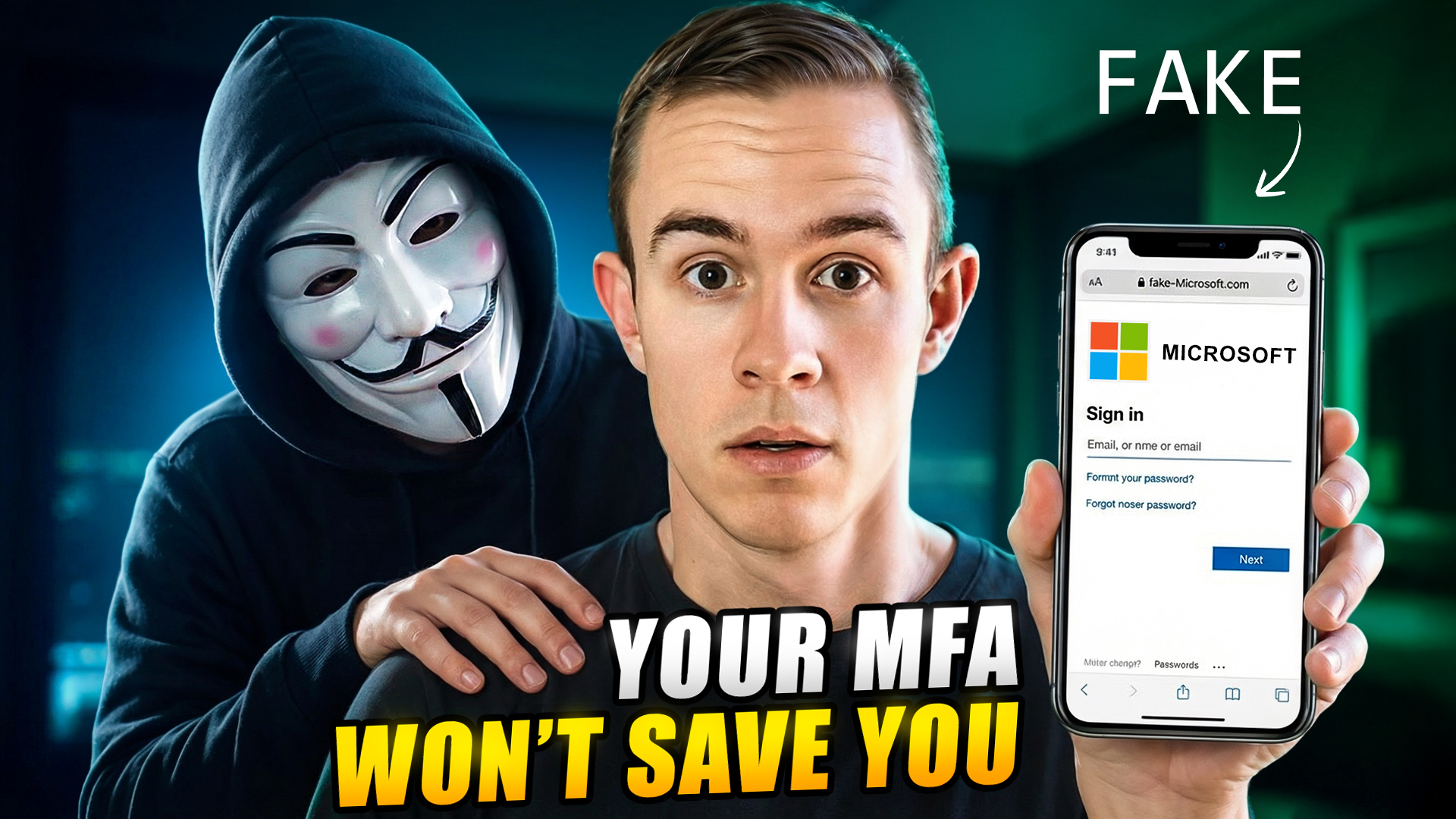
Why Your MFA Can Still Be Hacked (How I’d Implement MFA in 2026)
In today’s attack landscape, not all MFA methods should be treated equal. Across Microsoft 365 tenants, one of the fastest-growing attack techniques I’m seeing today is Adversary-in-the-Middle (AiTM) phishing —…