In today’s digital landscape, securing local admin accounts is paramount. Mismanagement of these accounts can lead to severe security breaches, compromising sensitive data and systems. What are your standards when it comes to managing local admin passwords and accounts? This article outlines best practices for managing these accounts and passwords securely, alongside effective troubleshooting, preventative, and reactive business practices. We’re going to take a look at Microsoft’s 1st party solutions for managing these accounts/passwords along with the most common 3rd party solutions for MSPs.
Common Bad Practices with Local Admin Passwords
Using the same passwords across devices
Reusing the same password for multiple devices is a risky practice. It means if one device is compromised, all other devices using the same password are also at risk. This significantly amplifies the potential impact of a breach. I think most of us have moved past this bad practice but I still see it in some environments
Storing and using passwords insecurely
How are you storing local admin passwords today? In RMM? in a documentation tool like ITG? in a Password Manager? Do you have any ACLs around techs accessing these passwords? Likely the storage location is not itself at risk but the access controls around the solution.
Using insecure passwords/not rotating
How complex are your passwords? How frequently (if at all) are you rotating them? The rotation of passwords is likely where we have a big gap today.
Best Practices
Dedicated Admin Accounts
Do you know that users across customers do not have local admin rights? Do you have a dedicated admin account on each device? These accounts should be dedicated and documented in the case of a breach with proper audit logging being tied to them.
Complex Passwords
Periodic Password Rotation
Encryption
In legacy times with local active directory, these passwords were stored as an attribute on user records in plain text. We can now encrypt these passwords at rest and they are natively encrypted in Microsoft Entra. Windows LAPS passwords are always protected in transit (https) when sent from the managed device to the cloud. Windows LAPS passwords that are stored in the cloud are always encrypted with AES256
Just-in-time (JIT) access
Audit logging
Implement robust audit logging to monitor the use of admin credentials. Logs should capture who accessed what resources and when, helping to detect and respond to unauthorized activities promptly. This is generally a gap I see in the industry today.
When are we using these accounts?
- Troubleshooting/Break-Fix
- Application install/Program changes
Preventative Mindset
Zero-Trust Mentality
Controlled Folder Access
Enable controlled folder access to protect sensitive directories from unauthorized modifications and ransomware attacks. This is available with attack surface reduction rules in Business Premium.
Application Whitelisting/Ring-fencing
Process Manipulation Blocklist/Allow List
Is EDR enough?
Reactive Considerations
- Elevation Control Management
- Remote access management
1st party bundles
- LAPS
- Windows Local Admin Password Solution (LAPS) is a great solution built into Entra and Intune that supports both Cloud-Native and Hybrid environments.
- Local admin passwords can be managed centrally in Intune and you can define policy to automatically rotate them on a periodic basis and after they are used to login to a device
- Intune EPM
- Endpoint Privilege Management is a new(er) solution that is an add-on you can purchase which allows for just-in-time elevation on devices so that users can have temporary privileges on devices to do things like install the apps they need.
- Intune Remote Help
- This is Intune’s native remote access solution that allows techs to remotely access devices.
- GDAP/PIM
- Using GDAP and PIM within your partner account, you could actually create a system around limited, just-in-time access for when technicians are access local admin passwords in Intune. Using the Cloud Device Administrator or Intune Service Administrator roles paired with a PIM enabled group, you could effectively create a solution that allows techs to PIM into groups that can access local admin passwords when needed but not have access the other 99% of the time.
- LAPS
My recommended LAPS policy settings:
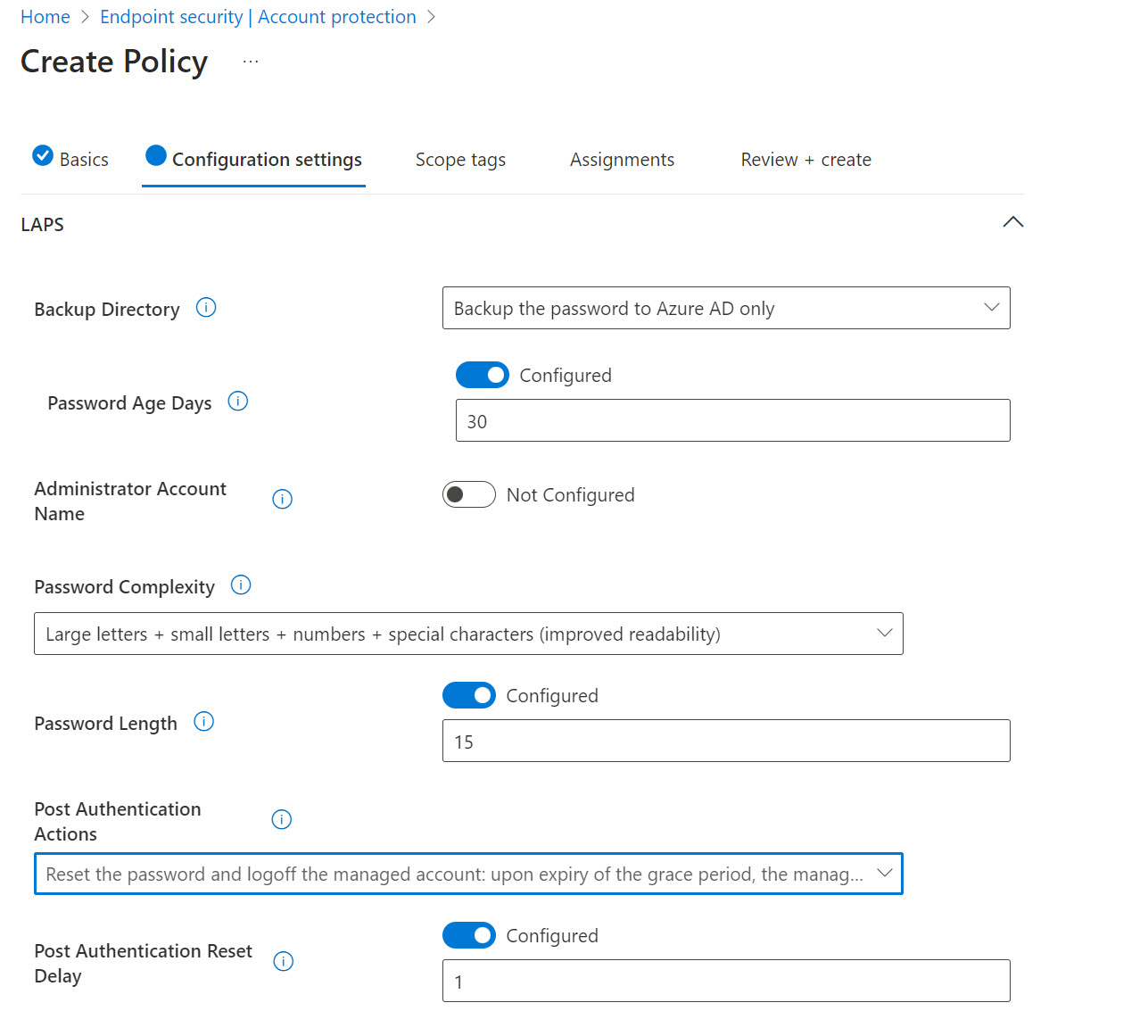
- Its all native. No agents. No extension to 3rd party risk.
- Not multi-tenant capable
- Not tied into our MSP tools like ticketing. Huge deal to operationalize.
- GDAP/PIM may be considered to be too high of an operational burden compared to managing these passwords in our documentation tool (although I would consider that less secure)
- It’s expensive. See pricing here. This is one of the biggest barriers to entry still. While LAPs is free, EPM ($3/e/m) and Remote Help ($3.50/e/m) equate to at least a 33% increase in cost in most cases vs what we are paying for 3rd party that are more MSP friendly.
- Products are still relatively new. EPM and Remote Help have only been out for about a year. Like all Microsoft products, it takes time for me to really trust that there won’t be some glaring gaps in consistent performance.
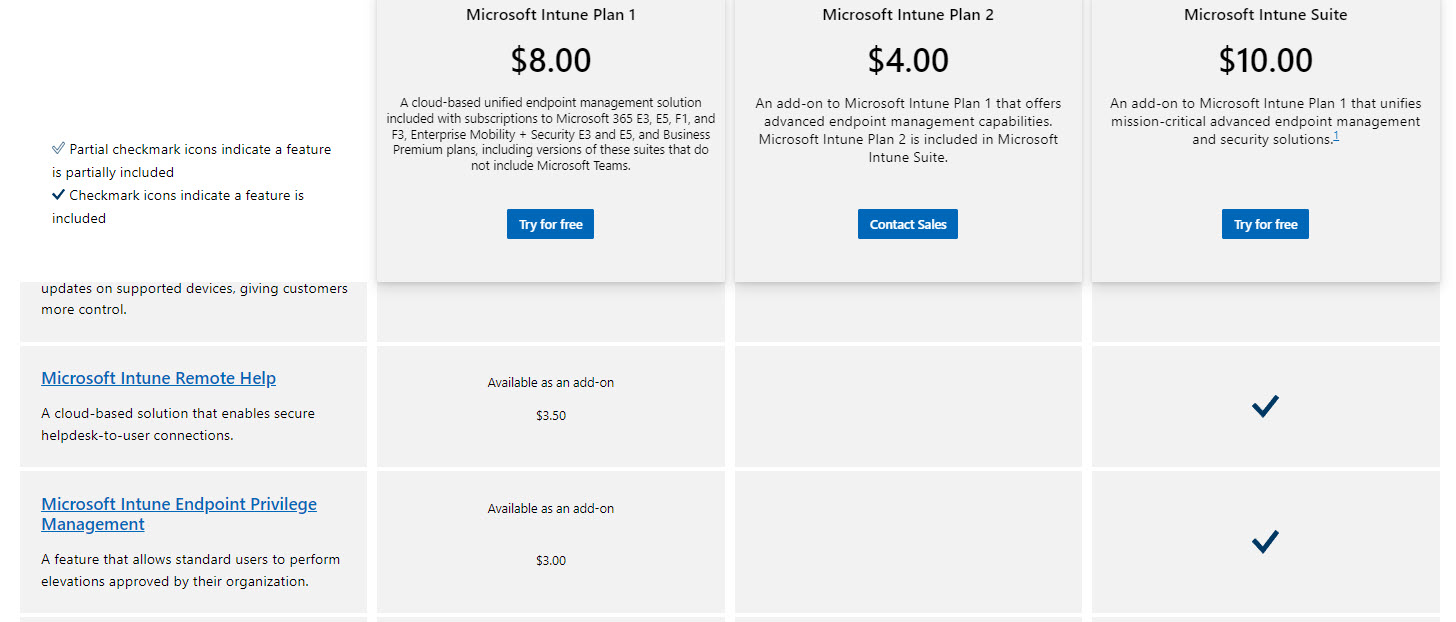
3rd Party Bundles
- CyberQP
- CyberFox
- Threatlocker
- Pros (not all inclusive but what I want to highlight)
- Multi-tenant capable
- Extend to server/db password management. We don’t get that today in a central solution with Intune as an example.
- Integration to our tools like PSA for Ticketing, Documentation tools
- Heighted capabilities like JIT built in.
- Managed response offerings => Some of these companies are introducing a managed response offering for the elevation request that come in allowing us to offboard that support burden (for a fee of course)
- Cons
- Require another agent. This is the biggest downside in my opinion. Yet another risk we are adding to our devices.
- Some of the core features are duplicitous with what you can get for free in LAPS. Thinking about TCO here.
- Pros (not all inclusive but what I want to highlight)
Conclusion
Managing local admin accounts securely is a critical component of a robust cybersecurity strategy. Leveraging tools like LAPS, Intune, and third-party solutions can further enhance security and streamline local account best practices.
Until Microsoft makes 1st party more cost-effective, I believe we will continue to see most of us adopt 3rd party.
