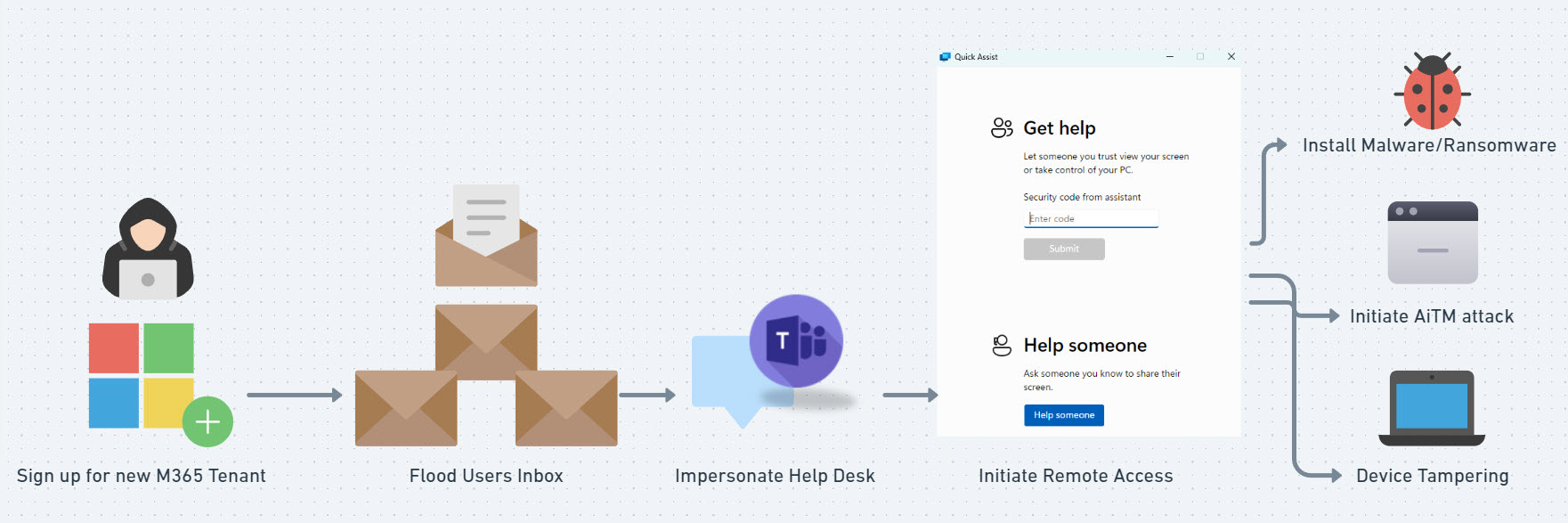
Attack Flow
Default Settings
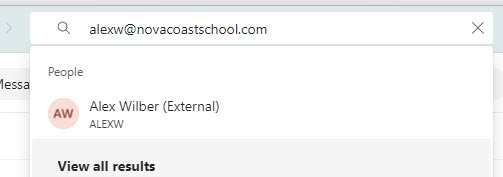
With the default settings in Microsoft 365, any user can search for an external email address in Teams and it will return a value telling you if that user exist or not.
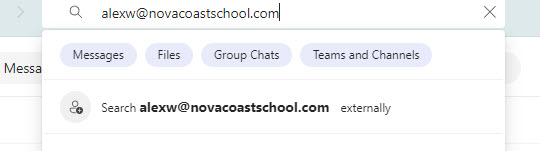
Found and accessible to chat:
Not Found:
By default, users in your organization getting messages from non-whitelisted participants will get a warning to consent before diving into the chat. I think given our typical users track record, they are likely to still blow past this screen.
Protection Runbook
Its important to call out that as of November of 2024, Microsoft has now put default protections as warning messages for users if Microsoft thinks a chat is phishing/impersonation:
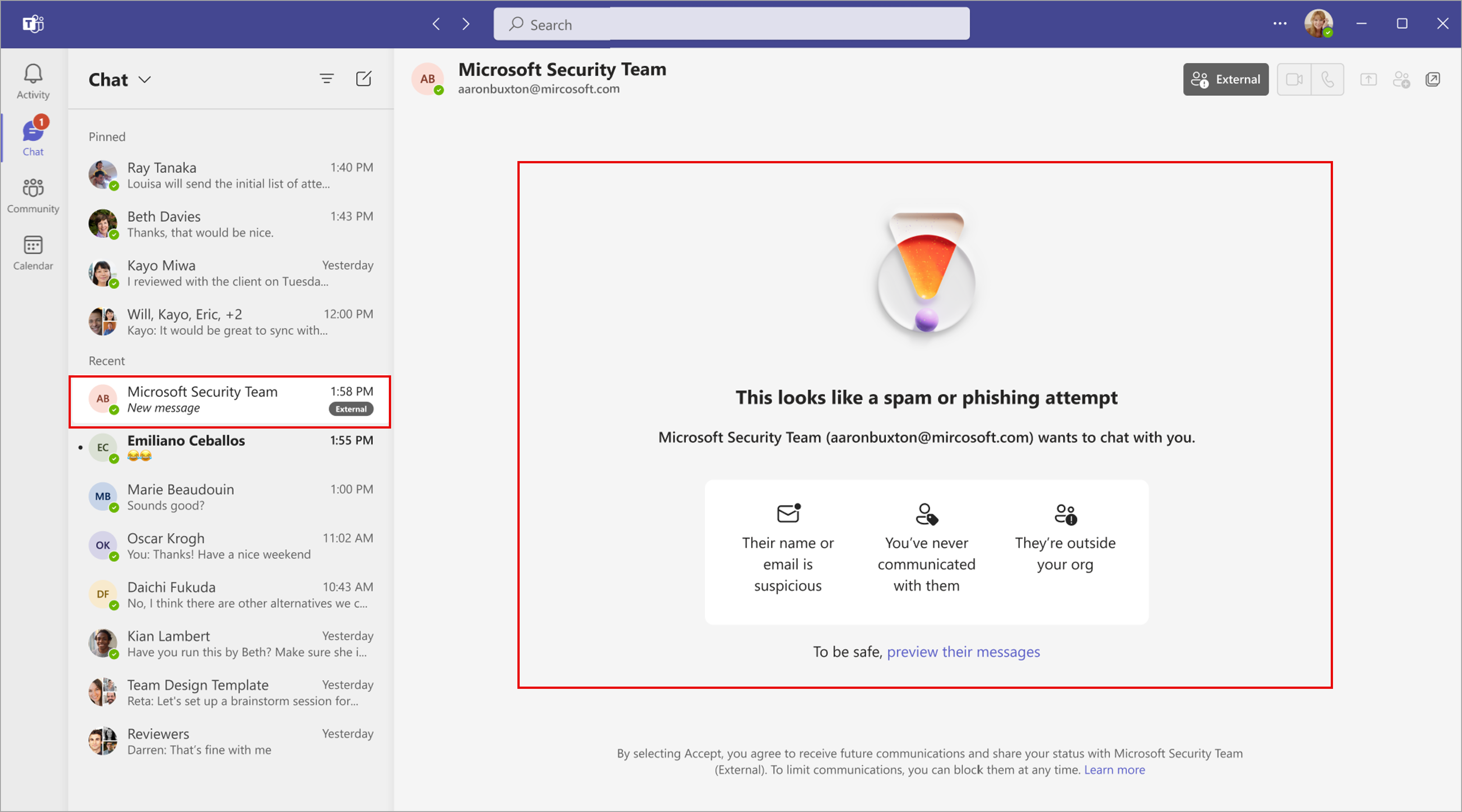
In this example:
- The attacker has added their display name as “Microsoft Security Team”
- Their domain looks like Microsoft.com but is in fact Mircosoft..com
1. Lock down chat with External Users in Teams
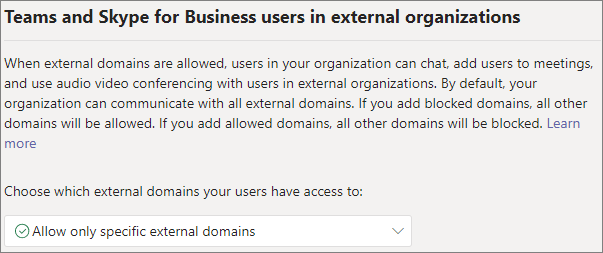
One of the best protections here is to block external users from chatting with members of the internal org unless they are approved and whitelisted:
- Managed Orgs: IT Admins – Manage external meetings and chat with people and organizations using Microsoft identities – Microsoft Teams | Microsoft Learn
- NonManaged Orgs: IT Admins – Manage external meetings and chat with people and organizations using Microsoft identities – Microsoft Teams | Microsoft Learn
2. Uninstall or Disable Quick Assist/RMM tools
Quick Assist is on by default on a Windows Device and is used heavily for this attack but any RMM/remote access tool can be leveraged like Screenconnect, Teamviewer, etc. Ensure that only your approved remote access tool is enabled on the device.

Uninstall/Disable: Use Quick Assist to help users | Microsoft Learn
The following KQL Query can also be used in Defender to hunt/alert for this activity:
Hunt for Teams Activity followed by suspicious RMM:
let interestingUsers = DeviceProcessEvents
| where Timestamp > ago(1h)
| where isnotempty(InitiatingProcessAccountObjectId)
|where FileName has_any (“quickassist.exe”, “anydesk.exe”, “teamviewer_service.exe”) // Multiple RMM tools can be abused here
| project InitiatingProcessAccountUpn;
CloudAppEvents
| where Timestamp > ago(1d)
| where Application == “Microsoft Teams”
| where ActionType == “ChatCreated”
| where isempty(AccountObjectId)
| where RawEventData.ParticipantInfo.HasForeignTenantUsers == true
| where RawEventData.CommunicationType == “OneOnOne”
| where RawEventData.ParticipantInfo.HasGuestUsers == false
| where RawEventData.ParticipantInfo.HasOtherGuestUsers == false
| where AccountId has “@”
| extend TargetUPN = tolower(tostring(RawEventData.Members[1].UPN))
| where TargetUPN in (interestingUsers )
| extend VictimTenant = tostring(RawEventData.OrganizationId)
| extend AttackerTenant = RawEventData.Members[0].OrganizationId
| extend AttackerUPN = RawEventData.Members[0].UPN
| extend AttackerName = RawEventData.Members[0].DisplayName
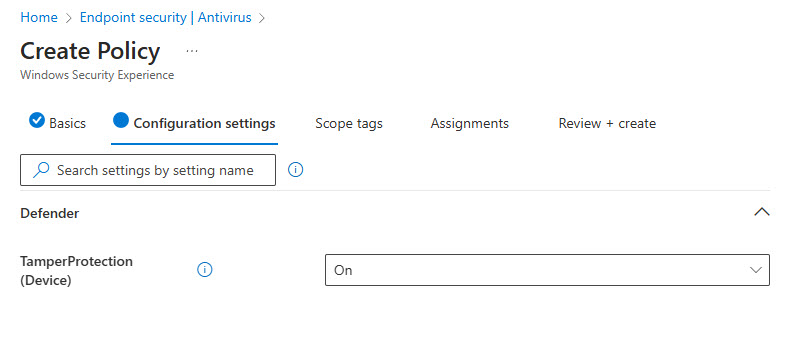
3. Ensure you have Tamper Protection on as part of your windows security settings
Tamper protection is a capability in Microsoft Defender for Endpoint/Defender for Business that helps protect certain security settings, such as virus and threat protection, from being disabled or changed. This would help in the event that the attack gained access to the users device through a remote session and was trying to turn off protections like AV and download malware/ransomware. This can be turned on in the Security Admin Center or Intune. It does require that your devices are enrolled into Defender for Business/Defender for Endpoint.
4. Educate your end-users about tech support scams
As part of our security awareness training, you should be educating your customers/end-users on tech support scams and what to look out for. The following article has some helpful tips:Protect yourself from tech support scams – Microsoft Support
Defense in Depth
I think the above runbook provides good protection but it is obviously not all inclusive of what you can do to help protect this type of attack. Evaluate your security stack to understand what additional layers you can add in here. Examples:
- Ensuring users aren’t local admins on devices
- Using link and attachment protections with Defender for Office 365
- Using Application whitelisting and elevation control on devices
- Using phishing-resistant MFA
