More than 99% of Identity attacks are password attacks
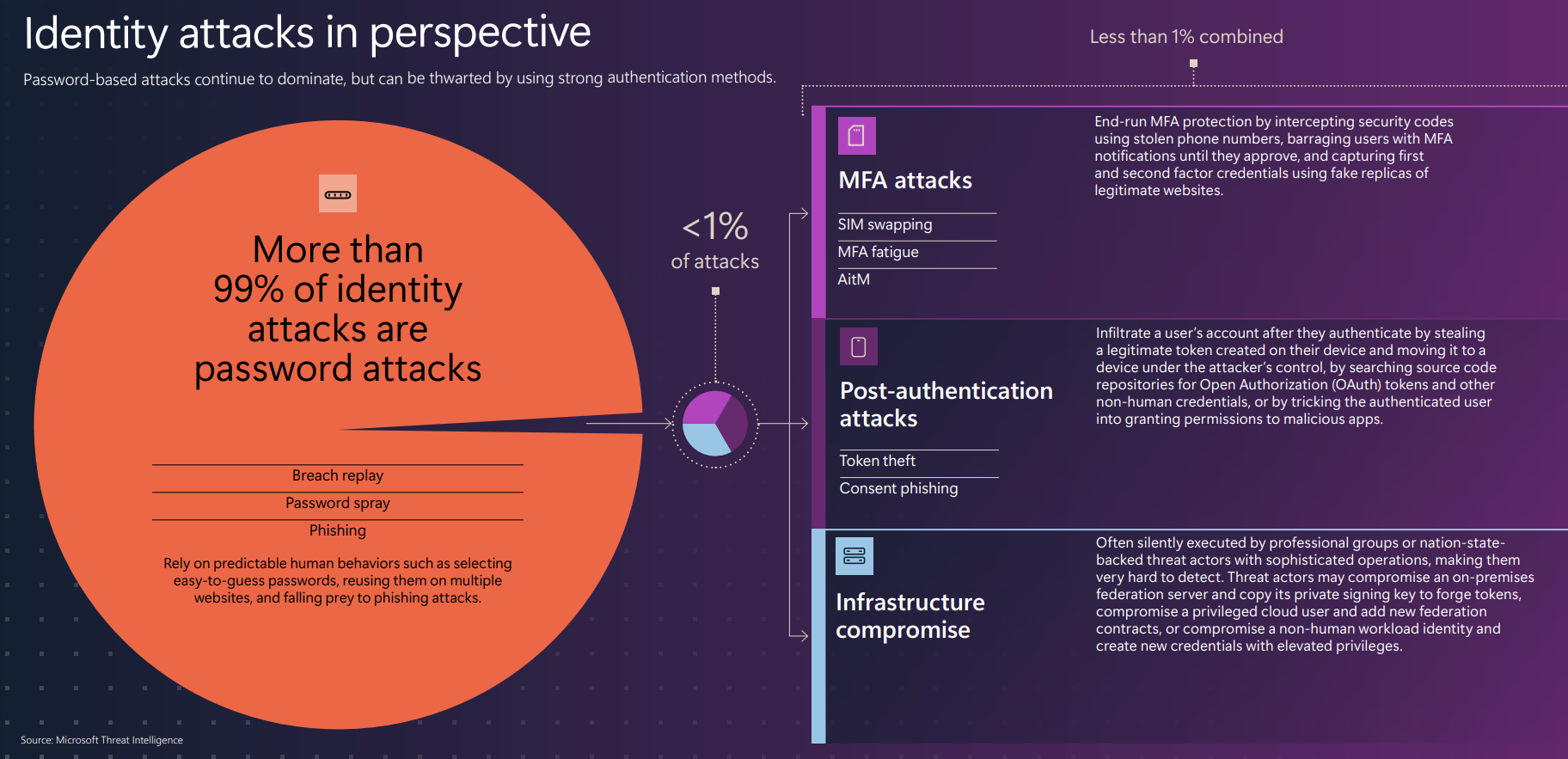
- 7,000 password attacks are blocked PER SECOND over the past year
- While token theft and AiTM attacks have grown significantly in both popularity and frequency, they still only represent a tiny fraction of attacks seen in the wild.
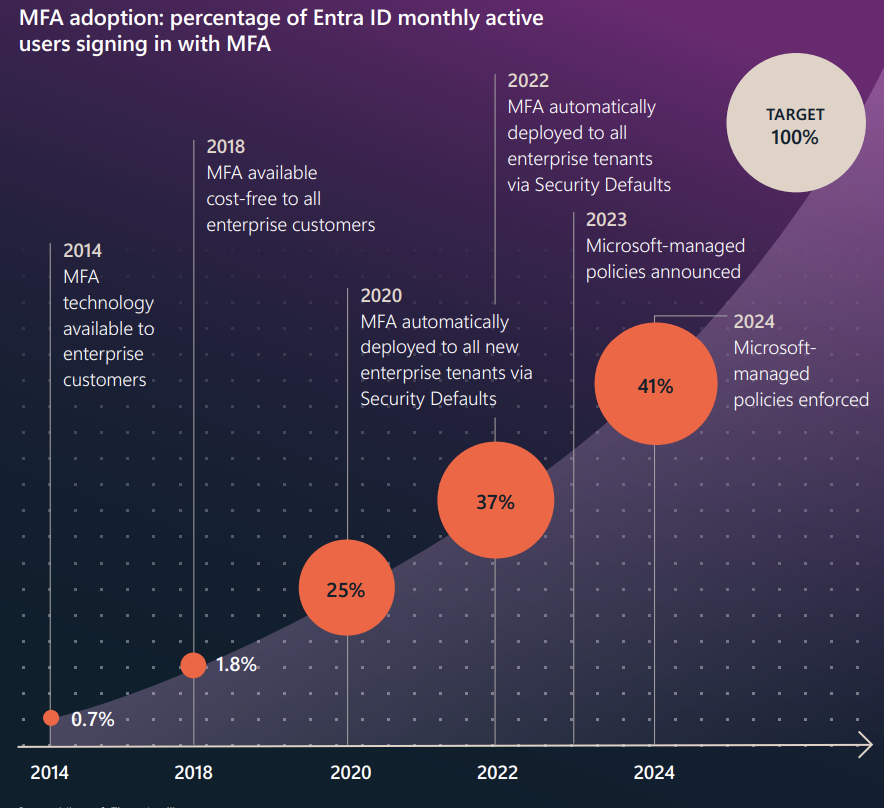
Microsoft's UX Research
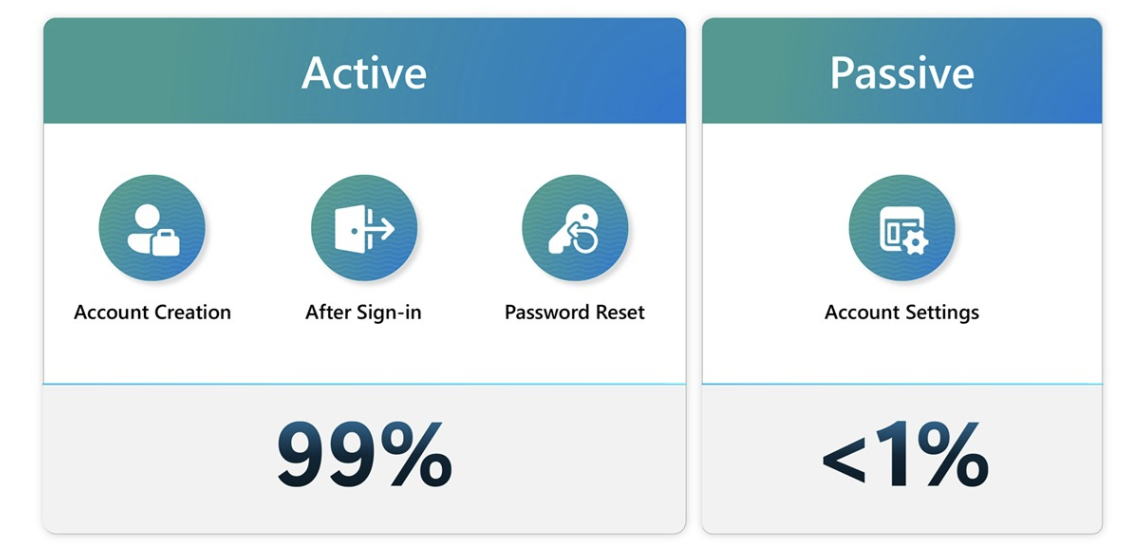
The statistics they present are encouraging not just to help prevent password based attacks but also help with rising AiTM attacks we are seeing as well. While they don’t site the full size of the audience they experimented with or the user type (i.e. consumer vs business user), there were some encouraging stats around the adoption and use of Passkeys:

Nudging users to sign up with Passkeys:
End User Experience (Microsoft Authenticator)
Setup
- If a user already has a profile set up in Authenticator, they can simply set up a passkey in that profile
- In the video below, I show the user experience for someone who has not set up a profile in Authenticator and has no password. In this case, we issue them a Temporary Access Pass (TAP) to get in and register a passkey. This would be your workflow for a new user onboard.
- Set up of Non-portable passkeys such as leveraging Windows Hello can be baked into a new user onboarding to their workstation and provides for an easier sign-in method than authenticator provides today in my opinion.
Signing In
Signing in is still a bit clunky too as the user has to use the camera on their phone to scan a QR code which will find the passkey in Authenticator to fulfill the sign in request. Even for me, this seems like more of a hassle than getting proactively prompted by authenticator to simply put in a number I see in the screen. For our end-users who already see MFA as an inconvenience, this added step of scanning a QR code is not going to go over well in my opinion.
Other Barriers to adoption/considerations:
Besides the obvious resistance to change and confusion that comes with moving away from passwords, I see the other following situations:
- Hybrid Environment constraints => Legacy and hybrid environments may still need to support passwords for other systems making it harder to adopt
- User onboarding changes => Temporary access passwords will have to be incorporated into user onboarding SOPs which might be a significant change to your MSP and/or the HR/Managers across customer environments who have been traditionally issuing passwords.
- Lost/Replaced Devices=> This constraint is not too much different than what exist today if we have our users on Microsoft authenticator for phones.
