How many of you can confidently say that your business maintains a centralized and approved application inventory? If you’re like most organizations, the answer is either “no” or “we have one, but it’s incomplete.” And honestly, that’s not entirely your fault.
With the rise of SaaS tools, ease of access, and the ability for employees to sign up for applications on their own, keeping a tight grip on your application inventory is incredibly challenging. But this shadow IT introduces significant risks to the organization—ranging from data exfiltration to security vulnerabilities in unapproved applications.
In this blog series, we’re going to break down software inventory management and security, mapping it directly to CIS Control 2 (Inventory & Control of Software Assets). We’ll also dive into Microsoft 365’s security tools, showing you how to protect your organization against these risks.
The Uncontrolled Software Inventory Problem
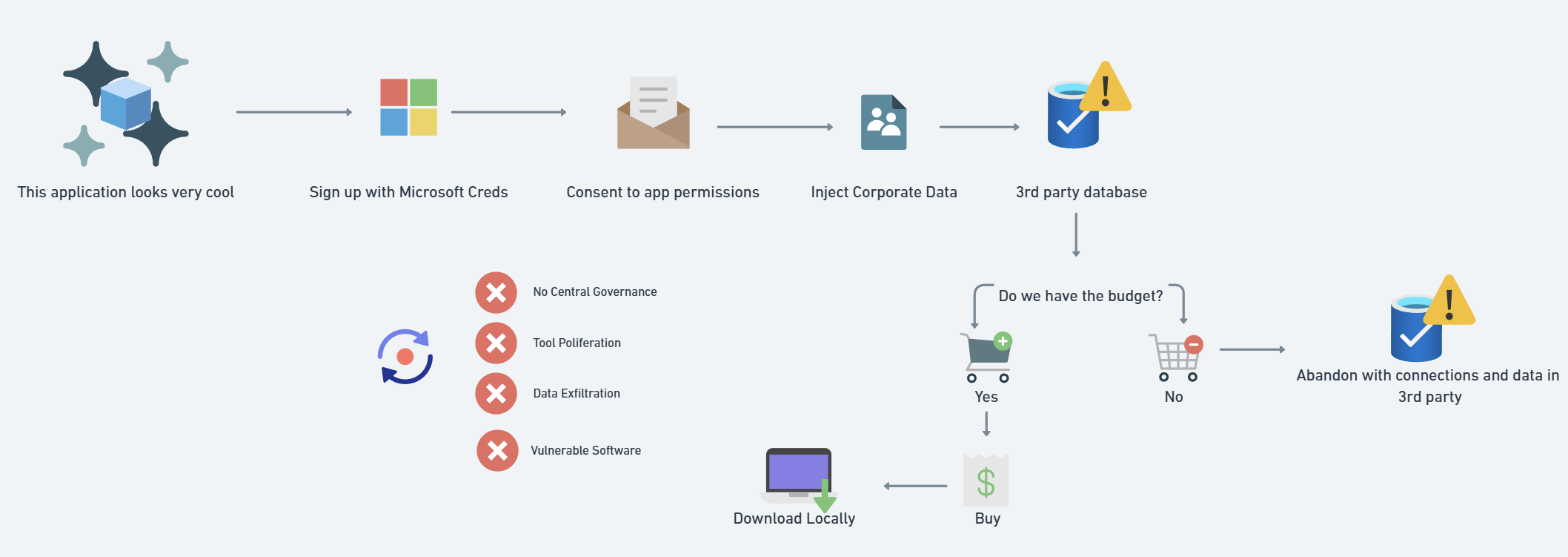
Let’s zoom out and look at how applications typically get introduced into a business.
💡 A marketing team member finds an exciting new tool and signs up with their business email.
💡 During sign-up, the tool asks for permissions to access Microsoft data (email, calendar, etc.).
💡 No approval process exists, so the user grants permissions without realizing the security risks.
💡 The tool starts storing company data in an unknown third-party database.
💡 If the company doesn’t approve the tool, they may abandon it—but the data and access remain.
Repeat this process across multiple departments, and you’ve got a recipe for software proliferation, data sprawl, and security risks. What I am referencing here is Oauth applications. Not all applications will ask for these permissions into your Microsoft tenant but still carry their own risk whether or not they are downloaded locally to workstations.
Default Settings and Inherent Risks
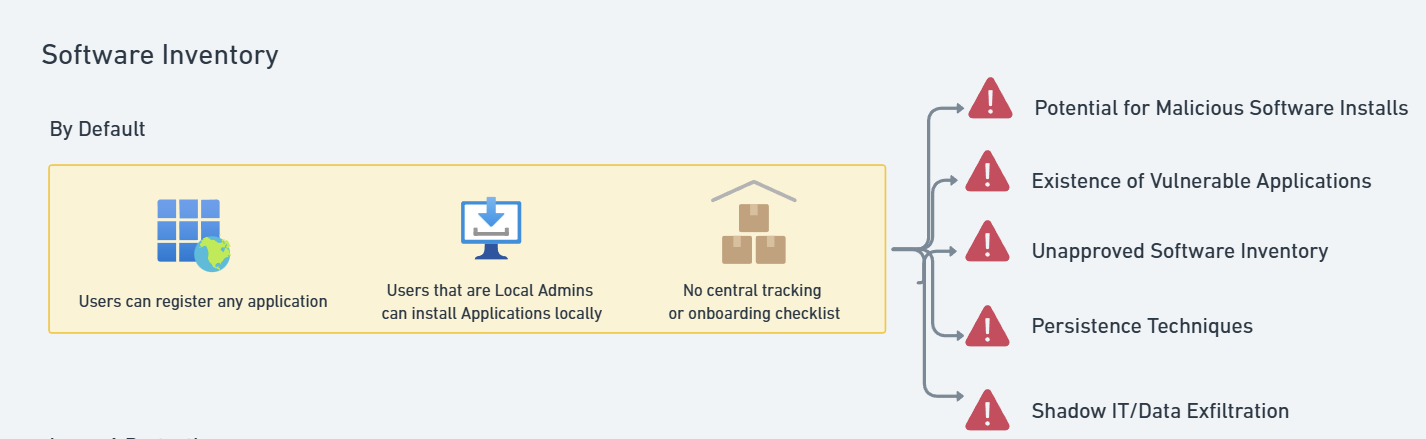
A lack of software governance exposes businesses to several security threats:
🔹 Unauthorized Data Access – Unapproved apps might be storing customer data in insecure locations.
🔹 Vulnerabilities in Third-Party Apps – The applications onboarded can have vulnerabilities such as zero-days and public exploits either now or in the future.
🔹 Persistent Backdoor Access – Attackers can exploit OAuth permissions to maintain access to accounts.
🔹 Shadow IT & Data Exfiltration – Employees may move sensitive company data to personal or unvetted apps.
- By default in Microsoft 365, any user can register an Oauth application and grant specific permissions. We’ve seen legitimate application abuse for persistence techniques. Ex: Deep Dive: Forensic Analysis of eM Client
- Companies like Proofpoint and Huntress have provided research and findings that over 10%+ of the tenants in their ecosystem had some type of traitorware application that was likely used by attackers.
- Removing users as local admins is usually something we clean up right away if a client has this present in their environment but unrestricted admin rights allows users to download any application they want locally. Your only layers of defense after is AV/EDR tools.
- Most importantly, there is a central lack of governance in most businesses that I consult with. No central inventory tracking and no Vendor Management policy/SOP that defines your minimum security standards.
How to Take Back Control: A Layered Approach
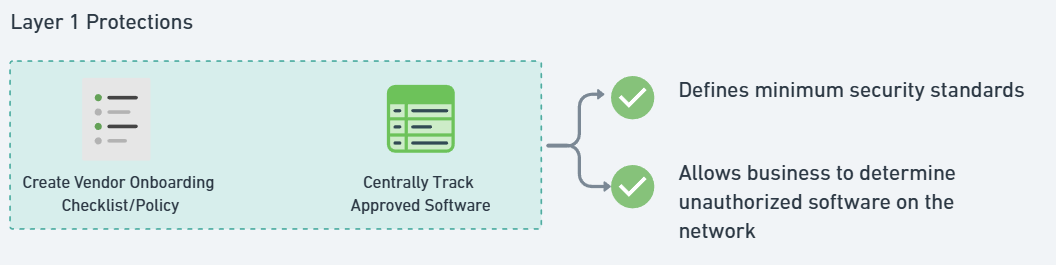
✅ Create a centralized software inventory—this can start as a simple spreadsheet tracking:
- Application Name
- Business Purpose
- Department Owner
- Security Review Status
✅ Implement an application approval process—define security standards:
- Does the tool have MFA & security controls?
- Does it store sensitive data?
- Does it comply with regulatory standards (SOC 2, ISO, etc.)?
✅ Regularly review & update the inventory—audit usage and security posture.
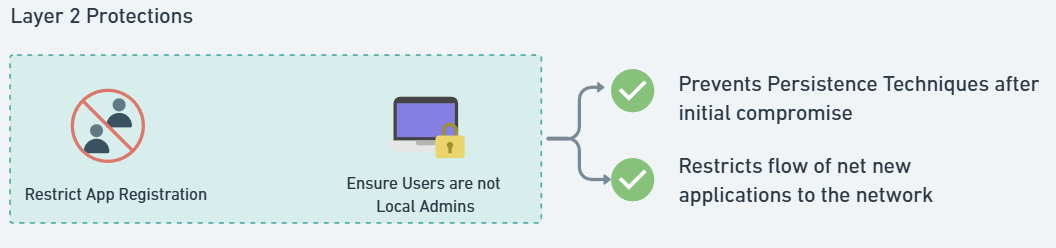
✅ Block unapproved app registrations in Microsoft Entra ID.
✅ Remove local admin rights from users to prevent unauthorized software installs.
✅ Provide end-users a path to make request for net new applications or application updates. (can be done manually or by using 1st party or 3rd party add-ons)
The following provides a stop gap so that users are forced to go through an approved workstream to get net new applications onto the network or end-user workstations.
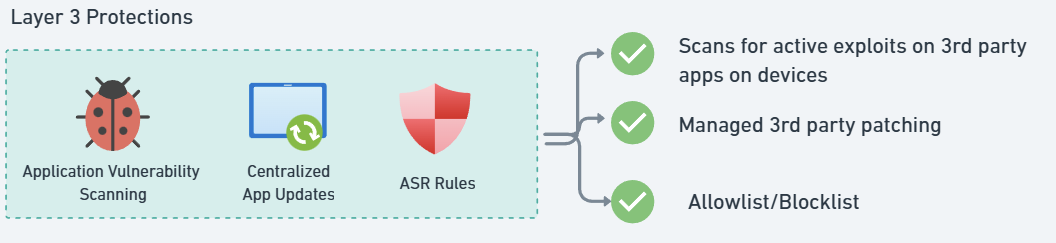
Leverage Defender for Business to:
- Detect vulnerable applications.
- Identify exploitable security flaws.
✅ Use Intune for centralized app updates—ensure critical security patches are applied.
✅ Enable Attack Surface Reduction (ASR) rules to prevent risky software from executing.
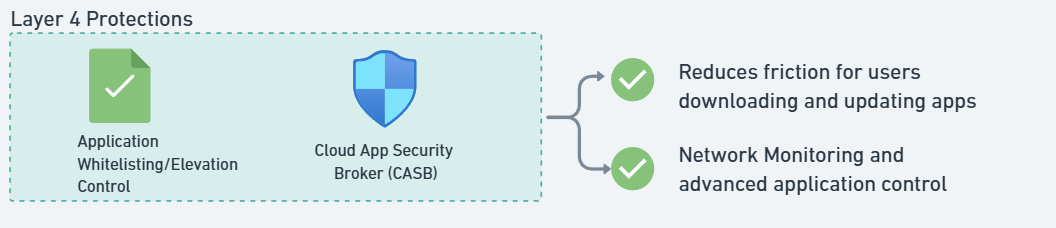
✅ Deploy Microsoft Defender for Cloud Apps (CASB) to:
- Monitor SaaS usage across the entire network.
- Identify risky applications before they become threats.
- Enforce conditional access policies based on risk scores.
- Sanction and unsanction applications on
✅ Implement Application Whitelisting—restrict software installs to an approved list.
✅ Implement Additional Applicaiton Control Policies—implement policies like App control for business (previously known as App Locker) for further tightening of application installs.
✅ Use Just-in-Time (JIT) Privilege Elevation—allow temporary admin rights when necessary.
Conclusion: Maximizing Security with the M365 BP stack

We will be covering all of these security controls as part of this blog series. Microsoft 365 Business Premium can achieve almost all of the controls I recommend as part of a secure application management practice but I will also elude to common 3rd party MSP tools you might be leveraging as well.
Automated Security Assessment for Applications
If you’re struggling with Microsoft 365 security assessments, I highly recommend CloudCapsule—a tool I built to audit your Microsoft environment against CIS controls.
👉 Run a free assessment at cloudcapsule.io and instantly get insights into your tenant security posture, software inventory, and risk exposure.
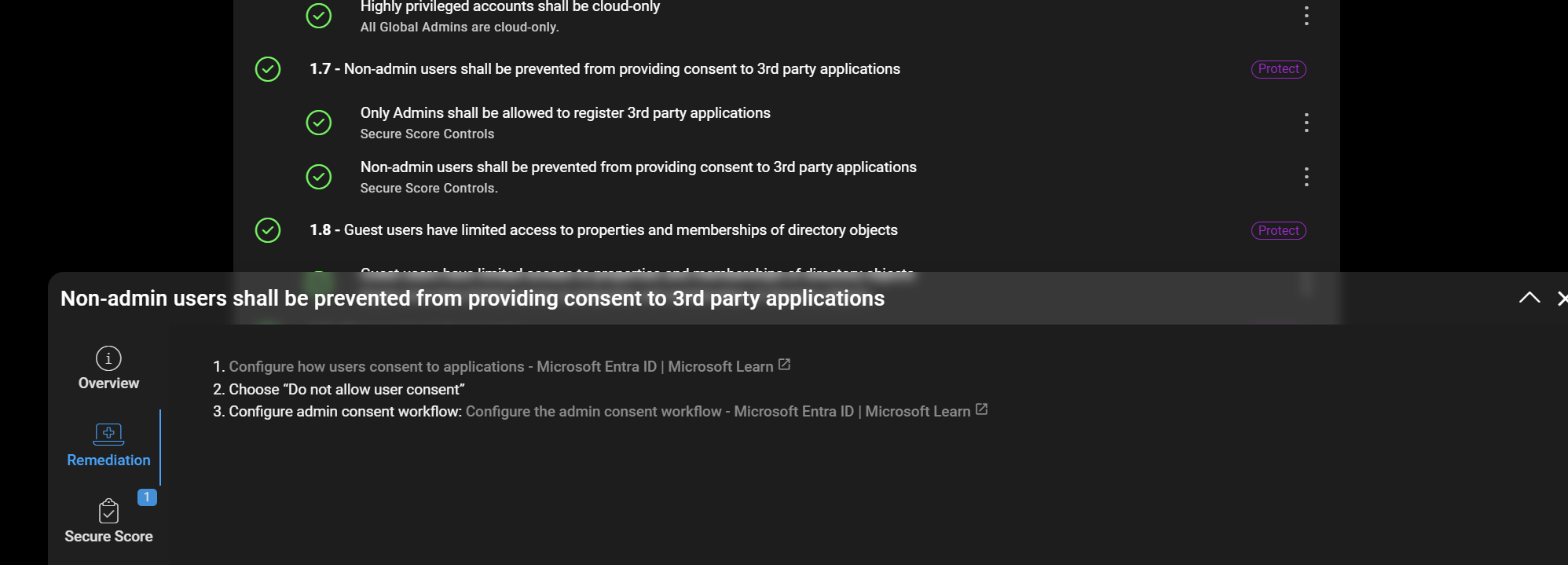
CloudCapsule audits all of your tenants for the recommended hardening policies for locking down applications.
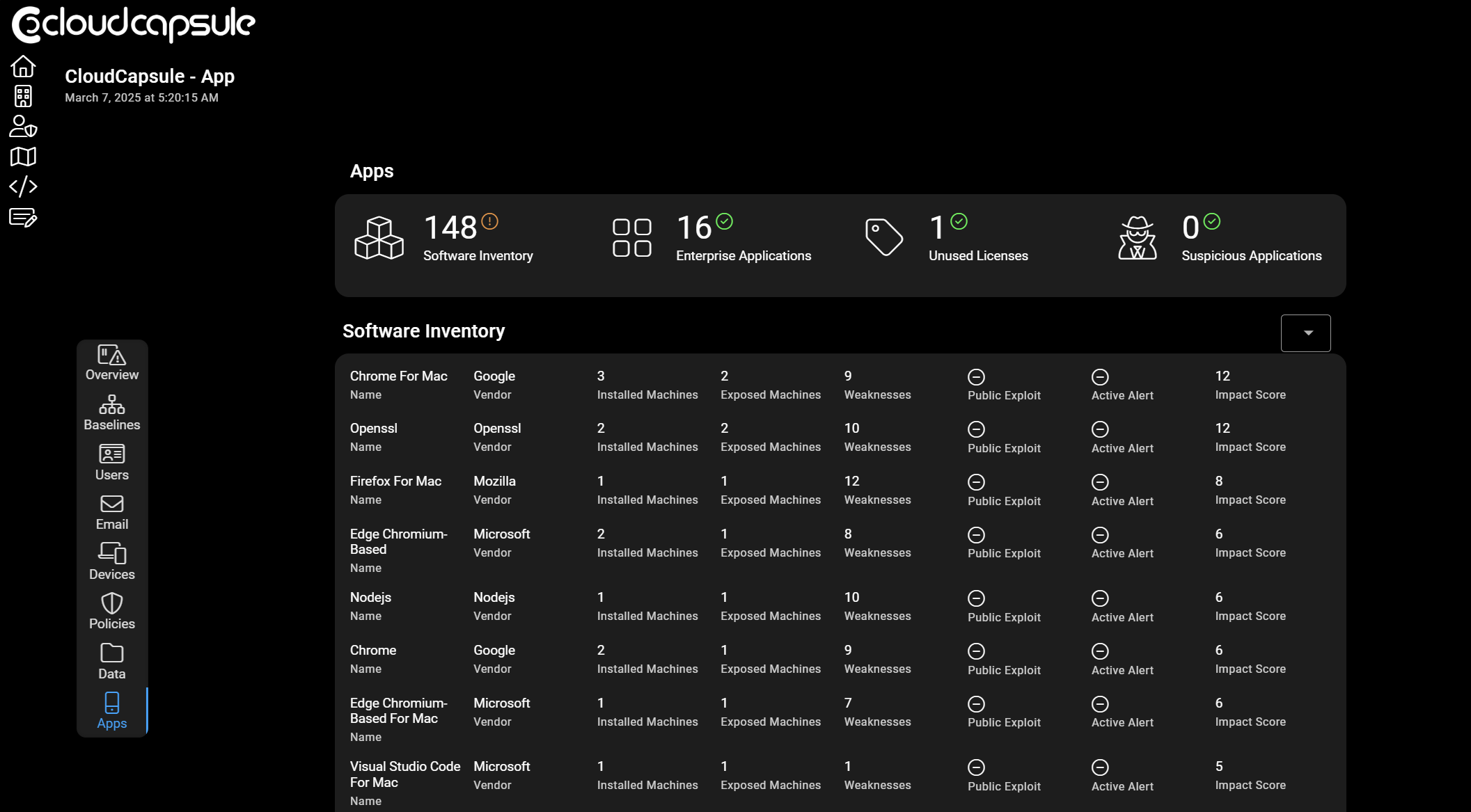
It also provides central tracking of your entire software inventory (agentless) across workstations and enterprise apps. Suspicious or malicious Oauth applications can be detected along with any active exploits across your inventory.
