- Any device
- Any network location
- Anywhere in the world
Managed Device Policy Matrix
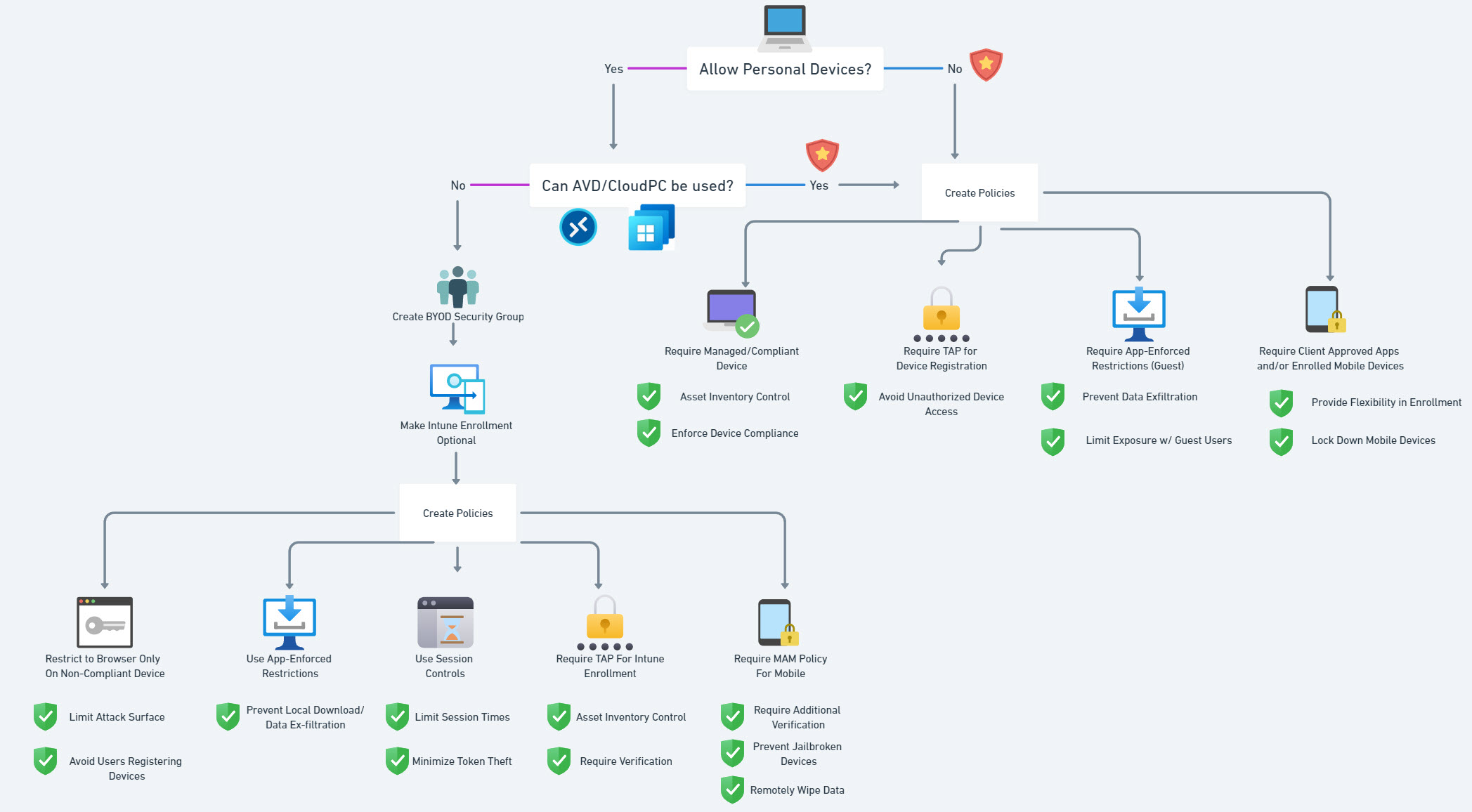
So like I mentioned last week, we want to channel our customers into using only approved managed devices. Today we are going to walk through the first recommended policy for secure device access which is requiring a managed and/or compliant device.
Default Settings
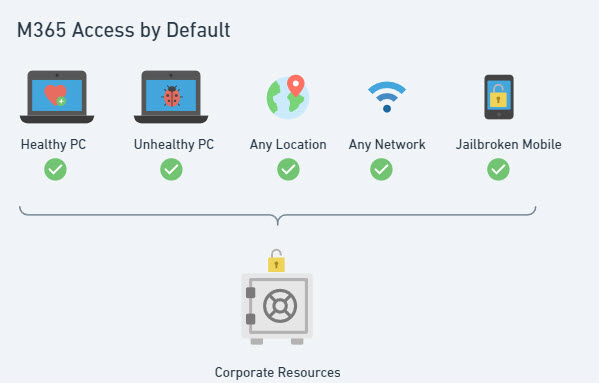
Baseline Policies
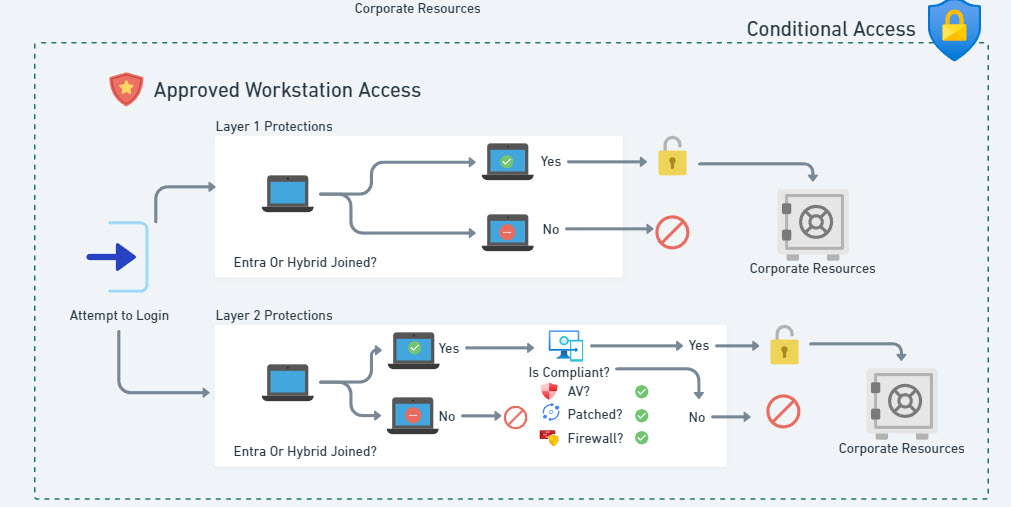
Layer 1 Protections: Block Access on Devices that are not Entra Joined or Entra Hybrid-Joined
How to Configure
- Go to the Entra Admin Center
- Protections>Conditional Access>+New Policy
- Name: Block Unmanaged Devices
- Users > All Users
- Exclude Break Glass User + (For CSP using GDAP>Exclude Guest >+Service Providers)
- Target Resources > All Cloud Apps
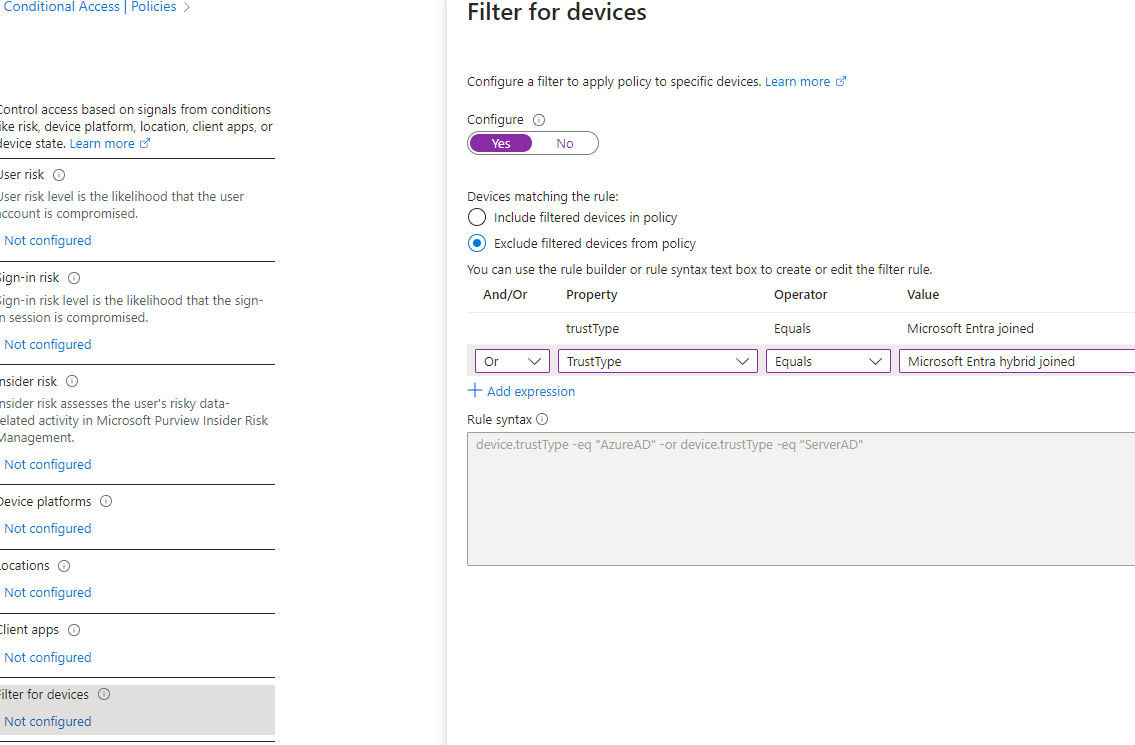
- Conditions>Filter for Devices>Exclusions>Device TrustType = Entra Joined or Entra Hybrid Joined
- Grant>Block
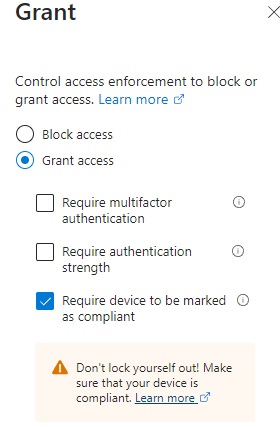
Layer 2 Protections: Require a Compliant Device
- Microsoft Intune is leveraged and devices are enrolled
- Device compliance policies are configured enforced for Device access
- Does the device have AV turned on?
- Is the device at a low risk state with Defender?
- Is the device patched?
- Ensure that all managed devices are in Intune
- Have an SOP in place for managing “Non-Compliant” devices given the policy we are implementing would lock them out of their account if it is not.
How to Configure
- Go to the Entra Admin Center
- Protections>Conditional Access>+New Policy
- Name: Require Compliant Device
- Users > All Users
- Exclude Break Glass User + (For CSP using GDAP>Exclude Guest >+Service Providers)
- Target Resources > All Cloud Apps
- Grant>Require Device to be marked as Compliant
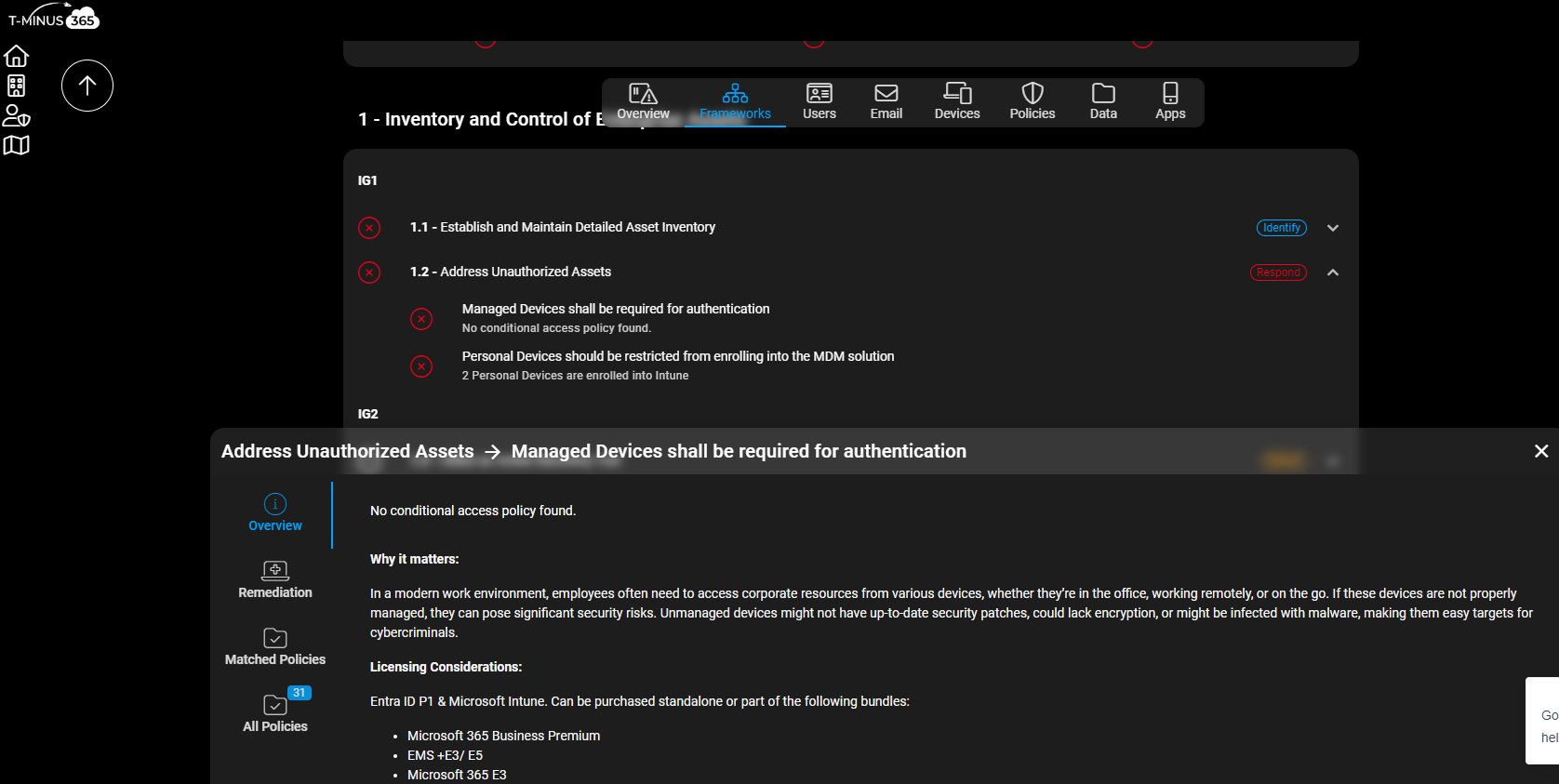
Tooling to help with reporting on these policies
I built a tool called CloudCapsule that allows you to connect your tenants to run a security assessment against the controls in place to CIS. You can perform a scan to look for these policies across the tenants that you manage.
Conclusion
Ok guys, I highly encourage you to go enforce at least the Layer 1 conditional access policy I showed here to start locking down your environment. Stay tuned next week as we cover the next recommended policy I have for secure device access. Subscribe to the newsletter to get automatic updates. If you didn’t see last weeks video on my top policy recommendations for BYOD/personal devices, be sure to check that out.
