Evolution of MFA
Passwords
- They are usually weak or easily crackable
- They are not unique
- They are stored insecurely
- 3rd party databases get breached all the time and passwords are exposed. We have an extension of exposure to all of the vendors that don’t integration to our IDP (i.e. Entra)
- Password Managers have been breached (Last Pass)
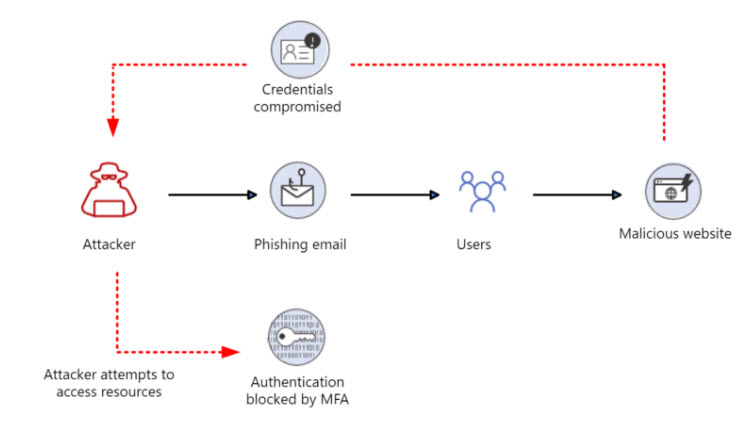
- Users can easily be breached via phishing attempts
OTP/TOTP
- SMS/Phone
- Software Tokens/Push Notifications
- SMS/Phone
- SIM Swapping
- Social Engineering
- Lost/Stolen devices
- Email
- Often, the 3rd party email we set up here to get the OTP does not have MFA enabled. (i.e. a personal Gmail account that gets added as the 2nd factor to our Microsoft account)
- Software Tokens/Push Notifications
- Social Engineering
- MFA fatigue on Push notifications
While I would consider these to be weaker forms of MFA, they are still better than nothing. Remember that having any form of MFA will prevent over 90+% of the common attacks out there today.
Authenticator + Number Matching
FIDO/FIDO2 => Passkeys
- They are passwordless
- They require device-bound context meaning the user has to perform some gesture on the device where the passkey is located. (i.e. their laptop, authenticator app, yubikey, etc.). This includes faceID, thumbprint, pin, etc.
- When registered, they include a “Registered Provider” or “origin” which can overcome fake or fictitious websites
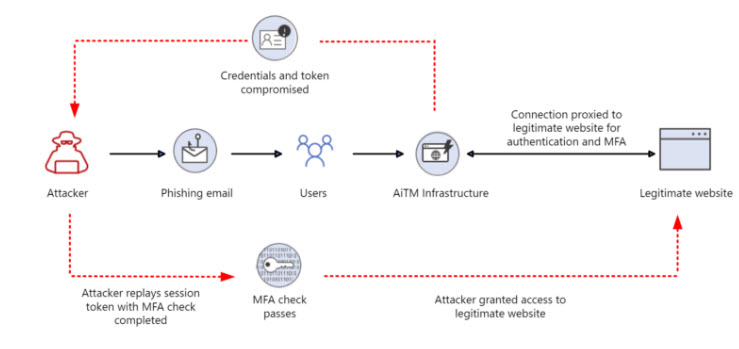
- If we look at this in the context of the Evilginx framework, users are directed to login as some website disguised as Microsoft. This could have the url of: login.microsoftonlline.com (it is subtle but I have to L’s in the “online” portion of that url)
- When a passkey is established for Microsoft it will be registered with the origin of login.microsoft.com
- Even if the user clicked on a malicious link bringing them to the fake website, the passkey would recognize the illegitimate website and not allow them to sign in, thus being phishing resistant.
Setting up Passkeys on Authenticator
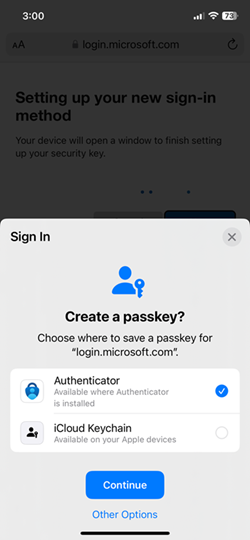
Passkeys => Thinking about the end-user impact
- Users will need to set up Passkeys in the “My Security Info Page”
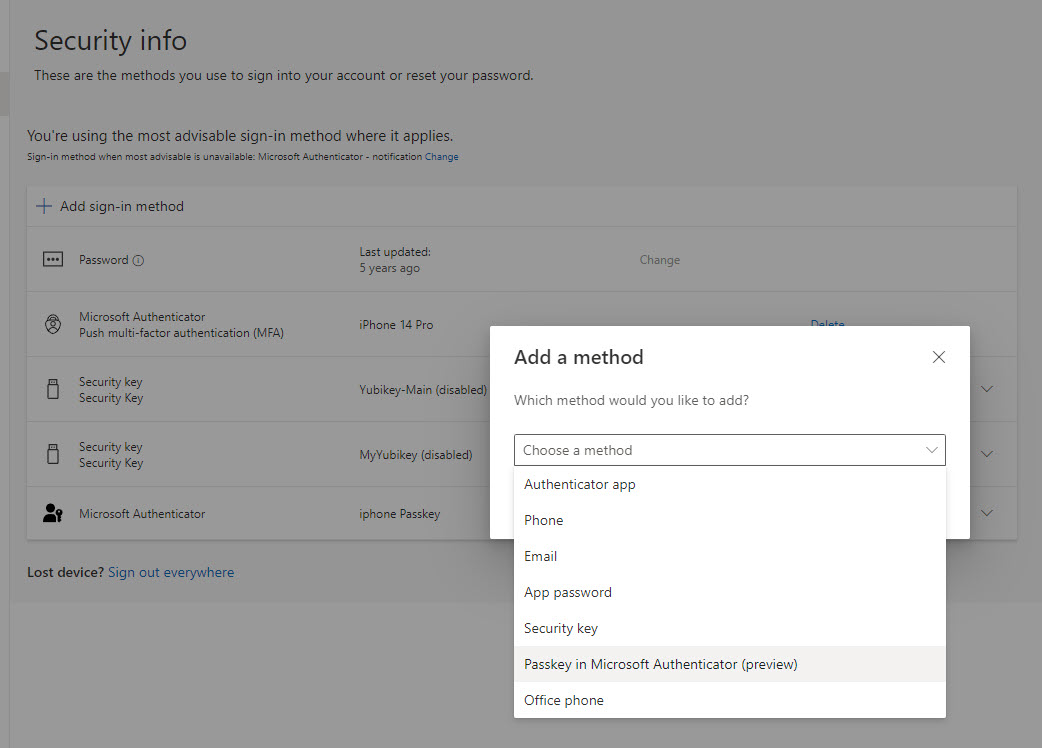
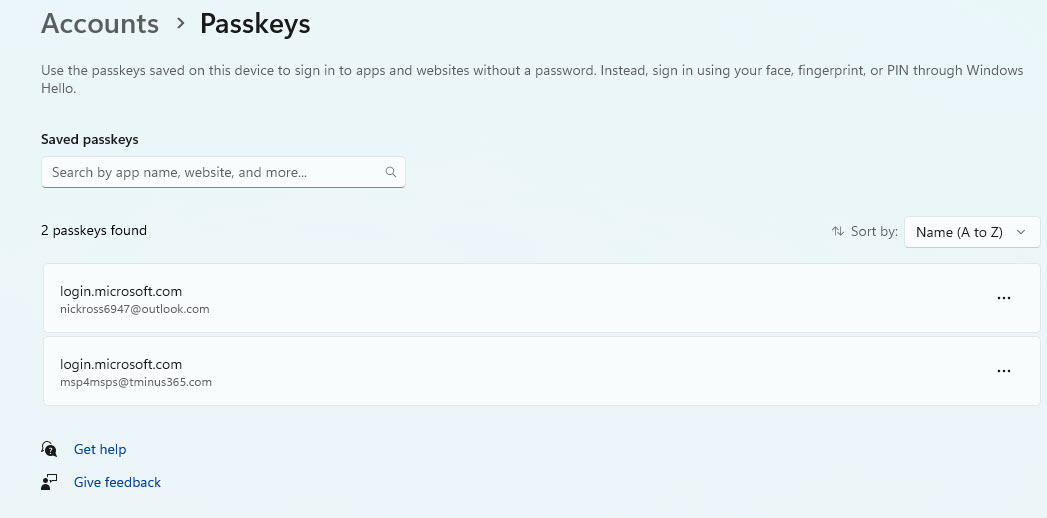
If a user does not follow the instructions correctly, they could store the passkey on their keychain on iOS instead of authenticator:
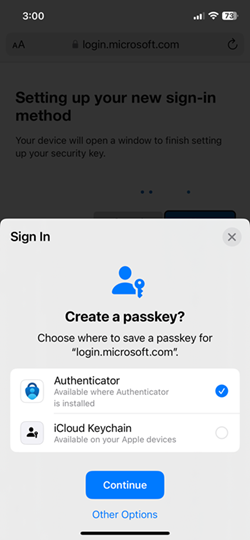
If passkeys with authenticator are the only 2nd factor you enable through conditional access, users will get prompted to scan a QR code when signing in:
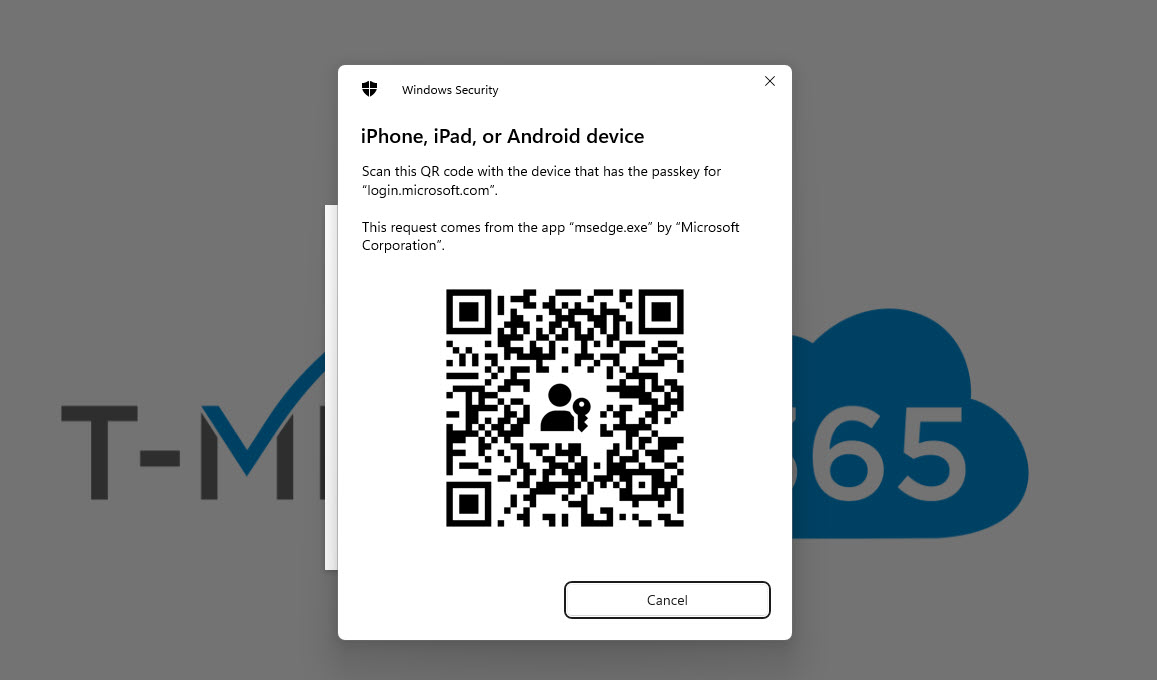
If you are enforcing Passkeys for all users, net new users who need to register will need a Temporary Access Pass to login to the security page where they can then add the Passkey.
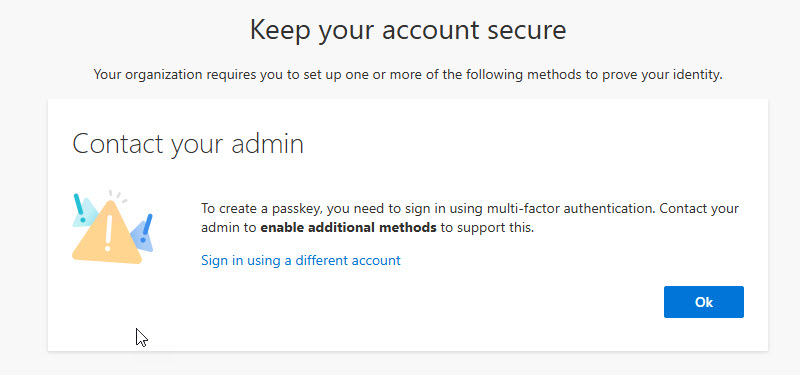
NOTE: If you do not already have Temporary Access Pass enabled, you will want to let this propagate around 8 hours before attempting to use that to sign in with a user that does not have MFA set up yet and register for a passkey. In my experience, I got weird error messages and stuck in an infinite loop of hell before I just waiting for Microsoft to propagate (classic)
If a user loses their mobile device or gets a new one, they will need another Temporary Access Pass to re-establish a new Passkey. This is an easily flow in my opinion than if they lost their Yubikey.
Pass-the-Cookie Attack Considerations
Pass-the-cookie attack involves a malicious compromise of a users device where an attacker can harvest the session cookie from a users browser and leverage it to garner an authenticated session on their device. It requires no login or MFA prompt. This attack would still bypass passkeys as well. Microsoft has come out with a conditional access policies setting for token protection that would help to alleviate token based attacks which is bound to a users device. Learn more: Token protection in Microsoft Entra Conditional Access – Microsoft Entra ID | Microsoft Learn
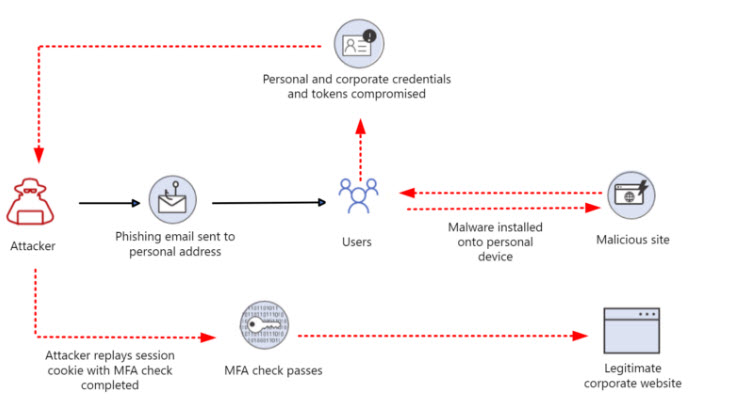

- Ensure that users are not signing in from personal devices where your security protection are not in place
- Pass-the-cookie attacks often use mimikatz which can be discovered and blocked by Microsoft Defender and other EDR/AV vendors
- Have Safe Links and Safe attachments policies in place to help protect users in email/documents
- You can leverage Strict location continuous access evaluation controls in conditional access policies to prevent this attack as well
