Over the years, Microsoft has evolved the enforcement of multi-factor authentication into various sections of the application. These changes are making it confusing as an admin to know where to go to see a report of MFA adoption. In this article, we will cover the various methods of MFA enrollment and provide a script that you can use to report on MFA in all customer environments.
Registering for MFA
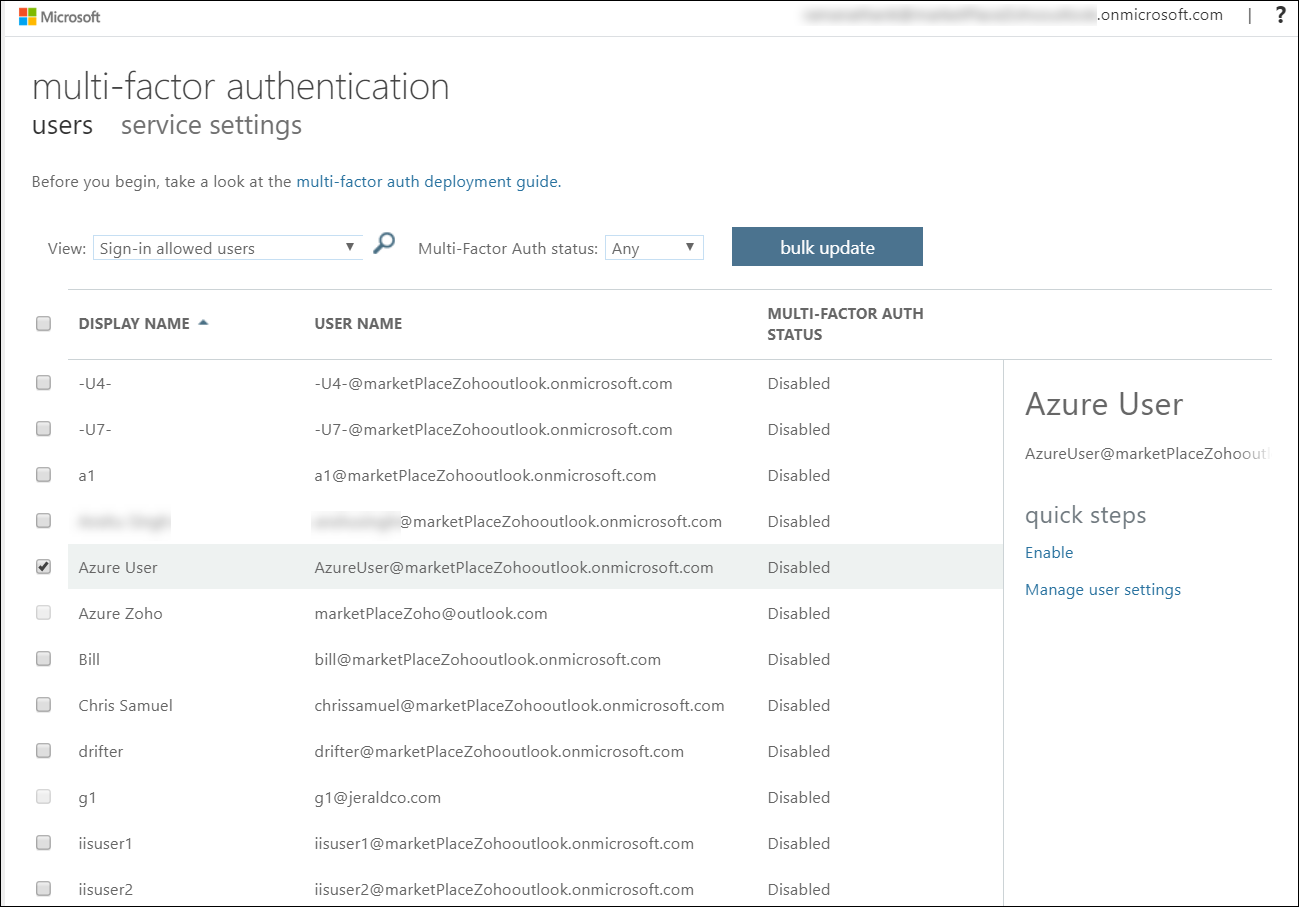
Per User MFA (Legacy Method)
Most MSPs are still probably using the MFA portal as a primary method of enforcing MFA. In this portal, there are options to set users as Disabled, Enabled, or Enforced. Enabled means that the user has a 14-day grace period to enroll a second factor. Enforced means that they are required to set this up immediately upon next sign in. The legacy method is in parenthesis here because Microsoft has mentioned they intend to deprecate this portal over time. No official date has been posted yet. This method is effective and can also be enforced via PowerShell.
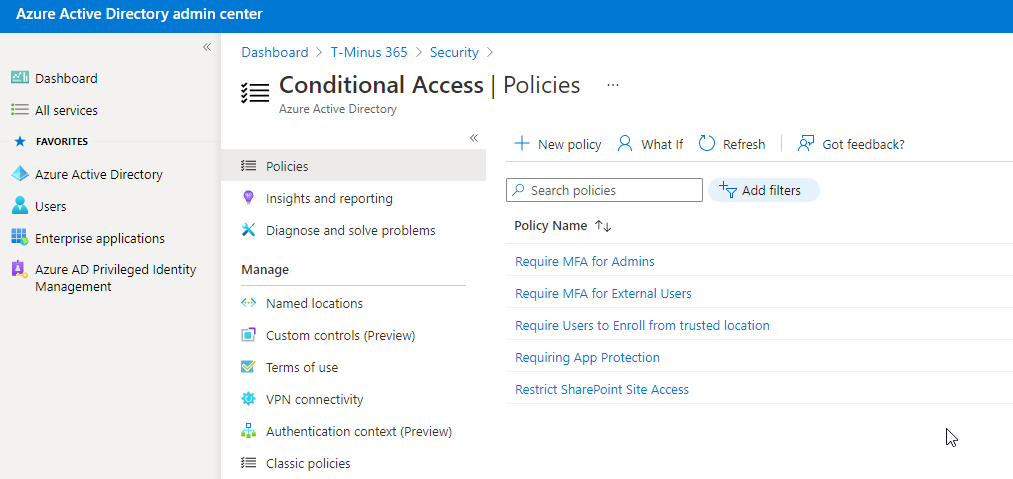
Conditional Access Policies
Conditional Access Policies are primarily if/then statements that grant or block access to corporate resources. If certain conditions are met, then controls are put into place. CA policies enforce MFA and scope them to certain users or groups. When a policy is established, the user will be asked to register a second factor the next time those conditions are met. CA policies require an Azure AD (Active Directory) P1 license which is usually the biggest limitation for most clients that utilize Business Standard licensing.
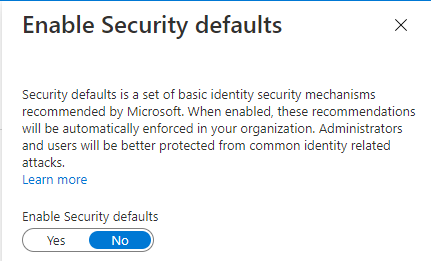
Security Defaults
Security Defaults were introduced at the end of 2019 and are on by default in all net new tenants. They automatically enforce MFA for all users with a 14-day grace period and require you to use the Microsoft Authenticator app. Security defaults cannot be on in addition to having a CA policy. If at least on CA policy is enabled, then Security defaults will have to be turned off.
The Script
To summarize, the methods in which you can enforce MFA make reporting a bit of a nightmare. For this reason, I created a script that pulls a report on every customer managed in partner center. The script uses the Secure Application Model to connect to your client environments and creates HTML pages that list the following:
- MFA enforced through the MFA portal
- Conditional Access Policies
- Security Defaults (enabled or disabled)
- Custom Controls (ex. DUO)
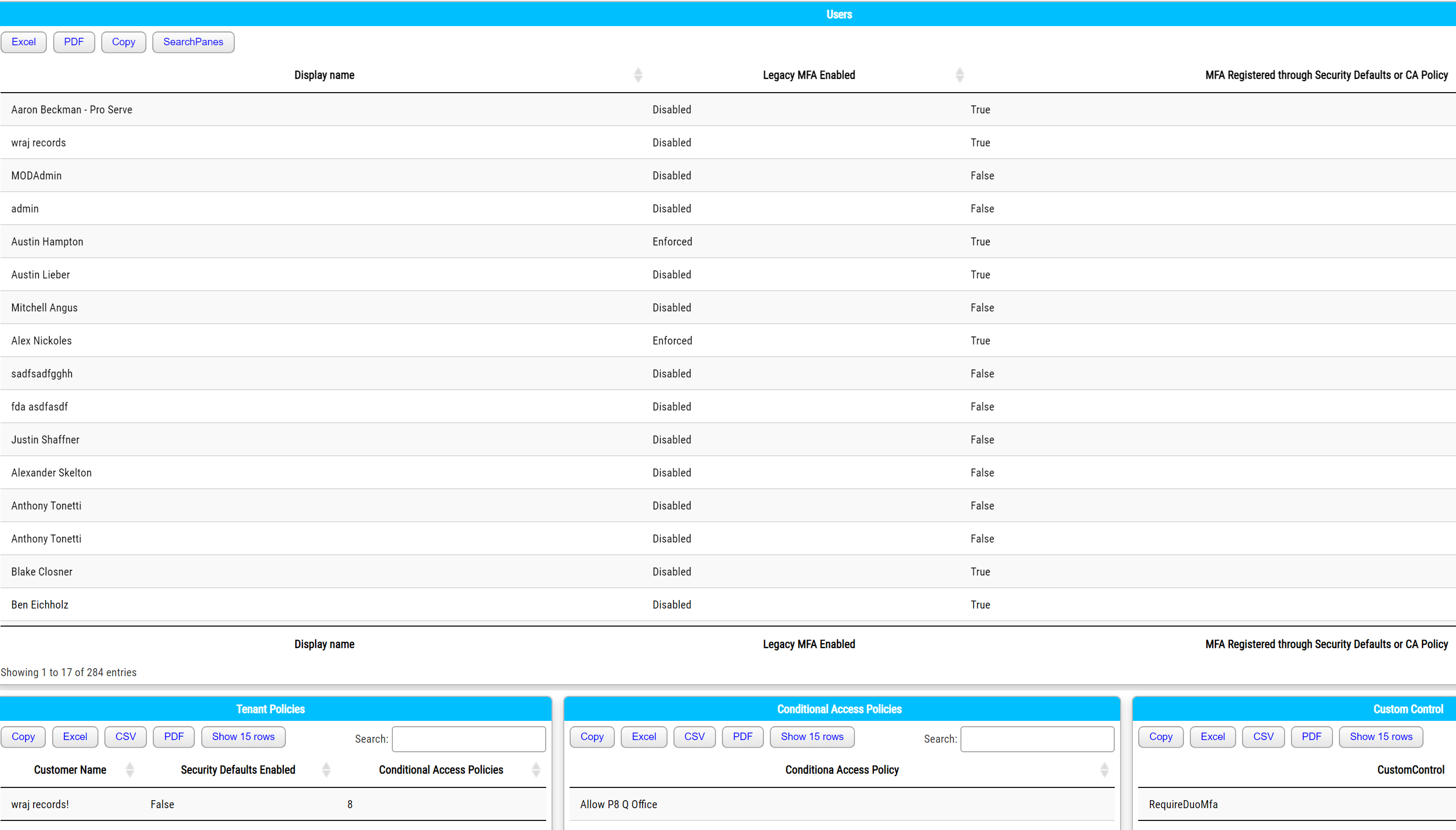
I did not cover custom controls, but they are part of CA policies and allow a 3rd party like DUO to enforce MFA. Many MSPs have this for their customers, so I wanted to add it here. This script should be run periodically to assess true MFA adoption.
I hope this provided some clarity on MFA enrollment with Microsoft! Please leave any questions or comments below.

Hey,
Any idea on how to make this show only licensed users as opposed to unlicensed?