Recently, Microsoft has announced the introduction of granular delegated admin privileges, or GDAP, coming early 2022. These changes are coming to address supply chain attacks (like Nobelium). Traditionally, both distributors (Microsoft Indirect Providers/CSP Tier 1s) and MSPs (Indirect Resellers) have established Delegated Admin Privileges (DAP) with all downstream customers. This allows distributors to license customer tenants and provide support. It allows you, as the MSP, to provide support and perform day to day management tasks via Partner Center.
The large security concern is that Delegated Admin Privileges (DAP) give you the keys to the kingdom (aka Global Admin Access) to all downstream customers. That means if you are compromised (or your distributor is compromised), all of your customers might be compromised as well. GDAP is going to help solve for this by providing a model of least privilege for access controls. I will be unpacking this at a high level from the details that have been made public so far, but just know there is a lot more to come here with the details of this announcement.
Comparison
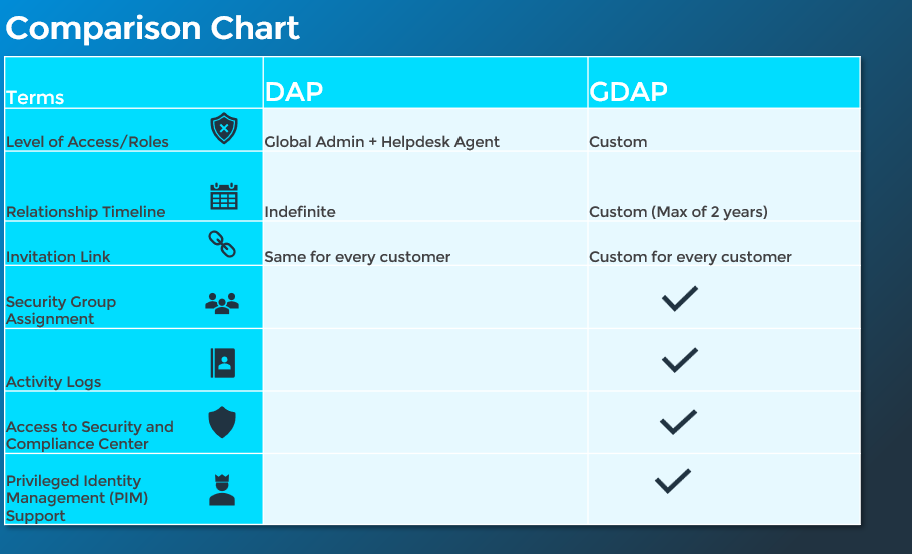
I am more of a visual person so I made this quick breakdown chart to cover some of the high level differences:
Level of Access/Roles: DAP relationships provide you the roles of Global Admin and Helpdesk admin by default without any ability to change. GDAP will allow you to select more granular level permissions and make that unique per customer. This is extremely important if you work with a distributor today and do not want that 3rd party risk.
Relationship Timeline: DAP relationships last indefinitely. The customer accepts the delegated admin link and that relationship is permanent unless you go under Settings>Partner Relationships and remove the relationship. GDAP allows you to create custom timelines for how long the relationship will be in place and there is also a maximum timeframe of 2 years. This means every 2 years you would have to reaccept the relationship per customer.
Invitation Link: DAP relationship links are universal per region. This means you use the same DAP link for every customer you onboard into Partner Center. GDAP changes that because you might have different levels of access per customer. This means that each link will be custom for each customer.
Security Group Assignment: There are no layers of assignment when it comes to DAP relationships. The same level of access is given to all members within a Partner Center environment who have access to customers. GDAP allows you to have nested security groups with separate roles in order to stratify permissions even further. Here is an example of that functionality:
“Partners can create a tier 1 support group and grant it service support admin and global reader roles, which means the group can create tickets on behalf of customers but cannot make any changes. Partners can create a tier 2 support group and grant it high-privilege roles such as Intune admin, Exchange admin, and Dynamics 365 admin.”
Activity Logs: With DAP, there are no granular activity logs that show you when delegated access permission are being leveraged from Partner Center and they also do not include any information around the lifecycle of a delegated admin relationship (when it was accepted, when it was removed, etc.). GDAP changes this by providing that visibility in the Azure AD Activity logs on both a partner level and a customer level.
Access to the S&C Center: This has been a pain point for MSPs for years in the fact that DAP does not allow you to enter certain admin portals on behalf of customers through partner centers. The Security and Compliance center (now splitting to two admin centers) has been a good example of this lack of access. GDAP is opening up more flexibly here and we will have to wait to see what additional admin centers will be accessible via delegated access.
PIM Support: Privilege Identity Management is a Microsoft service that allows for “just in time” levels of access. Essentially it allows you to elevate your role for a temporary period of time to perform certain admin tasks. PIM will be coupled with GDAP to allow partners to elevate privileges into certain security groups that have certain grants/roles into customer environments. This improves security even further.
Considerations
- Deciding what roles to provide as a baseline to customer environments: Since you now have autonomy to decide what roles you provide in customer tenants, you will have to determine a baseline and/or stratification based on how large your practice is as an MSP. If you work with a distributor, you will also need to be asking them what their baseline role is for every customer and request specific roles if applicable. Realistically, you should be giving them rights to license the tenant and provide a baseline of support.
- Operational Complexities: With GDAP there are now many layers you have to peel through from an operational standpoint. Outside of deciding levels of access, you also have to re-accept GDAP relationships every 2 years (minimum). Additionally, you have custom links per customer environment. Overall, I think the security benefits outweigh the additional complexity you are going to have to deal with. As an MSP, you should be evaluating your levels of access in customer tenants periodically for both yourself and 3rd parties.
- Access to New Admin centers! : This is a huge win if GDAP allows for delegated access to all of the admin centers (Like S&C center) that we have been missing for years. This will stop this horrible practice I see where MSPs are creating a Global Admins in customer tenants and sharing MFA across a group of techs.
- Free Azure AD P2 licensing: Microsoft announced last month that they are giving P2 away for 1 year so you can leverage things like PIM. Definitely take advantage of that to provide more security within your Partner Center environment.
Timelines
Currently Timelines (Updated 5/7/2022)
Transition active and inactive DAPs: Starting May 22, 2023
- Microsoft will begin transitioning active and inactive DAP relationships to GDAP with limited Azure Active Directory (AD) roles. We will provide clarity on the roles by March 15, 2023.
- For relationships that have been transitioned from DAP to GDAP, we will proceed to remove the corresponding DAP relationships 30 days later.
- We will pause the transition for the month of June to support the fiscal year closure.
The dates for the following milestones will be communicated on March 15, 2023:
- Stop new DAPs—DAP is currently granted when a new customer tenant is created. Microsoft will no longer grant DAP for new customer creation.
- Grant GDAP default roles for new customers—GDAP with certain default roles will be granted when a new customer tenant is created.
- Retire the bulk migration tool—The bulk migration tool will be retired.
PC Announcement: February 2023 announcements – Partner Center | Microsoft Learn
My Resources:
- Monitoring DAP relationships: https://tminus365.com/monitoring-dap-relationships/
- Adding GDAP Relationships: https://tminus365.com/adding-gdap-relationships/
- Choosing Roles for GDAP relationships: https://tminus365.com/what-roles-should-i-add-for-gdap/
- Leveraging GDAP and PIM: https://tminus365.com/leveraging-pim-with-gdap/
Microsoft Resources:
- November 2021 Partner Center Announcement: https://docs.microsoft.com/en-us/partner-center/announcements/2021-november#5
- December 2021 Partner Center Announcement: https://docs.microsoft.com/en-us/partner-center/announcements/2021-december#9
- January 2022 Partner Center Announcement: https://docs.microsoft.com/en-us/partner-center/announcements/2022-january#6
- February 2022 Partner Center Announcement: https://docs.microsoft.com/en-us/partner-center/announcements/2022-february#6
- Microsoft Operations Readiness Resource Gallery: https://partner.microsoft.com/en-US/resources/collection/granular-delegated-admin-privileges#/
- GDAP Implementation Partner Center Docs: https://docs.microsoft.com/en-us/partner-center/gdap-introduction
- GDAP Relationship Analytics: https://docs.microsoft.com/en-us/partner-center/gdap-relationship-analytics
- Least Privilege Roles by Task: https://docs.microsoft.com/en-us/azure/active-directory/roles/delegate-by-task
- Monitoring Admin Relationships: https://docs.microsoft.com/en-us/partner-center/dap-monitor-self-serve-removal
- GDAP FAQ: https://docs.microsoft.com/en-us/partner-center/gdap-faq

[…] I wrote a detailed write-up on this you can check out on my blog: https://tminus365.com/granular-delegated-admin-privileges/ […]