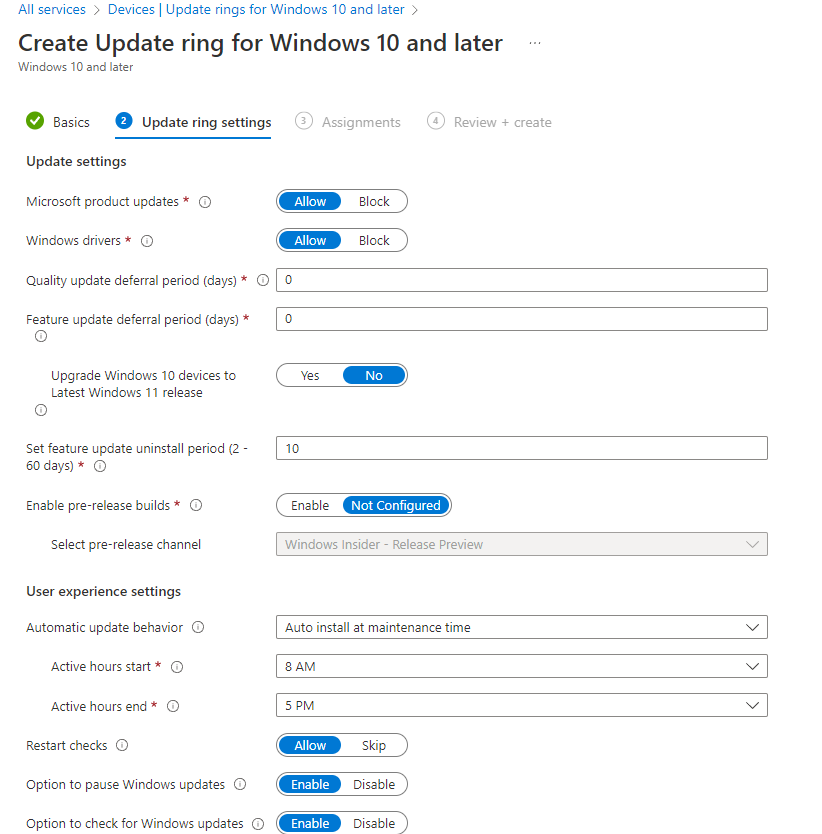
Windows update rings, also known as Windows Update for Business allow you to manage the patch cycle across Windows devices in your organization.
Updates should be staggered across devices in your organization in order to manage any new features or bugs as part of the new update. Critical updates should be deployed immediately to all devices leveraging the Windows update ring service.
If you are an enterprise customer, Windows Autopatch is another feature that can automate your deployment of Windows update rings.
Policy
Windows update rings are configured and assigned to all windows devices
Licensing Considerations
- Any tenant with Intune licensing can access this setting.
- OS Requirements: Configure Update rings for Windows 10 and later policy in Intune | Microsoft Learn
- Windows Autopatch Prerequisites: Prerequisites – Windows Deployment | Microsoft Learn
Set-Up Instructions
Configure Update rings for Windows 10 and later policy in Intune | Microsoft Learn
End-User Impact
Level: Medium-High
Patching has always been notorious for being disruptive to end-users. When you configure the Windows update rings, you can define specific time periods where updates will try to be deployed. This is typically in the after hours of business. You can also decide how long end-users can defer updates before they are forced to install them. There will always be use cases where you also have to uninstall updates due to those updates having bugs or disrupting some type of line of business application.
Tips
- Have a defined process in place for when you need to roll back updates or when you need to push out critical updates to all devices.
- In your broad deployment, make sure the quality or deferred updates are pushed out at least 14 days to avoid more frequent rollbacks.
PowerShell Scripts
Videos
- Windows Update Rings: https://www.youtube.com/watch?v=RKfDZeQL97w&t
- Automate Windows Patching | Microsoft Tutorial – YouTube

8. Update Policies shall be configured for Apple Devices
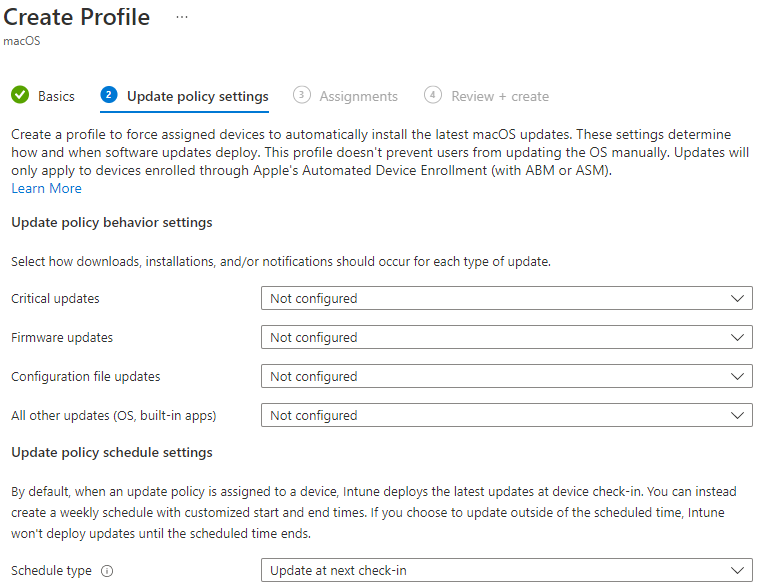
You can use Microsoft Intune to manage software updates for macOS, iOS, and iPad devices that enrolled as supervised devices. Just like the Windows update rings in the previous section, we can leverage these policies to manage the patch cycle on Apple devices enrolled into Intune.
Policy
Update policies are configured for macOS, iOS, and iPad Devices
Licensing Considerations
- Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Use Microsoft Intune policies to manage macOS software updates | Microsoft Learn
Use Microsoft Intune policies to manage iOS/iPadOS software updates | Microsoft Learn
End-User Impact
Level: Medium-High
Patching has always been notorious for being disruptive to end-users. When you configure the update policies, you can define specific time periods where updates will try to be deployed. This is typically in the after hours of business. When you use update policies for macOS, you might want to hide updates from users of supervised macOS devices for a period of time. You can accomplish this with a settings catalog policy for macOS devices that configure update restriction periods. You can follow these instructions to configure these settings: Use Microsoft Intune policies to manage macOS software updates | Microsoft Learn
Tips
The Install immediately setting is the most user-impactful setting as it will reboot the computer immediately.
PowerShell Scripts
Videos
Patching macOS Devices with Microsoft Intune | Microsoft Tutorial – YouTube
CIS Controls

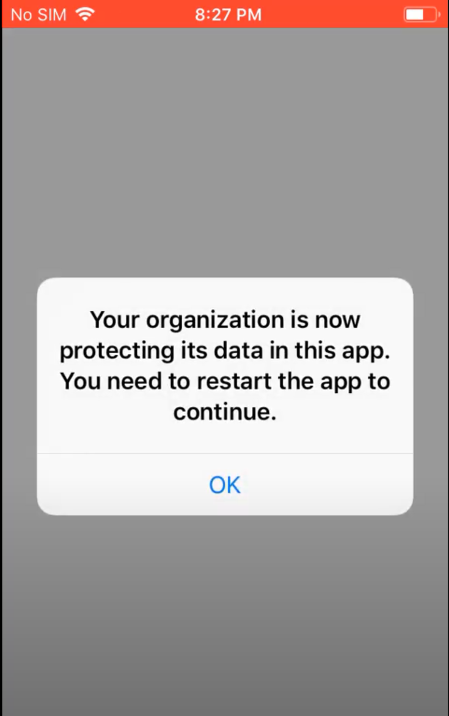
9. App Protection policies should be created for mobile devices
Leveraging the mobile application management (MAM) features of Microsoft Intune, app protection policies can be created so that users can access corporate applications on mobile devices securely, without having to enroll that device into the MDM solution. These settings allow you to place additional protection on applications such as requiring a pin or preventing cut, copy, and paste to unmanaged applications. App protection policies should be configured for iOS and Android devices.
Policy
App protection policies are configured for iOS and Android devices
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Create and deploy app protection policies – Microsoft Intune | Microsoft Learn
Android app protection policy settings – Microsoft Intune | Microsoft Learn
iOS/iPadOS app protection policy settings – Microsoft Intune | Microsoft Learn
End-User Impact
Level: Medium
When users go to access corporate data on a managed application like Outlook, they will receive a prompt that the devices is under corporate management. Depending on what settings are configured in the policy they might also have to a take additional action such as setting up an application pin.
Tips
Do not configure this setting for all apps on the device. The recommended setting is to configure all Microsoft Apps.
PowerShell Scripts
Videos
Protecting Corporate Data on iOS and Android Devices – YouTube
Android App Protection Policies – YouTube
iOS App Protection Policies – YouTube
CIS Controls
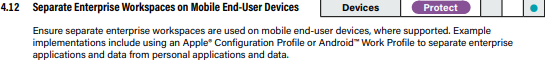
10. Mobile devices shall only be able to access corporate data through approved client apps
Conditional Access policies can be set up to only allow access to corporate data on client approved apps. This setting would prevent a user from leveraging the native mail client on their mobile application. A client that you are not able to control or wipe if they leave the organization.
Policy
Mobile devices shall only be able to access corporate data through approved client apps
Licensing Considerations
This setting requires at least an Azure AD P1 license which comes standalone or as part of the following bundles:
- EMS+E3/E5
- Microsoft 365 Business Premium
- Microsoft 365 E3
- Microsoft 365 E5
Set-Up Instructions
- Follow the steps outlined here to create a conditional access policy that requires approved client apps for mobile devices.
- In the Access Controls, only select the Required Approved Client App settings
*Note* You may chose to app the require app protection policy setting here as well but it will required that these devices enroll in the MDM solution. More information here: Grant controls in Conditional Access policy – Azure Active Directory – Microsoft Entra | Microsoft Learn
End-User Impact
Level: Medium
If a user goes to access corporate data on an unapproved client app, like the native mail app on the mobile device, they will be redirected to the Apple Store or Google Play store to download the approved client app (in this case, Outlook).
Tips
App Protection policies can be scoped to managed or unmanaged devices. If you have them scoped to managed devices, its likely you will want to include the “Require App Protection Policy” setting in the grant controls of the conditional access policy
PowerShell Scripts
- None Currently
Videos
CIS Controls

11. Lockout screen and password settings shall be configured for each device
Lockout screen timeouts should be configured for a certain number of minutes of activity for all device platforms. Password complexity requirements should be enforced and users should be prompted to change their password if it does not meet corporate requirements. In Intune, the location to configure these settings varies depending on the platform.
Windows: Security Baselines (Device Lock, Local Policies Security Options), Configuration Profiles (Device Restrictions: Password)
macOS: Compliance Policy (System Security)
iOS: Compliance Policy (System Security)
Android: Compliance Policy (System Security)
Policy
All supported devices have configuration settings defined/enforced for lockout screen timeouts and passwords
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Windows Security Baselines: Create security baseline profiles in Microsoft Intune | Microsoft Learn
- Under Device Lock set the password requirements
- Under Local Policies Security Options, Set the Minutes of lock screen inactivity until screen save activates policy
macOS Compliancy Policy: macOS device compliance settings in Microsoft Intune | Microsoft Learn
- Under System Security, modify the Password requirements and minutes of inactivity before password required
iOS Compliancy Policy: iOS/iPadOS device compliance settings in Microsoft Intune | Microsoft Learn
- Under System Security, modify the Password requirements and minutes of inactivity before password required
Android Compliancy Policy: Android Enterprise compliance settings in Microsoft Intune | Microsoft Learn
- Under System Security, modify the Password requirements and minutes of inactivity before password required
End-User Impact
Level: Medium
End users who enroll devices into Intune after this policy is enforced may be prompted to update their password if the policy requirements are not met on the device.
Tips
Make sure you don’t have conflicting policies between configuration profiles, security baselines, and compliance policies
PowerShell Scripts
Videos
macOS Configuration Profiles Intune – YouTube
iOS Device Restrictions-Microsoft Intune – YouTube
CIS Controls

12. Encryption shall be required on all devices
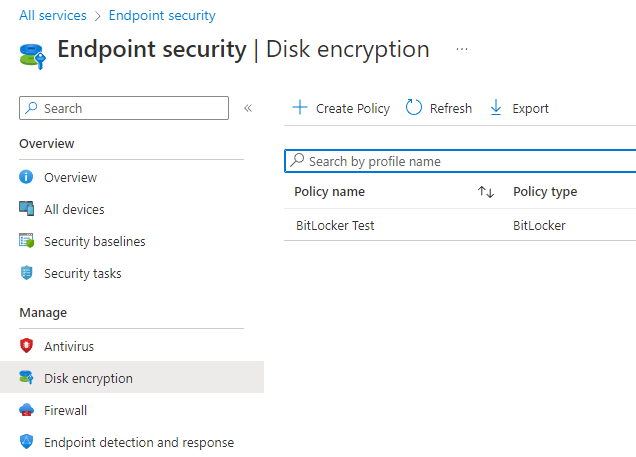
Disk encryption shall be configured on all corporate owned devices. Encryption of corporate data should also be configured at an application layer where applicable. In the Endpoint Manager Admin center, there is multiple locations to configure device encryption:
Endpoint Security>Disk Encryption: Allows you to configure encryption settings for FileVault (macOS) and Bitlocker (Windows).
Configuration Profiles: Endpoint Protection (Windows Encryption, FileVault), Device Restrictions (iOS, Android)
App Protection Policies (For application data encryption): iOS and Android
Policy
Disk encryption shall be required on all devices
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Disk Encryption: Manage disk encryption with endpoint security policies in Microsoft Intune | Microsoft Learn
Configuration Profiles: Configure Endpoint protection settings in Microsoft Intune | Microsoft Learn
App Protection Policies:
End-User Impact
Level: Low
If configured correctly, the end user should have no interaction with configuring encryption on the device. Leveraging configuration profiles or disk encryption settings should automatically configure the device encryption. There could be a use case where the configuration fails and the end user is prompted to fix on their device.
Tips
- Make sure you don’t have conflicting policies between configuration profiles, security baselines, compliance policies, and disk encryption profiles
- As a best practice, its best to push out the configuration profiles for disk encryption before enforcing any compliance policies that require device encryption. This will ensure that the encryption is silently configured an the user does not get prompted to set that up on their own.
PowerShell Scripts
Videos
Troubleshooting Bitlocker Encryption with Intune – YouTube
Enforce FileVault on macOS with Microsoft Intune – YouTube
S01E04 – Configuring and Deploying BitLocker Client Policies from Intune – (I.T) – YouTube
Configure BitLocker Policy in Intune – Create your own Intune lab (12/15) – YouTube
CIS Controls

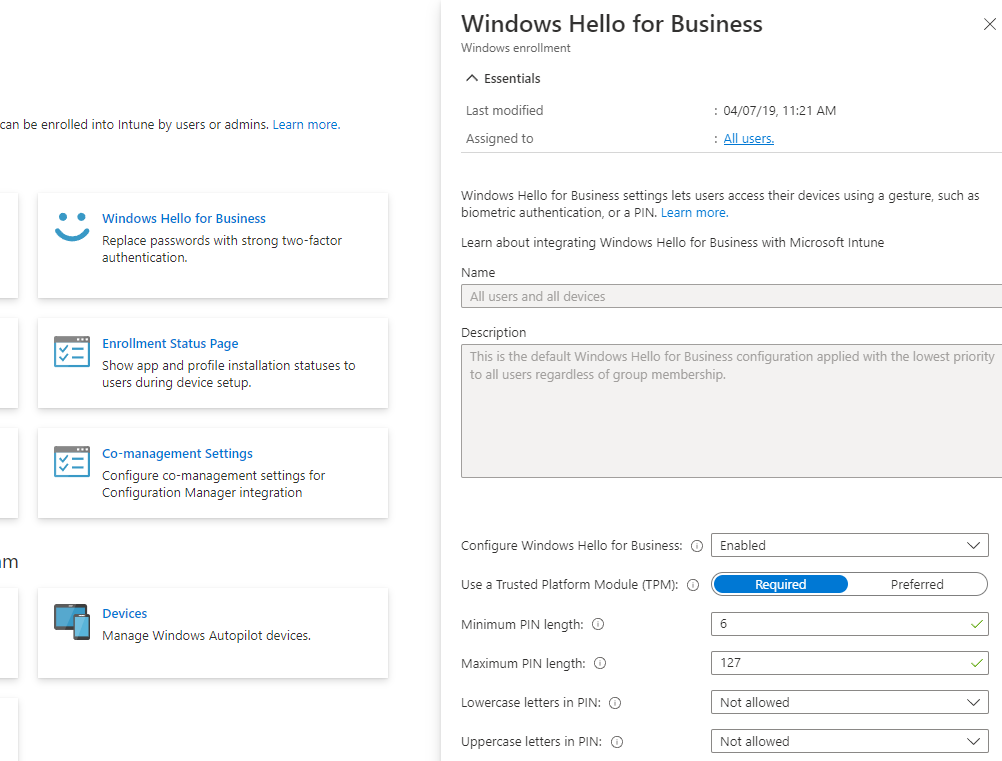
13. Windows Hello for Business should be configured where applicable
For Windows 10/11 devices, use of Windows Hello for Business replaces the use of passwords with strong two-factor authentication on devices. This authentication consists of a user credential that’s tied to a device and uses a biometric or PIN.
Policy
Windows Hello for Business should be configured where applicable
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
- Configure Windows Hello at the time of enrollment: Configure a tenant-wide Windows Hello for Business policy with Microsoft Intune – Microsoft Intune | Microsoft Learn
- Configure Windows Hello after device enrollment: Deploy policy for Windows Hello to groups of Windows 10 and Windows 11 devices in Microsoft Intune | Microsoft Learn
End-User Impact
Level: Low
Users will be prompted to set up facial recognition or fingerprint depending on the device. Users will also be asked to establish a pin in case that biometric authentication fails or cannot be accessed.
PowerShell Scripts
Videos
Deploy Windows Hello for Business using Configuration Profiles – YouTube

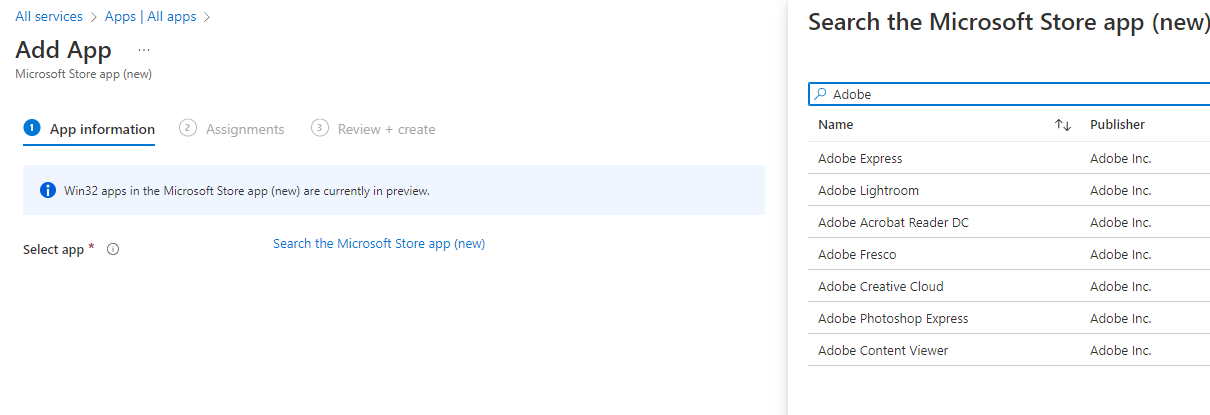
14. Authorized Applications should be deployed to managed devices
An authorized application inventory should be kept for corporate approved applications. These applications should be packaged and deployed in Microsoft Intune from the applications section of the Intune Admin Center. The application lifecycle should be maintained through Intune, including the patch cycle.
Policy
Authorized Applications should be deployed to managed devices
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
https://learn.microsoft.com/en-us/mem/intune/apps/apps-win32-prepare
Add Microsoft Store apps to Microsoft Intune | Microsoft Learn
End-User Impact
Level: Low
This will vary depending on the applications you are pushing out. The installation package you define will determine if the application will install automatically or provide the option to the user to install the application.
Tips
Leverage packaging tools like Winget and Chocolatey to help automate the app packaging and deployment.
PowerShell Scripts
https://github.com/Romanitho/Winget-Install
https://github.com/Romanitho/Winget-AutoUpdate
https://github.com/o-l-a-v/winget-intune-win32
Videos
Automate App Packaging: How to automate app packaging for Windows Devices – YouTube
Deploying Apps in Intune: https://www.youtube.com/watch?v=FGZ7hrVBSE4
Winget + Intune: https://www.youtube.com/watch?v=y2PbdOueUNQ
CIS Controls
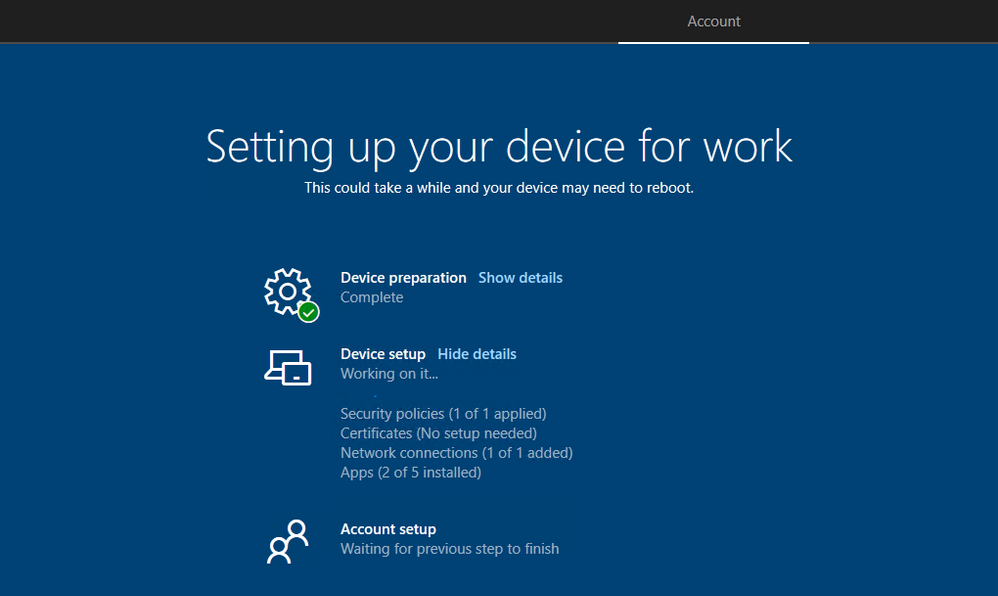
15. Device Use Shall be restricted until required applications are installed
When a user is first onboarding to a new device, required applications, such as your AV or Endpoint protection software, should be allowed to install before the user begins to access the device. This setting can be configured as part of the enrollment status page for people enrolling Windows devices and signing in for the first time.
Policy
Device Use Shall be restricted until required applications are installed
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Set up the Enrollment Status Page in the admin center – Microsoft Intune | Microsoft Learn
Selecting Required Apps for your Enrollment Status Page – Microsoft Community Hub
End-User Impact
Level: Medium
This will vary depending on the applications being installed. Its possible the user will have to wait some time for the applications to finish installing. For this reason, its best to define the minimum blocking applications as part of the settings and not make this the full list that will be installed.
PowerShell Scripts
None Currently
Videos
S03E02 – Enrollment Status Page What it is and What it isn’t – (I.T) – YouTube
Decode the Windows Enrollment Status Page | Microsoft Intune – YouTube
Set up the Enrollment Status Page – YouTube
CIS Controls
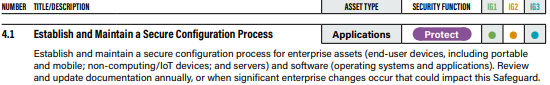
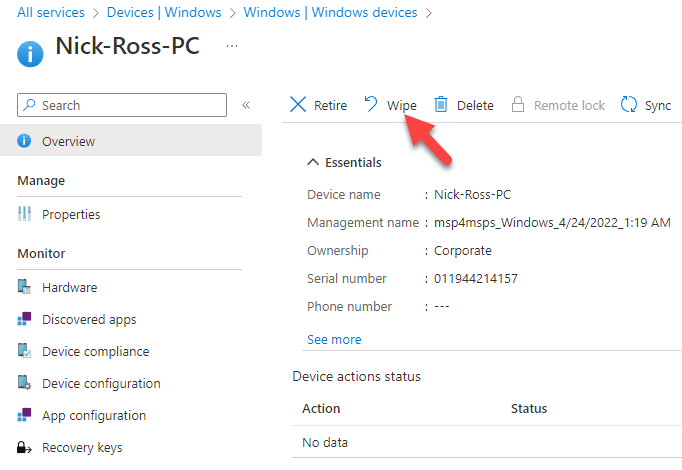
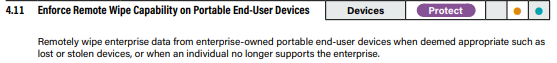
16. Devices and Applications shall be wiped when a user leaves the organization or reports a lost/stolen device
Standard operating procedures should be put into place to remotely wipe devices and applications when a user leaves the organization or a device is lost or stolen.
Policy
Devices and Applications shall be wiped when a user leaves the organization or reports a lost/stolen device
Licensing Considerations
Any tenant with Intune licensing can access this setting.
Set-Up Instructions
Retire or wipe devices using Microsoft Intune | Microsoft Learn
How to wipe only corporate data from apps – Microsoft Intune | Microsoft Learn
End-User Impact
Level: None
There should be no user impact here unless the actions to remotely wipe a device or application is done in error where the user should not have had that action performed against their device.
PowerShell Scripts
None Currently
Videos
How to Wipe and Remove a Windows 10 Device in Intune – YouTube
Remotely Erase MacOS using Microsoft Endpoint Manager (Intune) – YouTube
Windows Autopilot Reset – YouTube
MS28 – How to Perform Selective Wipe from Microsoft Intune – YouTube
CIS Controls
Bonus: Review CIS Microsoft Intune Benchmarks
CIS post benchmarks for Microsoft Intune Windows Devices. Currently they have benchmarks for Windows 10 and Windows 11 devices. The granularity of these benchmarks is too verbose to cover in this guide but I would encourage you to review it over time to see what additional controls you would want to add to your baseline depending on your environment.
You can download the benchmarks here in the Microsoft Intune for Windows section: CIS Downloads (cisecurity.org)
