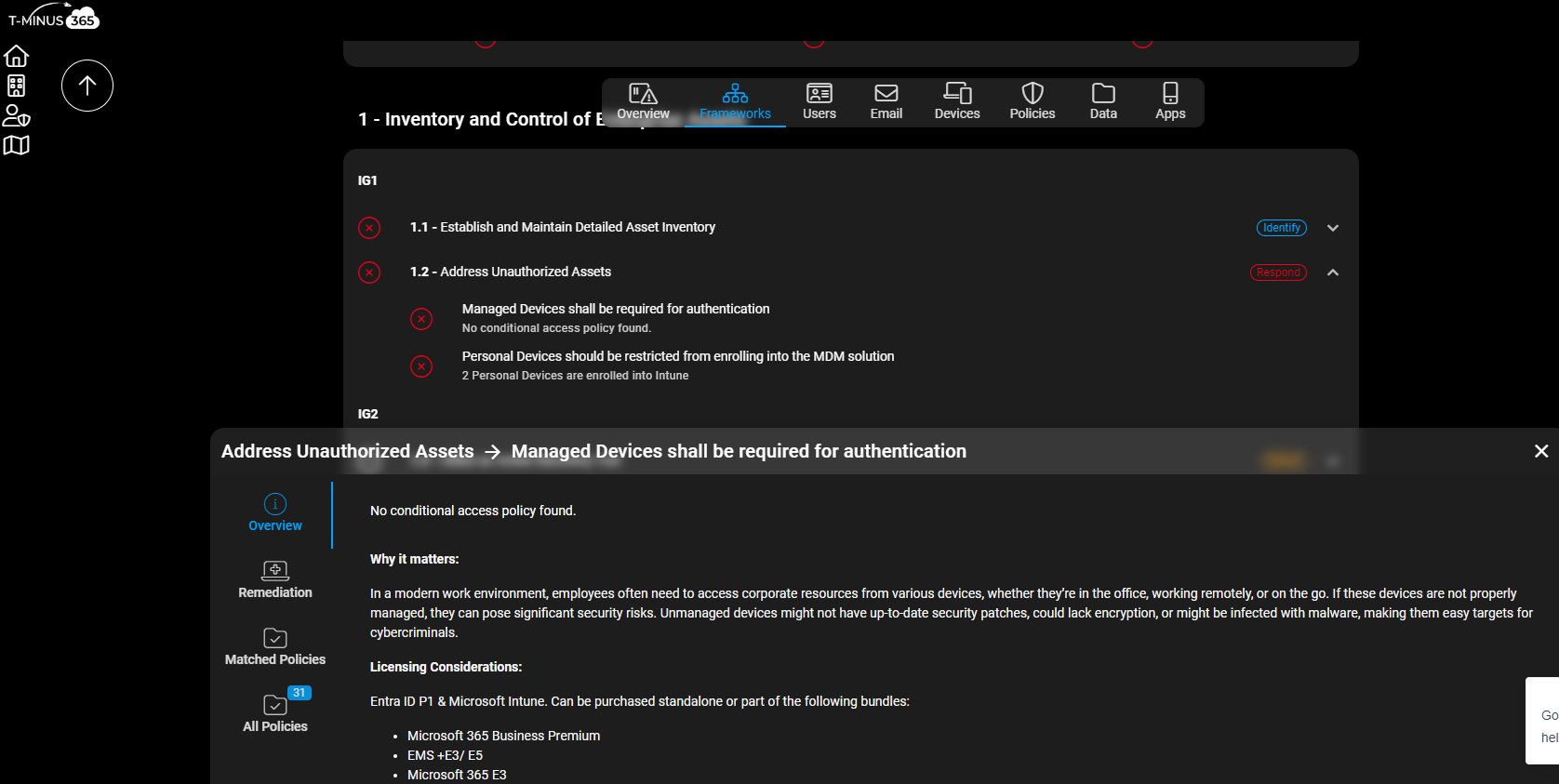
Why Default Device Registration is a Security Risk
Without strict policies, allowing any user to register or join a device creates a “back door” for attackers who might compromise a user account. Here’s why this can be concerning:
- Persistence for Attackers: By joining their own device to your network, attackers can maintain ongoing access without needing to repeatedly compromise accounts.They can hide as a trusted device on the network.
- Cluttered Asset Inventory: Registered personal devices can bloat your asset list, making it harder to keep track of approved, compliant devices.
Let’s dive into policies that can help secure your organization and prevent these vulnerabilities.
Default Settings
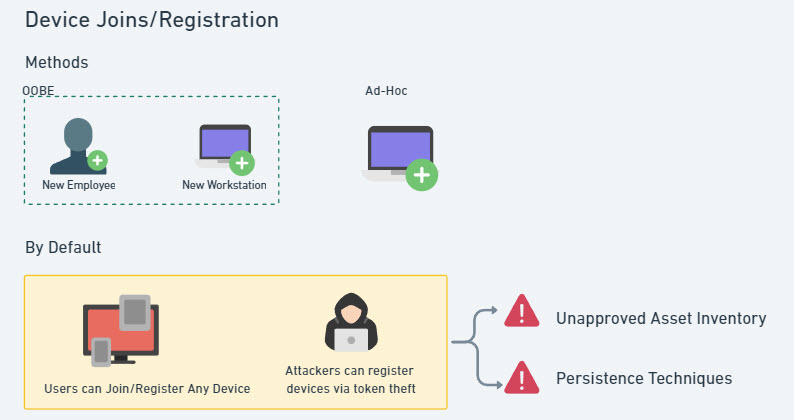
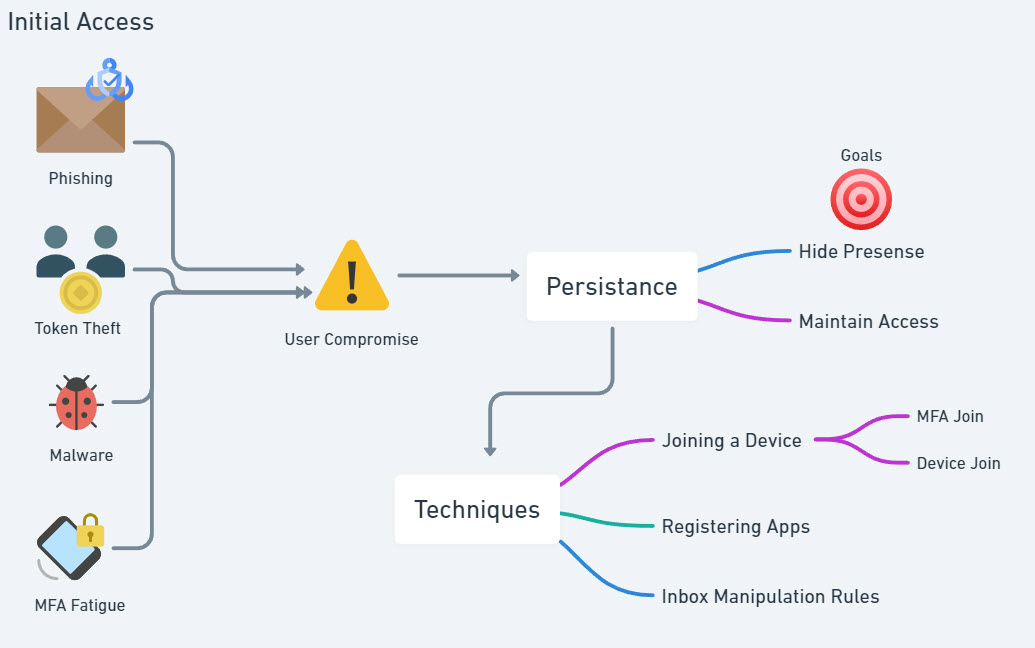
If we think about the common ways devices are joined or registered into Entra today, we really have two major workflows:
- Through the out-of-box-experience when we have a new employee onboard or a new workstation (think of a workstation replacement.)
- Devices are joined or registered ad-hoc
The key thing to note here is that when users sign into desktop applications on any device, they end up getting prompted to register their device with Entra without any type of approval workflow. This is what can lead to an unapproved asset inventory.
Top Policies to Secure Device Registration in Microsoft 365
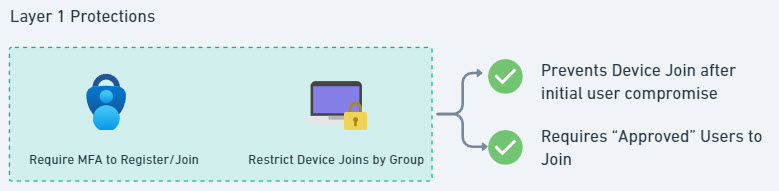
When I talk about “Layer 1” Protections, these are usually settings I usually try to enable by default in every tenant I manage. Layer 2 protections usually are a step up because they include:
- A deeper level of maturity
- A higher impact to end-users
- An inclusion of another SOP to support
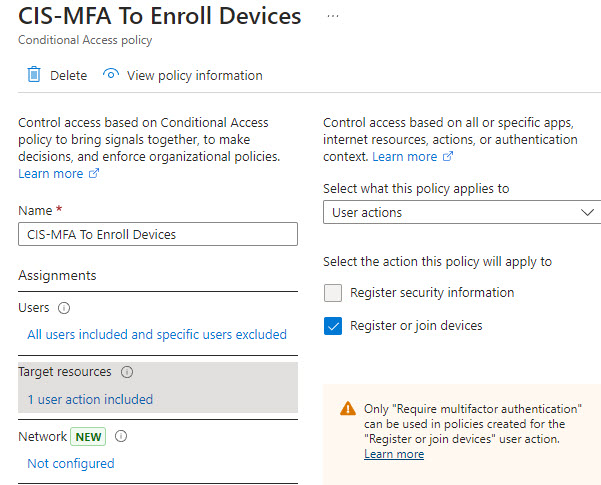
1. Conditional Access Policy for MFA on Device Registration
Adding Multi-Factor Authentication (MFA) for device registration is a simple yet effective way to stop unauthorized devices. By requiring an MFA prompt, even if an attacker has access to a compromised token (think of man-in-the-middle attacks, cookie hijacking, etc.), they’ll face a significant roadblock:
- Use Case: If an attacker tries to register a device, they’ll be prompted for additional MFA, blocking access without the correct credentials.
- Implementation: Create a new Conditional Access policy to enforce MFA for device registrations in Entra ID. This way, any attempt to register a device will require verification beyond just username and password.
2. Restricting Device Joins to Specific Groups
Restricting device joins to an “Approved Users” group helps limit who can add new devices. This control is especially useful for high-security environments or when dealing with contractors or temporary staff. You would have to have a proccess in place for your User onboarding workflow to temporarily add new hire to this group while they get their workstation set up. Here’s how to do it:
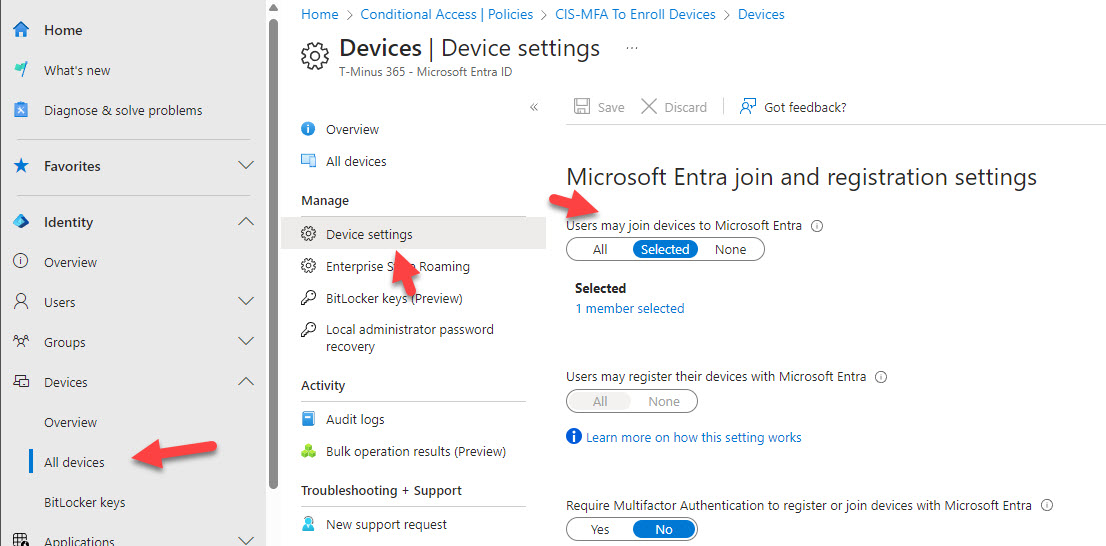
- Implementation: Within Entra ID, configure the “Users may join devices to Entra ID” setting to restrict device registration to a specified group. For example, assign onboarding teams to handle device registrations, limiting broad access.
- Benefit: Only approved users can join devices, reducing the risk of unwanted devices in your environment.
3. Using Temporary Access Pass (TAP) for Device Registration
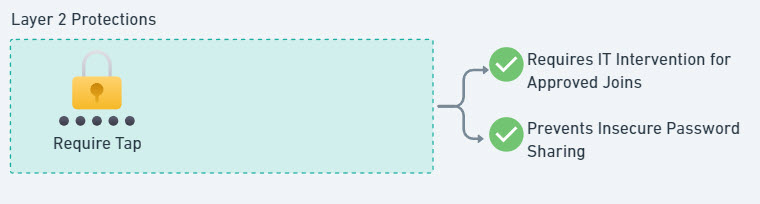
For a more secure approach, consider using a Temporary Access Pass (TAP) to authorize device registrations. This method not only reduces password sharing risks on initial new hire onboarding but also ensures each registration window is temporary and verified by IT. This would ensure that users can’t blindly register any device to Entra:
- How It Works: IT generates a TAP with a limited time window for use, allowing new employees or devices to authenticate securely. This time-sensitive pass also limits the potential for device persistence by attackers.
- Implementation: In Entra ID, in the Authentication Methods section, ensure that TAP is activated under policies. Configure an authentication strength for TAP that you can apply in conditional access. Set up a TAP authentication strength under Conditional Access policies specificly for the user action of register or join devices just like we did for the first recommended policy. This setting ensures device registration is restricted to a temporary pass managed by IT.
- Added Security: TAP requires coordination with IT, ensuring device registrations are secure and controlled.
Tooling to help discover these policies
If you are looking for a tool to help you understand if you have these policies deployed across one to many tenants, check out a tool I built called CloudCapsule, which automates Microsoft 365 security assessments. You can get a tenant connected and within minutes, have a full security report mapped to the CIS Controls.