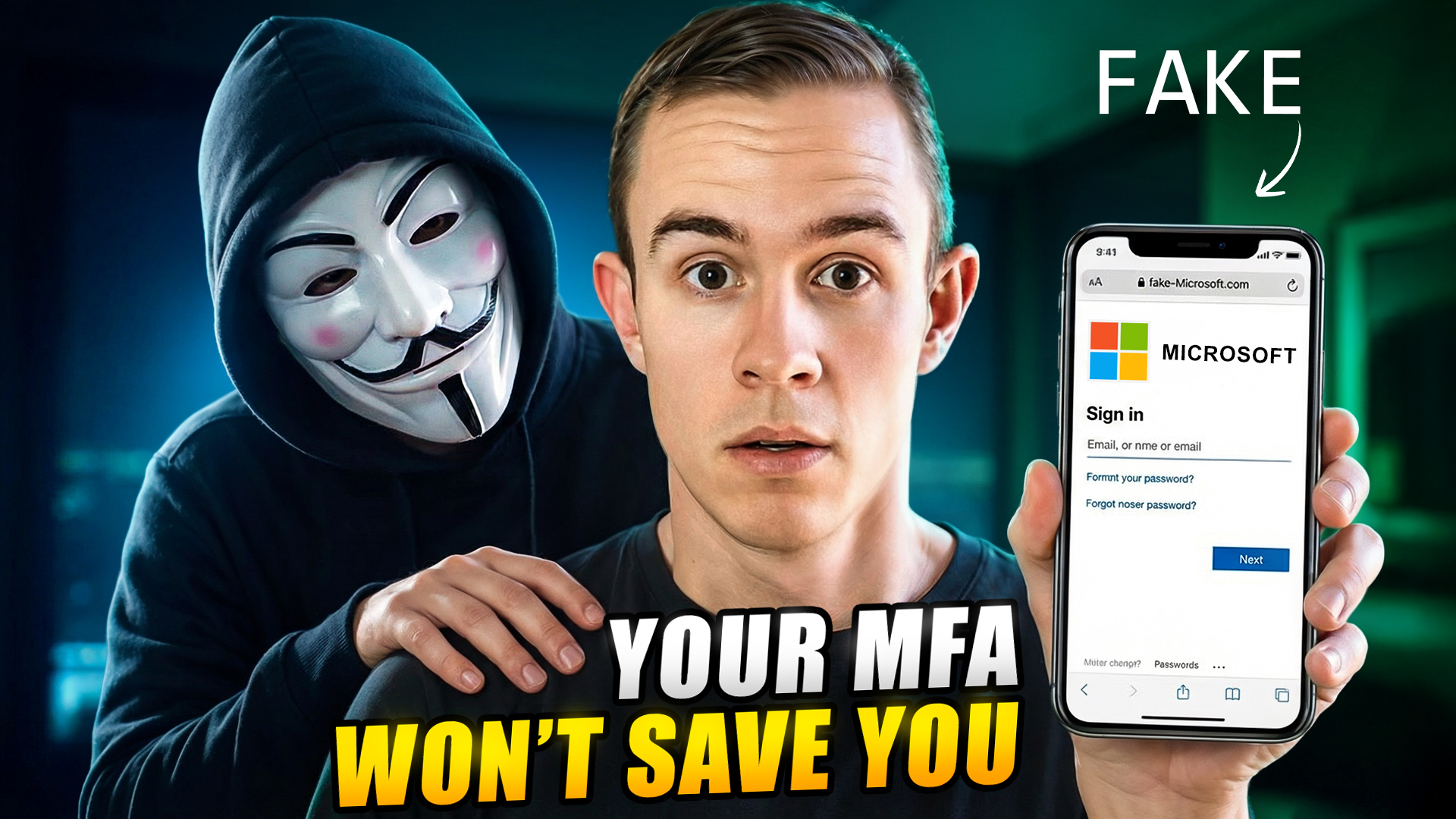
Why Your MFA Can Still Be Hacked (How I’d Implement MFA in 2026)
In today’s attack landscape, not all MFA methods should be treated equal. Across Microsoft 365 tenants, one of the fastest-growing attack techniques I’m seeing today is Adversary-in-the-Middle (AiTM) phishing —…
Secure Your GDAP Access with Just-in-Time Permissions
TL;DR: Most MSPs still run with standing access to customer tenants through GDAP. That’s convenient but dangerous. Switching to Privileged Identity Management (PIM) for Groups in Entra ID gives your…
What’s New in Microsoft 365 | November Updates | Ignite Highlights
Below are all of the latest feature updates coming to Microsoft 365 and highlights from Microsoft ignite. Automated Security Assessments mapped to the CIS Controls CloudCapsule is a tool I’ve…
Microsoft 365 Copilot for Business: What You Need to Know
Microsoft just dropped a brand-new Copilot SKU specifically for small and medium businesses. Lower cost, same Copilot capabilities. Let me break down what’s new, what it includes, how to activate…
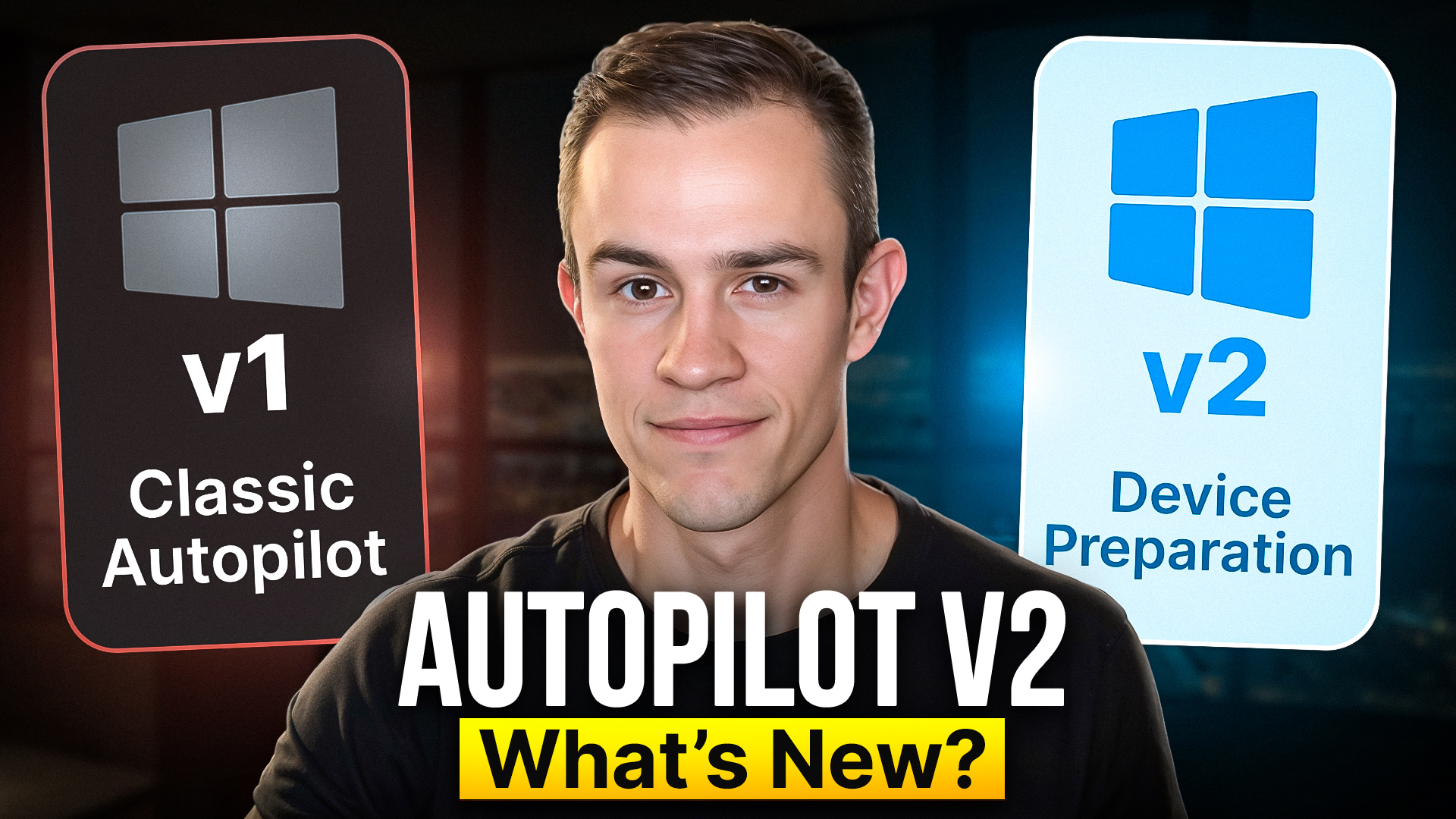
Autopilot Device Preparation Tutorial | Is it better than v1?
Windows Autopilot has been around for years, and many admins have built entire deployment processes around what we now call “Autopilot V1.” But recently, there’s been a ton of buzz…
This Copilot Trick Turns Outlook Into Your Executive Assistant
You know that feeling when you open your inbox in the morning and it’s just… chaos?Meeting invites. Follow-ups. “Quick questions.” And before you even start working, half your day’s already…
What’s New in Microsoft 365 | October Updates
Below are all of the latest feature updates coming to Microsoft 365 Automated Security Assessments mapped to the CIS Controls CloudCapsule is a tool I’ve been working on over the…
How I Secure Admins in Microsoft 365
Privileged accounts are the #1 target for attackers. One compromised Global Administrator can mean full control of mail, SharePoint, Teams, Defender…everything. The fallout is real: downtime, legal exposure, regulatory headaches,…
Secure Local Admin Passwords: How Microsoft’s LAPS for Intune Solves It
IT admins still fall into two common traps when managing local administrator accounts across user workstations: Using the same password across all endpoints. Allowing end users to be local administrators…
Ditch the VPN: How Microsoft’s Global Secure Access is Changing Remote Connectivity
2025 has been a rough year for VPNs. We’ve seen breaches at major vendors, clunky user experiences, and a constant flood of helpdesk tickets from frustrated users. Yet, many businesses…