Personal Device Access (By Default)
- AV protections for malware
- EDR tools for Endpoint detection and response
- DNS Filtering Services for secure browsing
- Our RMM for secure configurations and patching
- Application Whitelisting tools for proper elevation control
Policy Decision Matrix
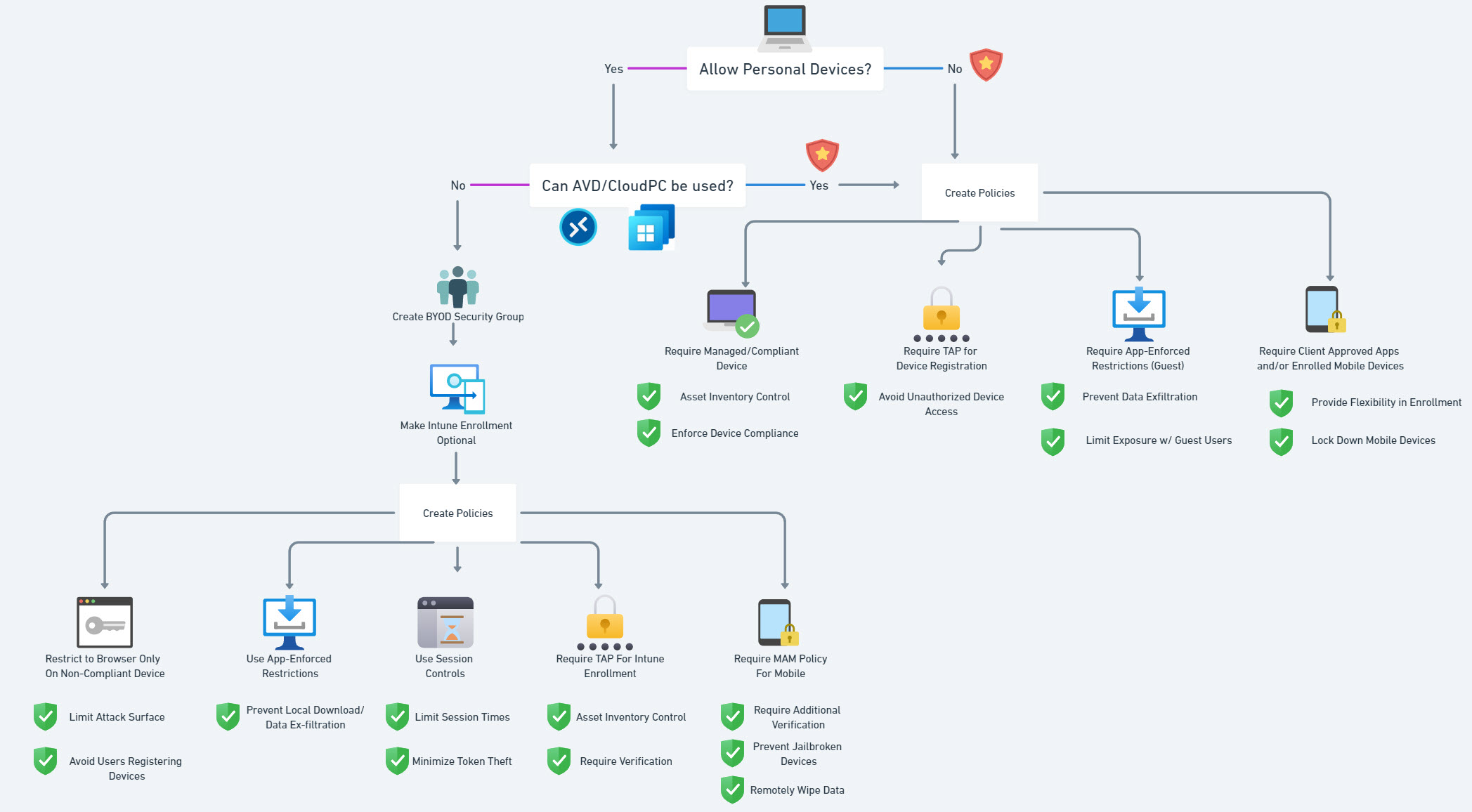
Can AVD/Cloud PC be used?
These solutions containerize our corporate resources, increase our security, and can also be accessed from personal devices. The cons here is that AVD and/or Cloud PC can get expensive to have enough resources for users to have a good experience with these solutions when they are doing basic work tasks like taking a teams meeting. Maybe thats a good thing though to slowly nudge them into using a managed device?
Creating a Personal Device Security Group
The first step is creating a dynamic security group in Entra to segment personal devices from company-owned devices. This group will funnel all non-corporate devices into a distinct group that we can manage with specific security policies.
- Go to Entra Admin Center > Groups and create a new group.
- Set the Membership type to Dynamic Device.
- Add a rule that identifies devices based on their Device Ownership status—filtering for devices not marked as company.
- Save the group, so any personal device entering your system is automatically added.
With this setup, we can apply specific controls, enforce policies, and monitor access for personal devices that might otherwise clutter the company’s asset inventory.
Making Intune Enrollment Optional
I like to make Intune enrollment optional for them to provide them more flexibility in the policies we will be discussing later. An example here would be if a user has enrolled their personal device into Intune and it is compliant, I will not limit their session times to 1-3 hrs because the risk is reduced.
Essential Personal Device Access Security Policies in Microsoft 365
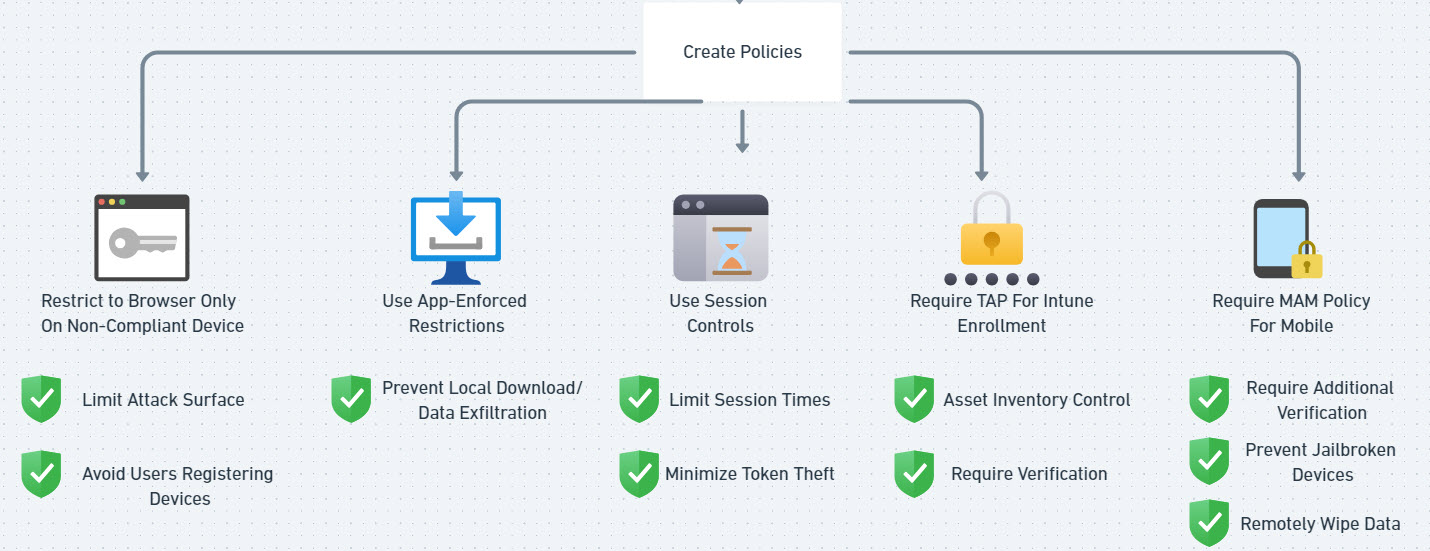
Restrict Access to Web-Only for Non-Compliant (and unmanaged) Devices
- Policy: Configure a conditional access policy to limit access to browser-only views on non-compliant devices, restricting users to web-access only
- Reason: This restriction limits exposure to security threats since data cannot be downloaded directly to the device, client applications cannot be breached, and helps prevent clutter in your Entra environment with unmanaged devices being registered by users.
Use App-Enforced Restrictions
- Policy: Block file downloads from SharePoint and OneDrive on personal devices.
- Reason: This reduces the risk of data exfiltration on devices that aren’t under IT control.
Use Session Controls
- Policy: Set session limits for BYOD access to reduce risks related to token theft or prolonged access on unsecured devices.
- Reason: Shorter session limits ensure that users must authenticate more frequently, minimizing the time that compromised sessions remain active.
Require a Temporary Access Pass (TAP) for Intune Enrollment
- Policy: Require users to verify their device through a Temporary Access Pass when enrolling in Intune.
- Reason: This provides additional security validation, making sure only approved devices can register with your system since your techs have to generate them.
Mobile Application Management for iOS and Android Devices
- Policy: Use Mobile Application Management (MAM) policies in Intune to secure data on mobile devices without full device enrollment.
- Reason: This allows IT to control corporate data on users’ mobile apps, like Outlook, without needing to manage the entire device, which enhances both security and user privacy.
