Considerations
MFA Enforcement has evolved over time. Stop using per-user MFA.
- Enabled => Required users to perform MFA immediately across all logins
- Enforced => Allowed users to defer registering for MFA for 14 days
- Disabled => MFA not enforced
Conditional Access can quickly become swiss cheese. Ensure you have a blanket MFA policy for All Users.
- Temporarily adding users to overcome some operational constraint where MFA needs to be bypassed
- Users being excluded as they are going on international travel
- Inadvertent exclusions through group membership
- Includes All Users, only excludes break glass accounts
- Includes All Applications
- Does not whitelist any Networks to exclude from enforcement
- Does not have any other filtering going on
- Requires MFA in the Grant controls
MFA methods and the evolving attack surface
- Disabled SMS, Voice Call, and Email OTP
- Disable OTP on Authenticator and make sure number matching has been enabled
- Try to enforce phishing-resistant forms of MFA for Admin accounts (ex. FIDO2 keys/Passkeys for Global Admins)
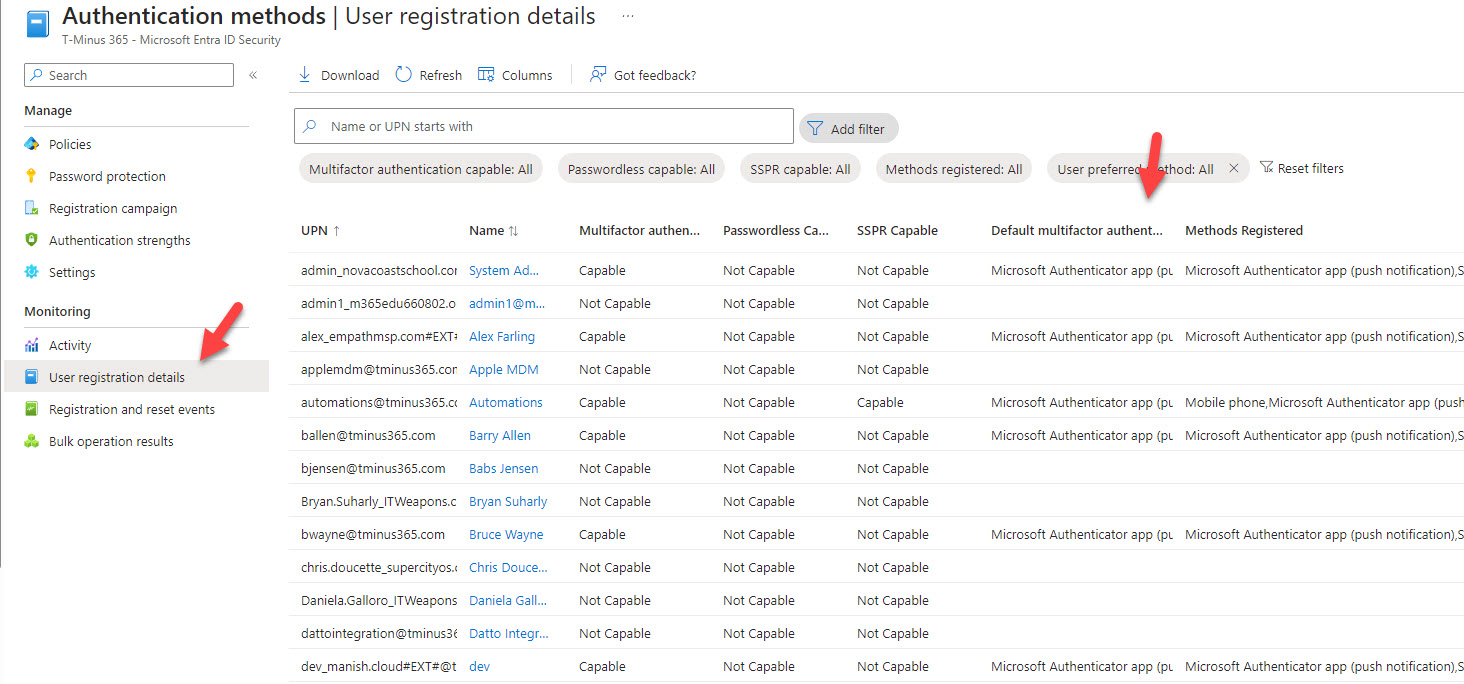
There is no central MFA report
- The user has signed-in at least once
- They have some type of enforcement being applied that would have them register for MFA
- is this a licensed user
- is this a shared mailbox
- is this a service account
- is this a break glass account
- is the account enabled
Entra ID logs can help but are a lot of noise
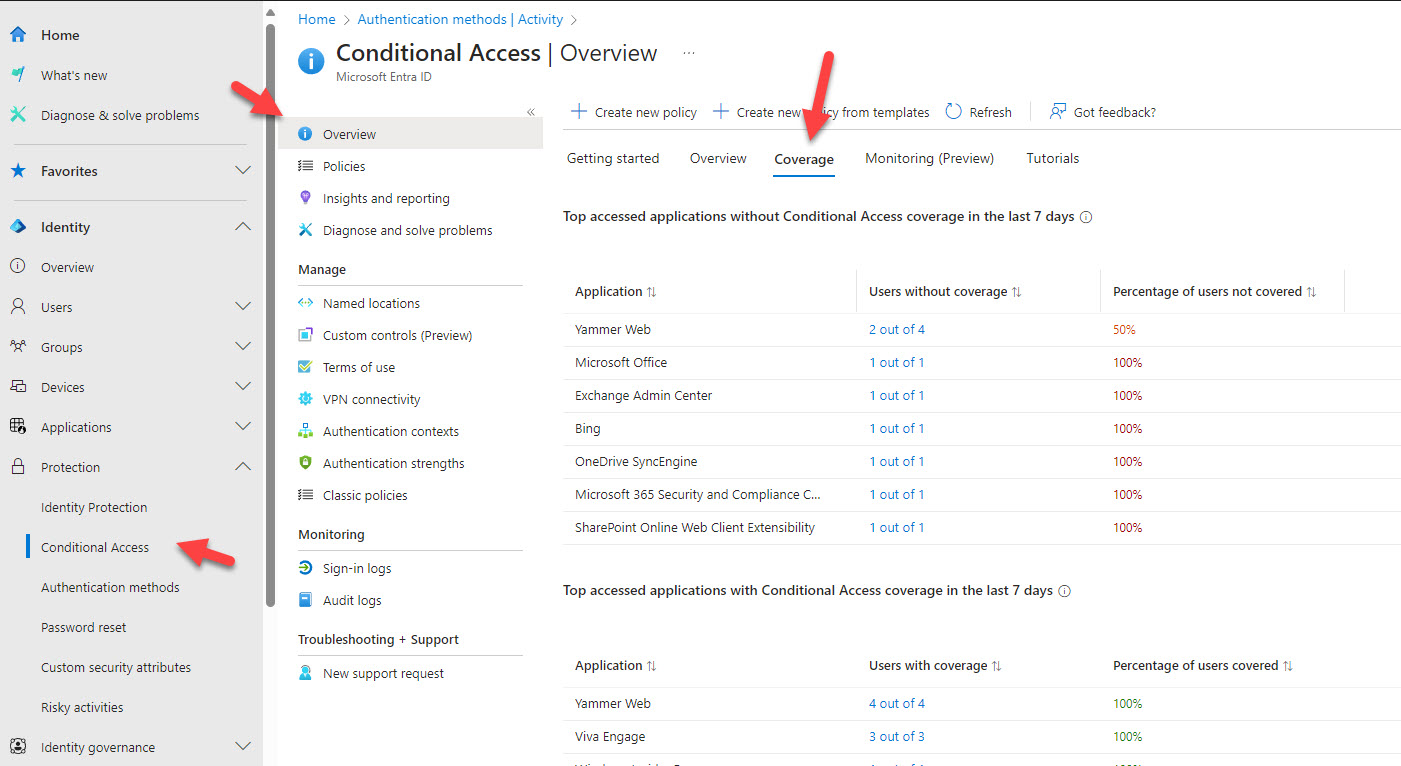
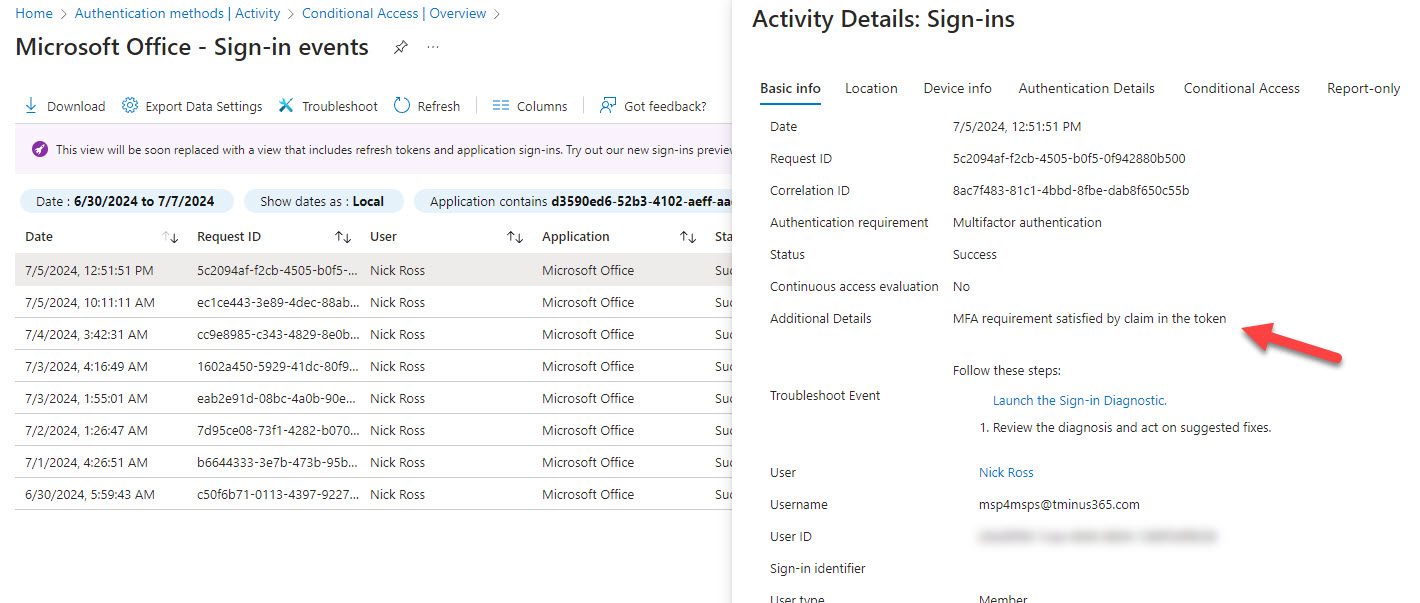
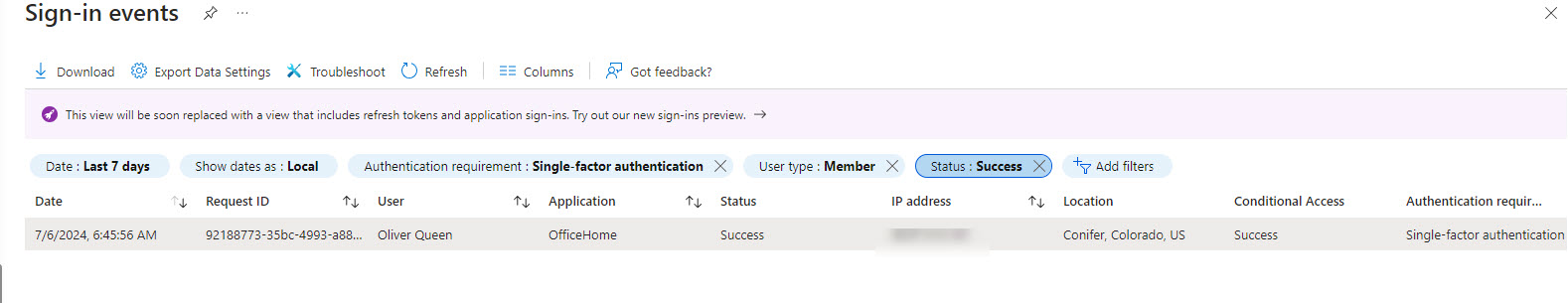
Tools that can help with reporting
- Stop using per-user MFA. Enforce a blanket conditional access policy for MFA.
- Disable legacy forms of MFA.
- User the User Registration Details and Activity report to review who is capable for MFA
- Periodically review your conditional access policy exclusions and the coverage report
The following are other tools I recommend that can help with the reporting and monitoring of MFA across your customers:
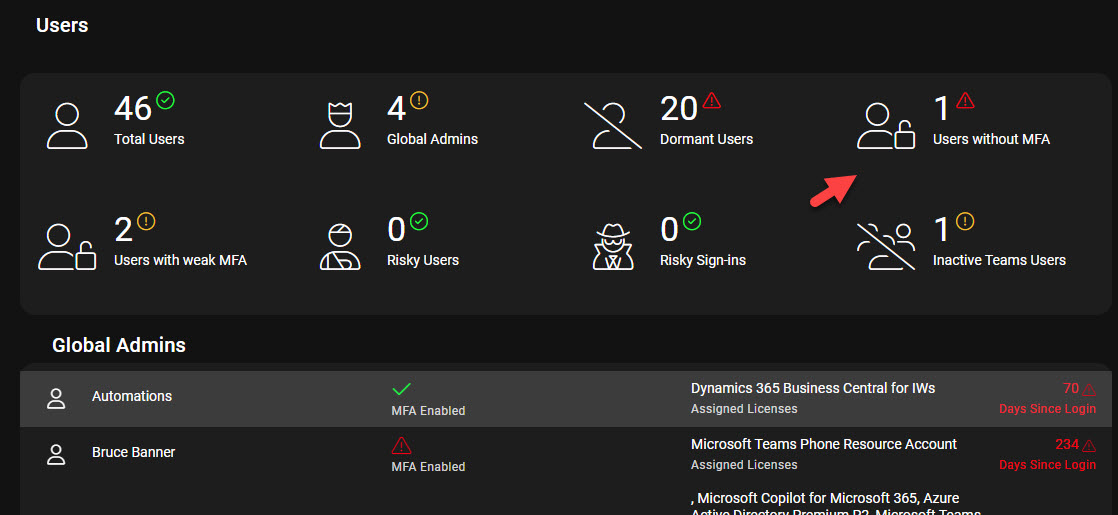

- Licensed users that:
- Are enabled
- Have a mailbox
- Are not a shared mailbox
- Are not covered by Conditional Access
- Are not covered by Security defaults
- Have not been registered for MFA
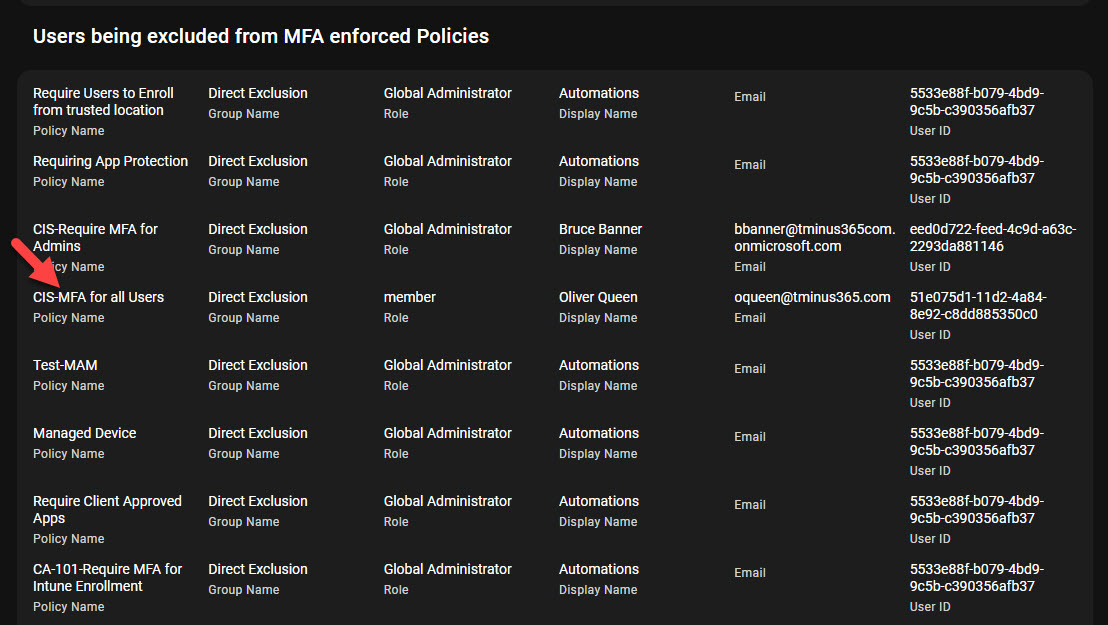
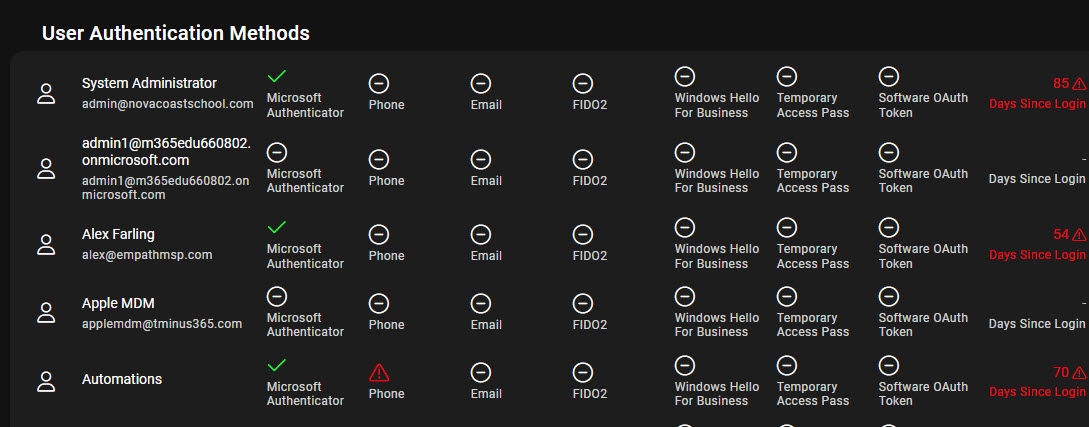
Run a free assessment on a tenant to see what this report looks like for you.

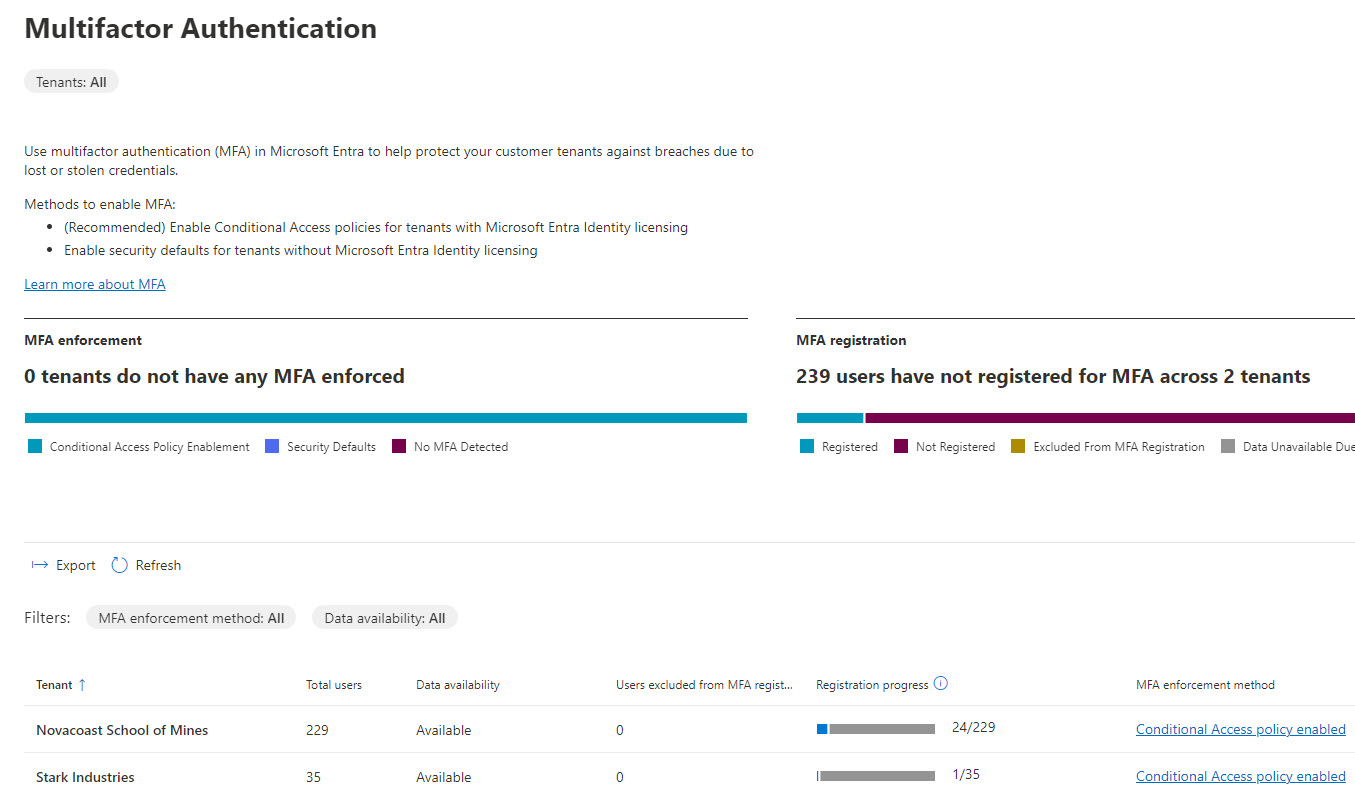
Bonus: APIs that help with reporting:
Getting Users Default MFA Method: https://learn.microsoft.com/en-us/graph/api/authentication-get?view=graph-rest-beta&tabs=http
Getting Users Per-User MFA State (new): https://learn.microsoft.com/en-us/graph/api/authentication-get?view=graph-rest-beta&tabs=http#example-2-get-a-users-mfa-state
Getting Users Additional MFA detail: https://learn.microsoft.com/en-us/graph/api/authentication-list-methods?view=graph-rest-beta&tabs=http
Getting User MFA Registration Information: https://learn.microsoft.com/en-us/graph/api/reportroot-list-credentialuserregistrationdetails?view=graph-rest-beta&tabs=http
