The Nigerian price scam is probably one of the most well known phishing emails out there today but all memes aside, over 90% of all cyberattacks begin with phishing. In this article, I am going to show you how your Microsoft email settings are NOT secure by default and the top 5 recommended settings I would turn on for maximum email security. These security settings will help boost your Secure score in Microsoft by over 70 points.
What is phishing?
Phishing is still so popular because it cannot be stopped with technology alone. The basis of phishing plays on human psychology in order to trick individuals into taking some action. Lets talk about 4 common traits with phishing attacks and take a look at a few phishing examples to showcase these traits

- Impersonation => Attackers will try to impersonate other individuals or organizations either through disguising the from address of the email or the body of the email itself. In this example, we are seeing the attacker trying to disguise the body of the email to make it look like its coming from chase bank. This could also be disguised to look like its coming from the CEO of the company or another users like someone in finance
- Sense of urgency => “The ATM withdrawal or debit card purchase exceeds that amount you have chosen” messaging incites fear and can be used to cause the user to want to take action
- Request of sensitive information => In this case, the attacker is trying to get the user to click on a link likely to take them to a fake website that looks like chase, to enter their username and password
- Links or Attachments => Often cases, malicious links are hidden in the email and are used to download malicious payloads to a users device or get them to go to a malicious website to harvest more information.
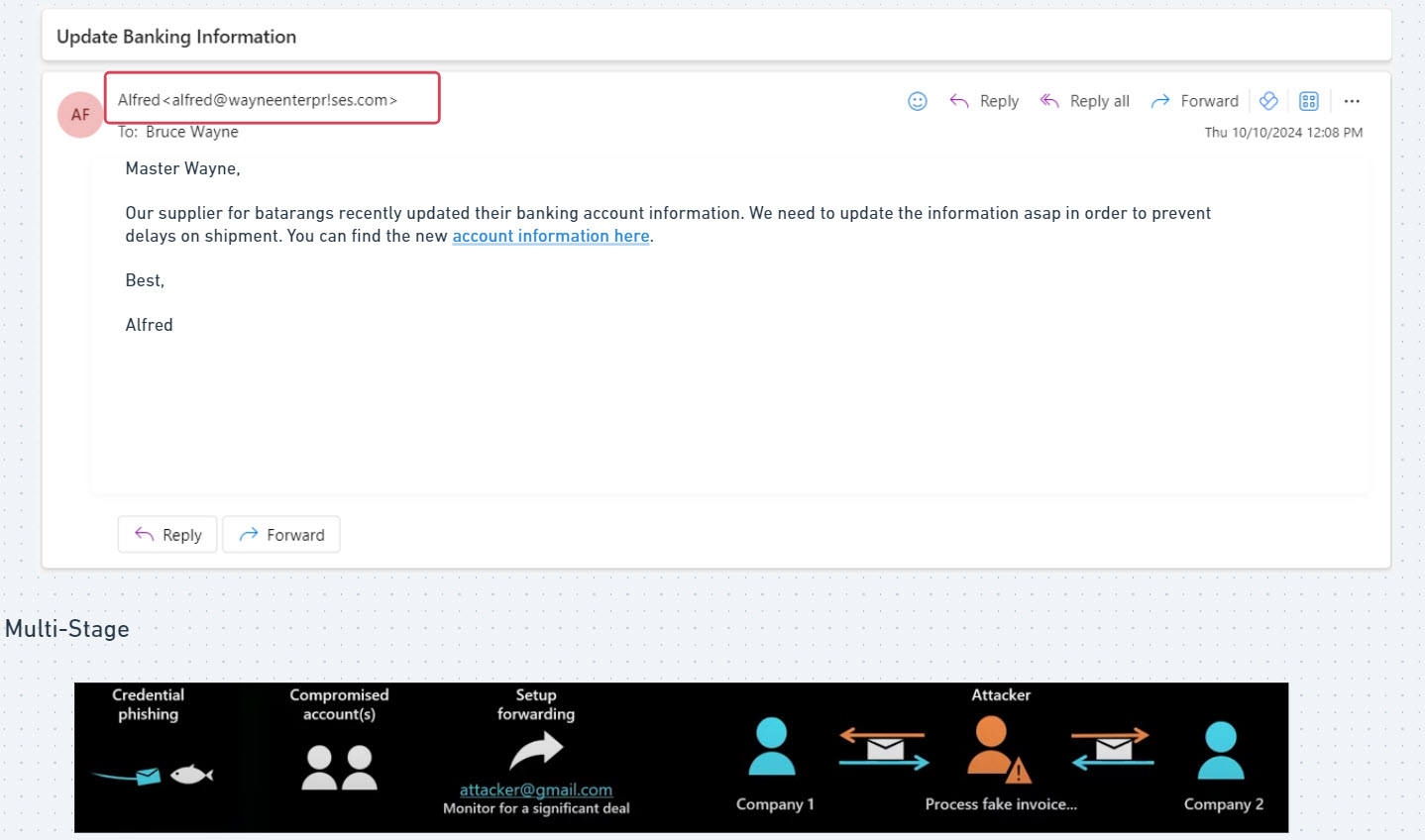
In the small business world, we see phishing attacks where attackers are trying to disguise themselves as the high profile users in the organization or HR to try and influence the user to take some action. In many cases, that is getting them to wire or send money to a new entity. I’ve talked to many organizations who have been subject to wiring hundreds of thousands of dollars to a malicious bank account.
Exchange Online Protection vs Defender For Office 365
Exchange Online Protection comes with baseline policies set up for:
- Anti-spam
- Anti-Malware
- Anti-phishing
Some of the policy configurations I will be showing you can be done with base level license that does not require Defender for Office365. I would say though if you care about security, Exchange Online Protection is not enough. You need to be using an advanced email security solution like Defender for Office 365 or a 3rd party. Defender for Office 365 includes more advanced settings for security included advanced phishing protections for impersonation and spoofing, along with policies for secure scanning for links and attachments.
As we take a look at some of the recommended settings, its important to note that as with all things security, we are trying to dial our security nobs so that users are protected without completely shutting down productivity. Microsoft email security is notorious for either catching a bunch of emails as false positives
Or letting a bunch of blatant phishing emails through
For this reason, the security settings we configure are going to be somewhat variable depending on the environment and the kinds of attacks we are seeing over time. We will cover the reporting you can view later in the article for continuous improvement.
5 Recommended Security Configurations
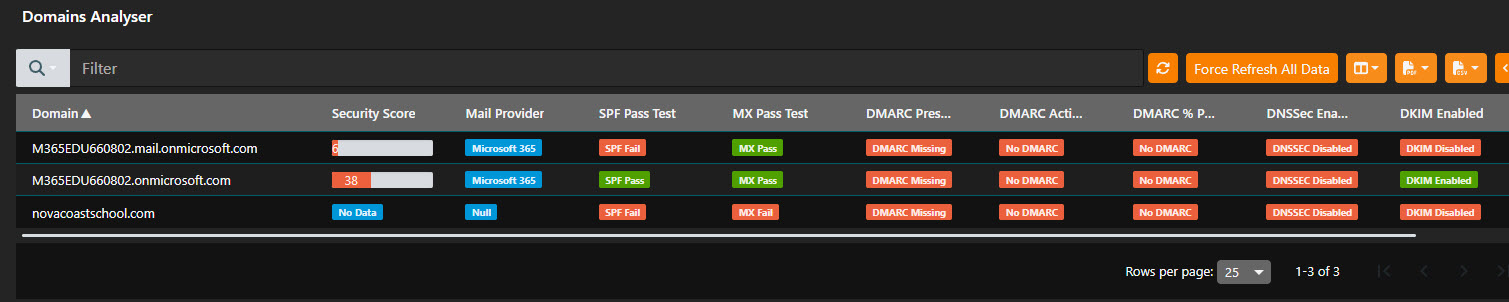
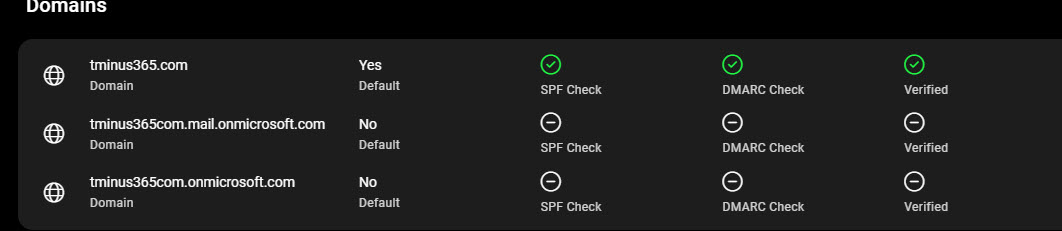
1. SPF, DKIM, and DMARC
Think of your email system like a postal service. SPF, DKIM, and DMARC are like different security checks at the post office to make sure the mail you’re getting is actually from who it says it is.
- SPF is like checking the return address on an envelope. It makes sure that the mail server sending the email is authorized to send mail for that domain.
- DKIM is like sealing the envelope with a unique stamp. It proves that the email hasn’t been tampered with during transit.
DMARC is like the postmaster who decides what to do with the email if SPF or DKIM checks fail—either reject it, quarantine it, or let it through.
These records should be added to every custom domain within your Microsoft 365 Environment.
Back to our example of someone trying to spoof or impersonate someone’s domain, SPF, DKIM, and DMARC could help prevent the mail from being delivered altogether and instead be rejected or quarantined.
How to Configure:
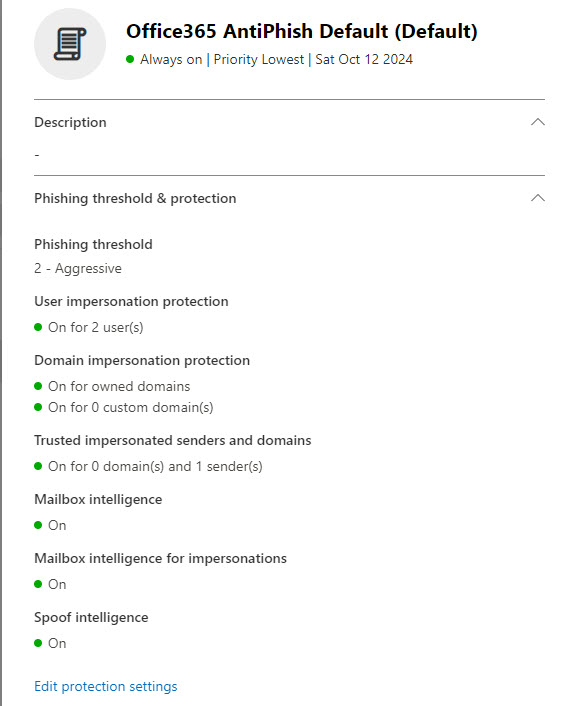
2. Adjust the Default Anti-phishing Policy
I usually just modify the default policy in the environment, but you could also create a new policy as well. As a general principle, I do not use the Strict or Standard preset policies. These come with a lack of control that I do not care for. Here are the settings I modify in the default Anti-phishing policy in the Defender Admin Center:
- Set the phishing email level threshold at 2 or higher
- Enable impersonated user protection
- Enable impersonated domain protection
- Ensure that intelligence for impersonation protection is enabled
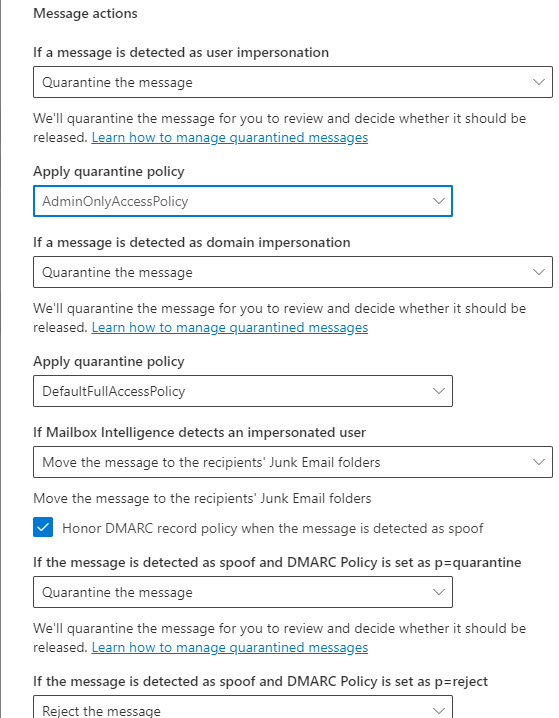
- Move messages that are detected as impersonated users by mailbox intelligence
- Quarantine messages that are detected from impersonated domains
- Quarantine messages that are detected from impersonated users
- Enable the user impersonation safety tip
- Enable the domain impersonation safety tip
- Enable the user impersonation unusual characters safety tip
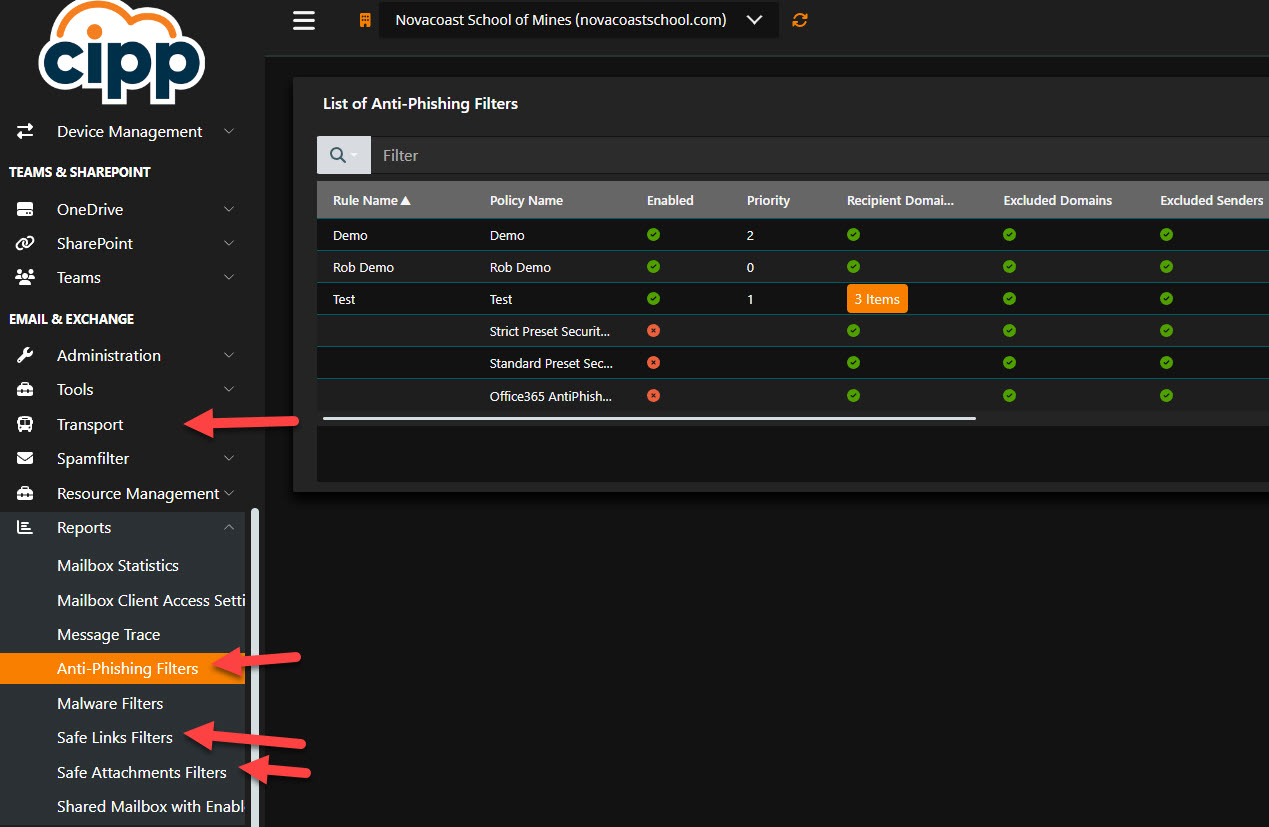
3. Create Policies for Safe Links and Safe Attachments
When we talk about defense in depth, Safe links and safe attachment protection are a great example where we might have email that is still delivered to end-users but we want further scanning and/or protection for links in the email or malicious attachments. These polices that are part of Defender for 365 allow for url scanning and scanning of attachments to further identify malicious or suspicious activity.
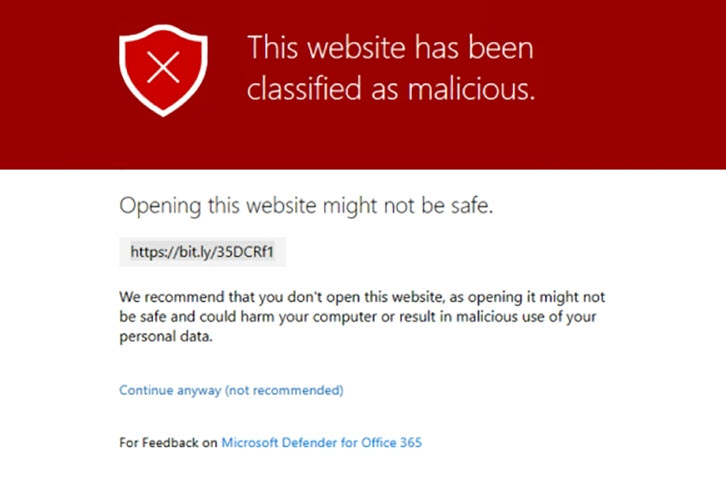
Settings:
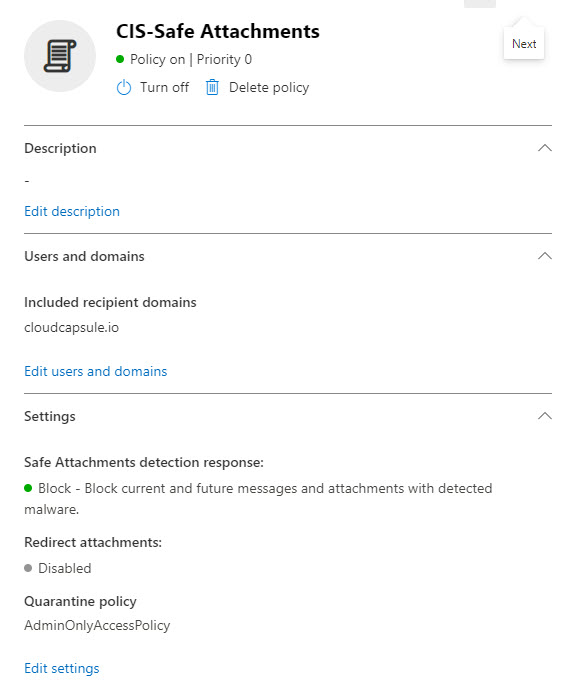
- Ensure the Safe Attachments policy is set to Block
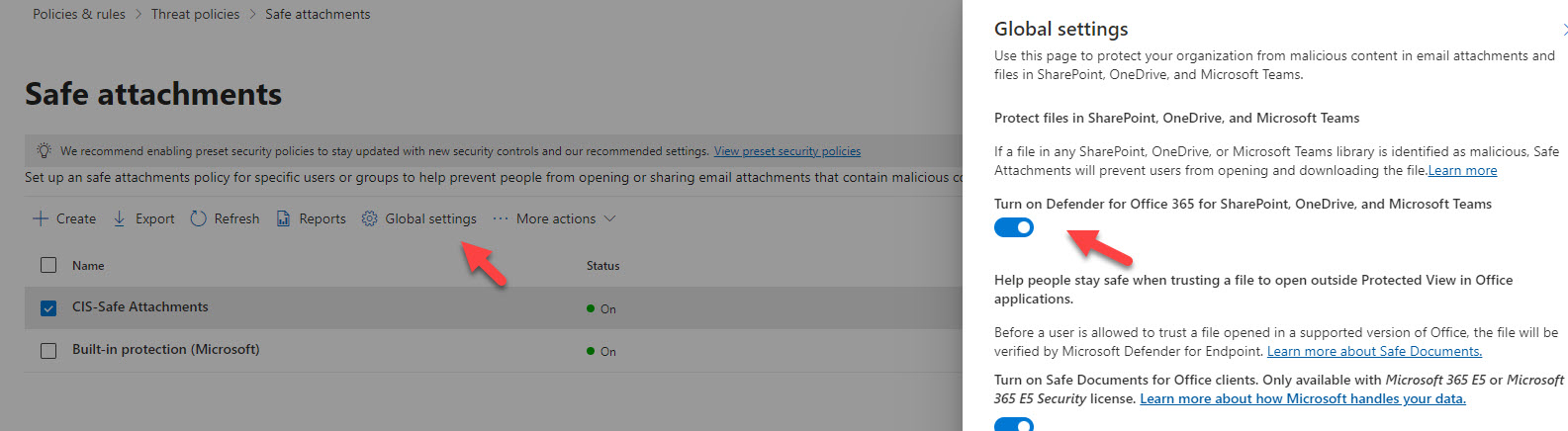
- Turn on Safe Attachments in the Global Settings for SP, OD, and Teams
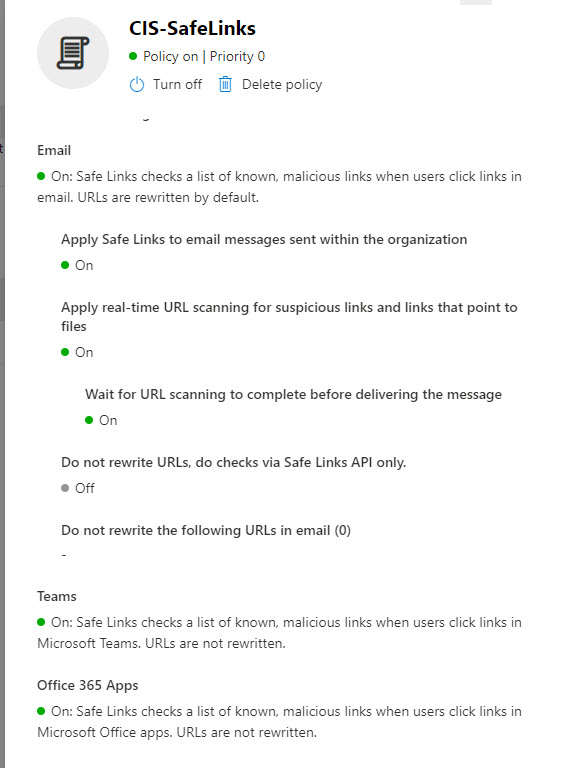
- Ensure Safe Links Policy:
- Is Unchecked for “Do no rewrite URLs
- Is Unchecked for Let users click through to the original URL
4. Set up External Sender Warnings
So far we have looked at protections that help prevent or detect for malicious activity. As I mentioned at the beginning of the article, phishing is unique in that it plays on the psychology of users. For this reason, we also want to put in some protections to help our users identify suspicious activity in email. This first setting we are going to look at is external sending warnings. This adds a tag to email messages and a banner message in the email body. It’s great for helping users identify potential malicious spoofing or impersonation.
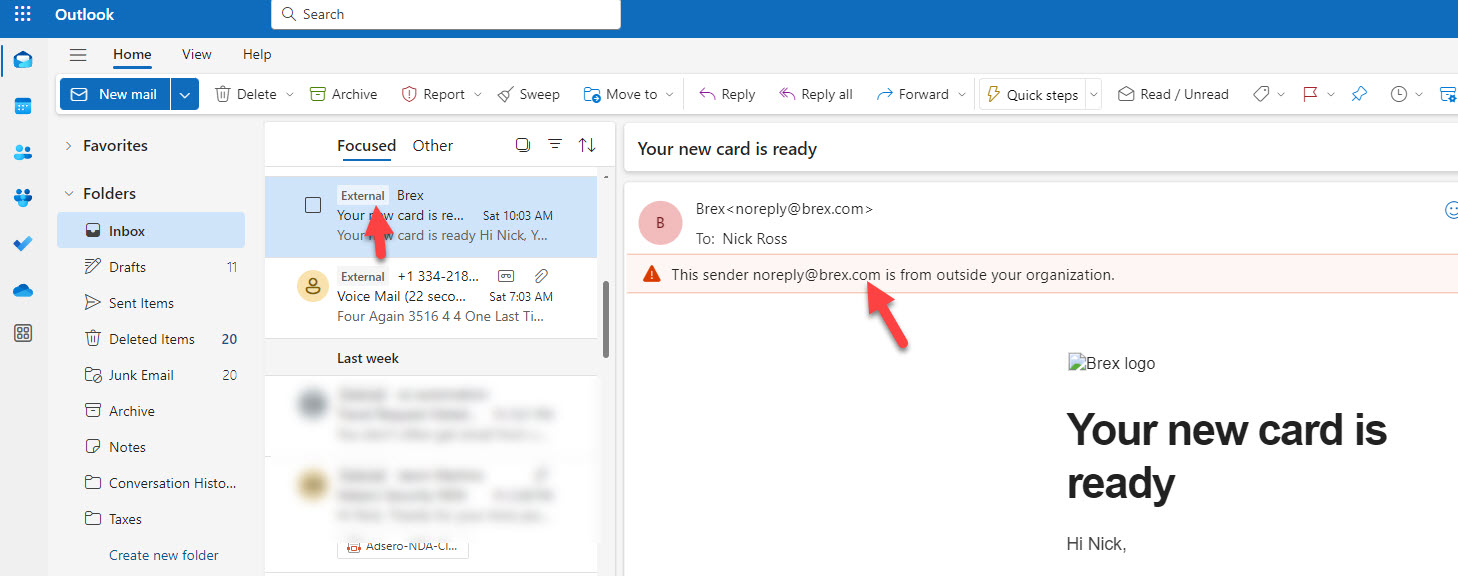
To set this up:
- Exchange Online tenant admin will need to run the cmdlet Set-ExternalInOutlook to enable the new user interface for the whole tenant (this is available now); adding certain emails and domains to the allow list via the cmdlet is also possible.
5. Set up Mail flow rules for sensitive keywords
This last setting I am going to show also gives users some helpful warnings based on the content coming through. Since we see so many attacks where users alter bank account information, I want to leverage Mailflow rules to provide the user more helpful context based on text in the subject or body.
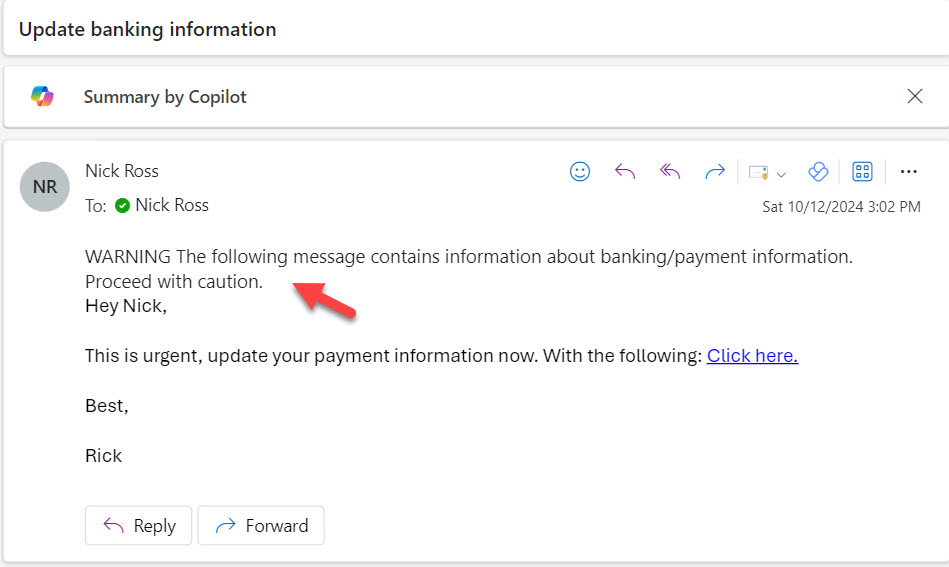
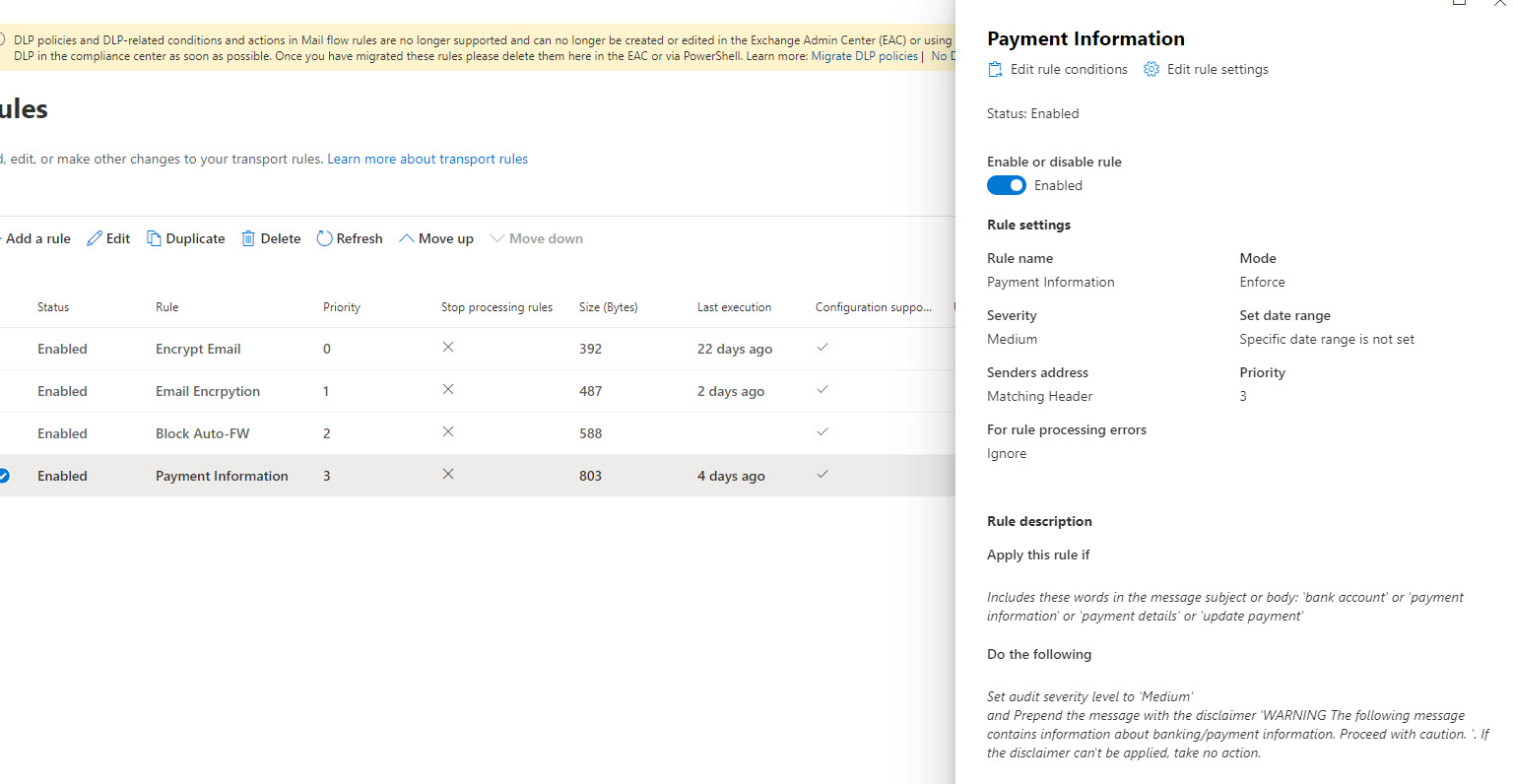
How to Configure:
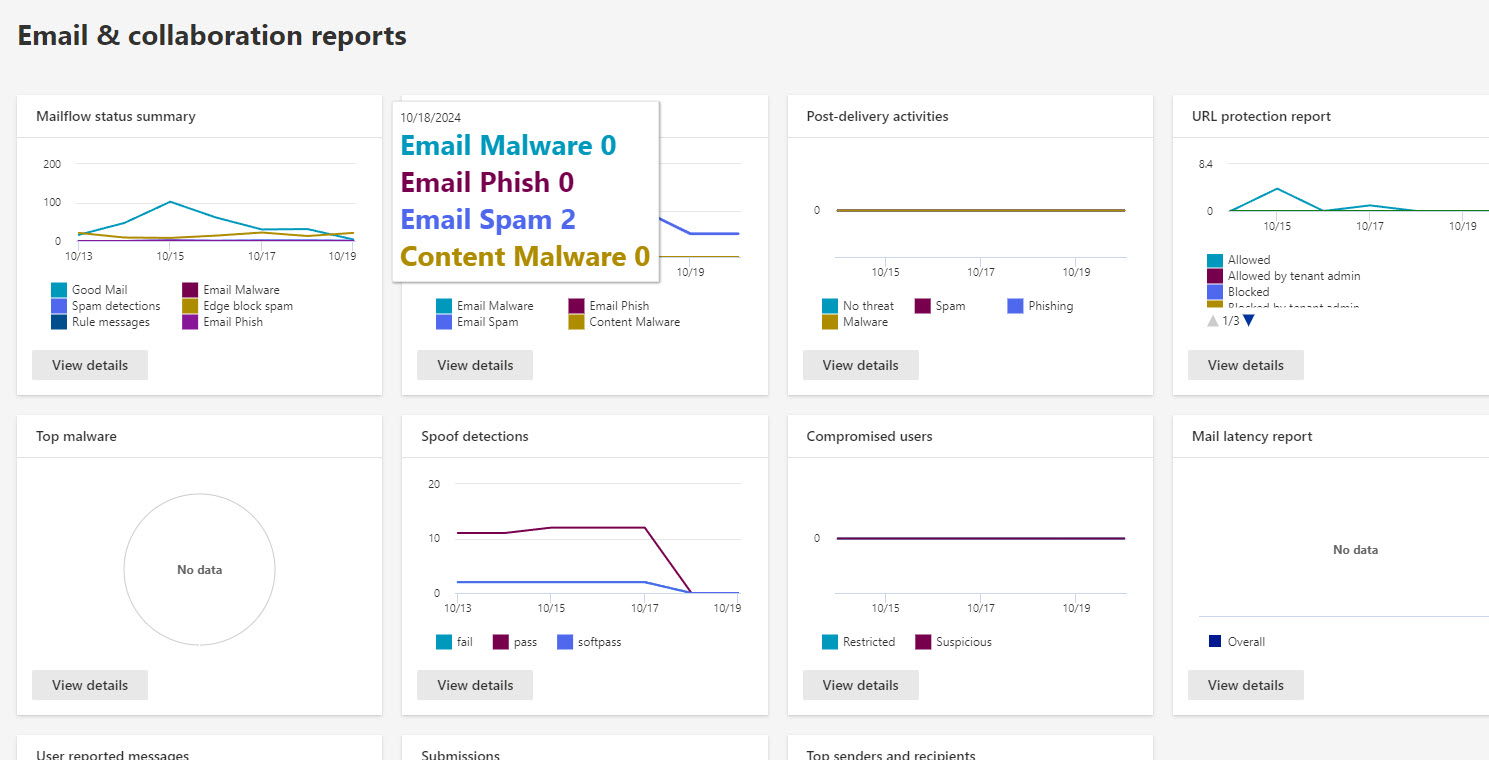
Monitoring for Continuous Improvement
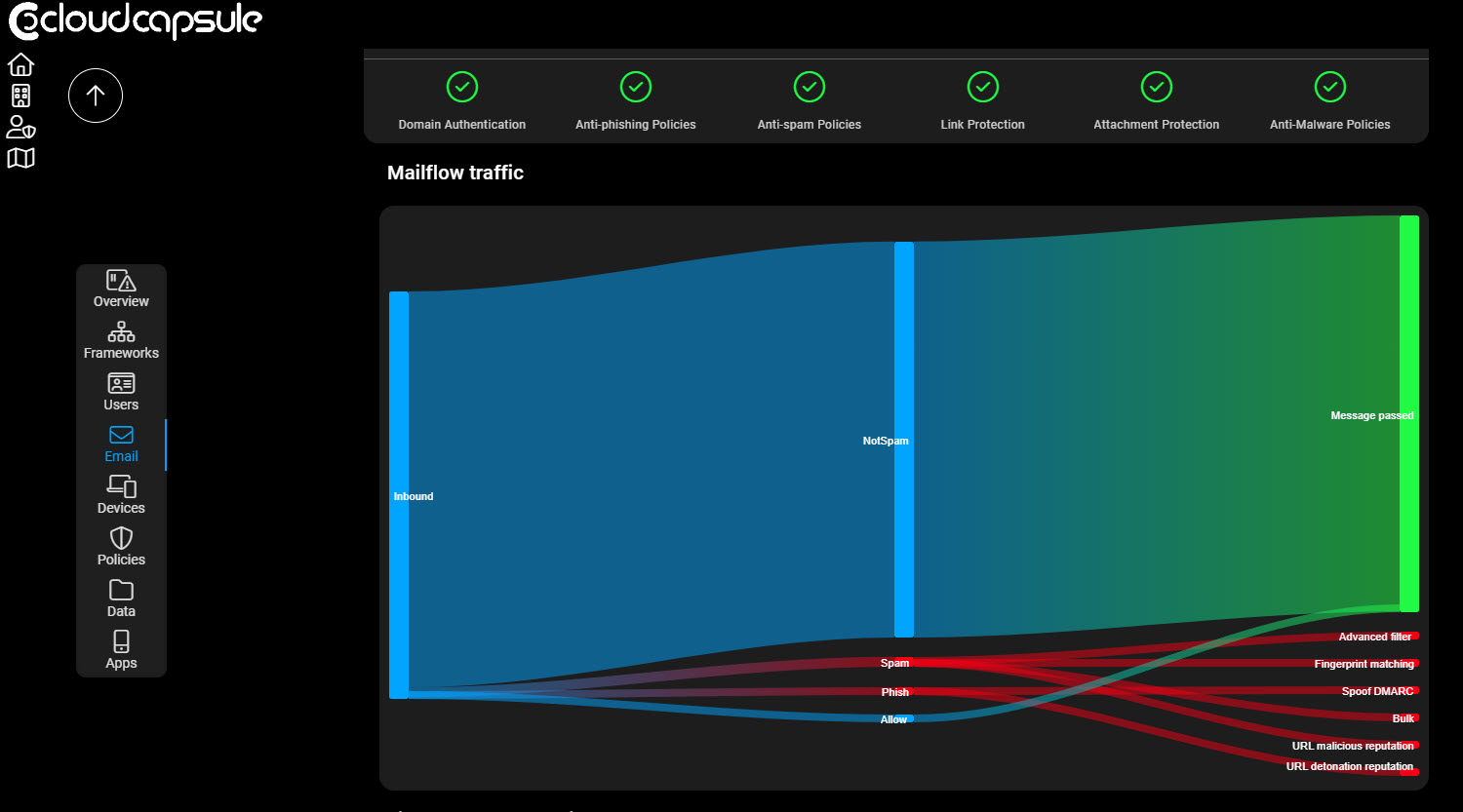
You can monitor the traffic in the tenant as well as all email captured in Junk/Quarantine within the Security admin center
- Go to Security & Compliance
- Click Reports (Bottom of Nav)
- Scroll to Email and & Collaboration Reports
Here you can review thinks like the healthy vs unhealthy mail, spoof detections, URL clicks, and more.
3 Party tools for Help Monitoring
1. CloudCapsule
This is a tool that I built that automated M365 Security assessments. It will specifically look for many of the settings we talked about here as checks of compliance.
2. CIPP
The Cyberdrain Improved Partner Portal (CIPP) is an open source tool that provides great multi-tenant management capabilities to administer Microsoft 365 across customers. It has reporting and policy configuration capabilities for the settings we are talking about on a multi-tenant layer.