Have you ever opened a seemingly harmless Word document, only to have it trigger a script that could have encrypted your entire device? What saved you from disaster? It could very well have been an invisible defense mechanism you didn’t even know existed—Attack Surface Reduction (ASR) rules in Microsoft 365.
In this blog post, we’ll dive deep into how ASR rules work, how they can prevent ransomware and other malicious attacks, and why rolling them out the wrong way could be more disruptive than helpful for your business.
What Are ASR Rules?
Think of ASR rules as invisible tripwires designed to block malicious actions before you even notice they’re happening. Whether it’s an Office macro running or an attacker trying to download a malicious payload, ASR rules step in and stop the process before it can wreak havoc.
ASR rules are part of the Microsoft Defender suite, which is aimed at securing devices from attacks like ransomware, phishing, and other malicious scripts. They operate primarily at the application layer, focusing on blocking unauthorized macros, scripts, and processes, even those that may not be flagged by traditional antivirus solutions.
Configuring ASR Rules in Microsoft 365
Let’s walk through the basics of how to configure these powerful rules using Microsoft Intune.
Step 1: Ensure Devices Are Enrolled in Microsoft Defender
Before you can implement ASR rules, devices must be enrolled in Microsoft Defender. If your devices aren’t yet enrolled, you won’t be able to enforce ASR rules. You can find step-by-step instructions in the Microsoft documentation or previous videos I’ve done on this topic.
Step 2: Access the Endpoint Security Settings
In the Intune admin center, navigate to Endpoint Security, and look for the Attack Surface Reduction section. Here, you can create a policy that will apply ASR rules across your organization.
Step 3: Create and Configure the Policy
Once inside the Attack Surface Reduction section, click on Create Policy. You’ll choose your platform (e.g., Windows) and select the specific ASR rules profile to enforce. From there, you’ll have several options, including “Off,” “Audit,” and “Block” for each rule.
"Audit" Mode: Why You Should Start Here
While it might seem tempting to immediately switch everything to “Block,” this could cause significant disruptions. By choosing the “Block” option, you may inadvertently prevent legitimate applications and processes from running, causing unnecessary support issues.
Microsoft recommends starting with the “Audit” setting for all ASR rules. This setting doesn’t block anything immediately but logs activities that would have been blocked. It gives you the opportunity to review any false positives or legitimate business processes that might be flagged.
As a best practice, begin by auditing these rules across your organization, then gradually move to the “Block” setting once you’ve identified and resolved any issues.
Monitoring and Adjusting ASR Policies
Once your ASR rules are in place and running in audit mode, it’s time to monitor their performance. In the Defender Admin Center, you can track the effectiveness of these rules by viewing detailed reports on detected activities.
For example, if a document’s macro is flagged as malicious, you’ll see it listed in the Attack Surface Reduction report. These reports provide the telemetry you need to adjust your rules and refine exclusions over time.
Key Takeaway: By monitoring the results, you can ensure that your policies are protecting your organization while minimizing disruptions.
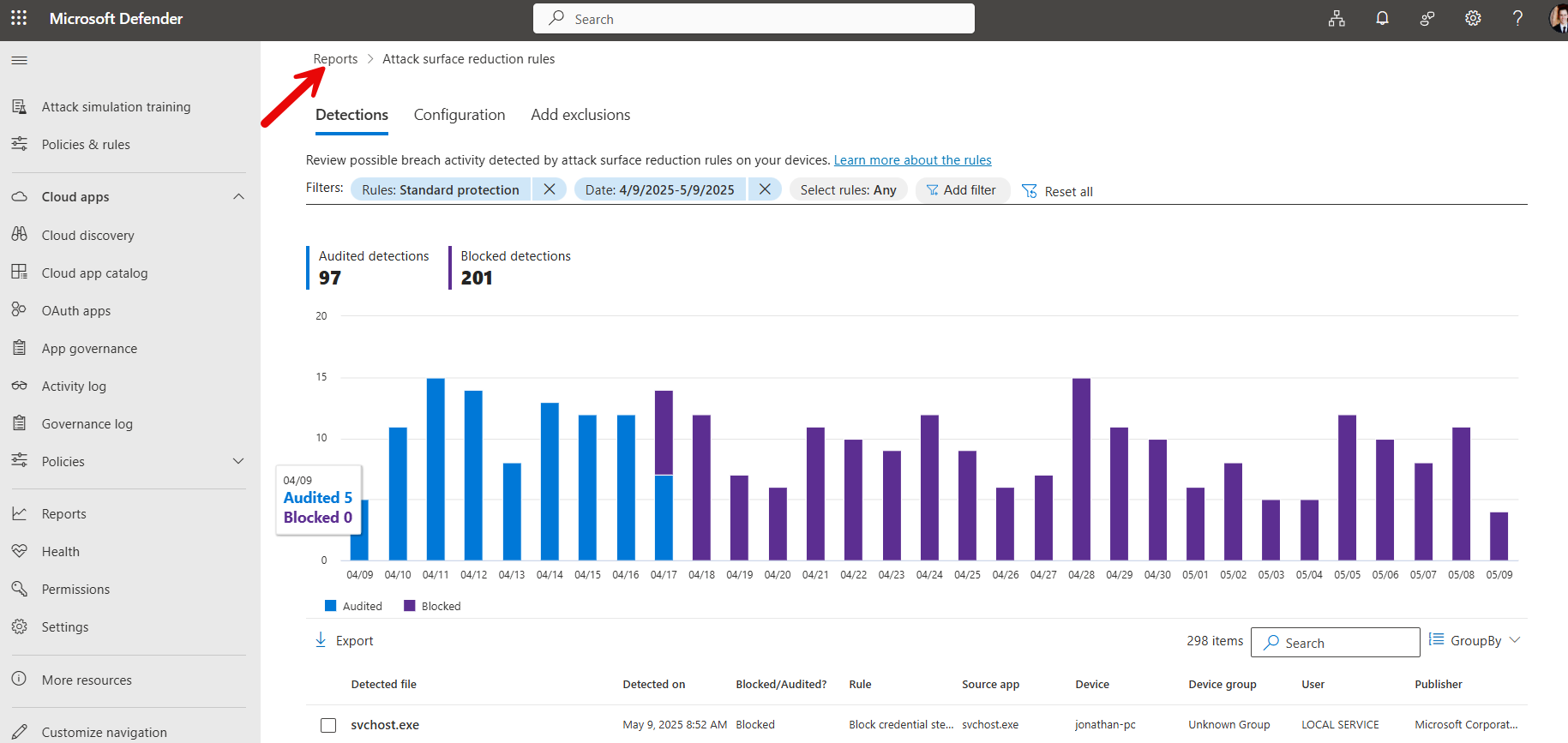
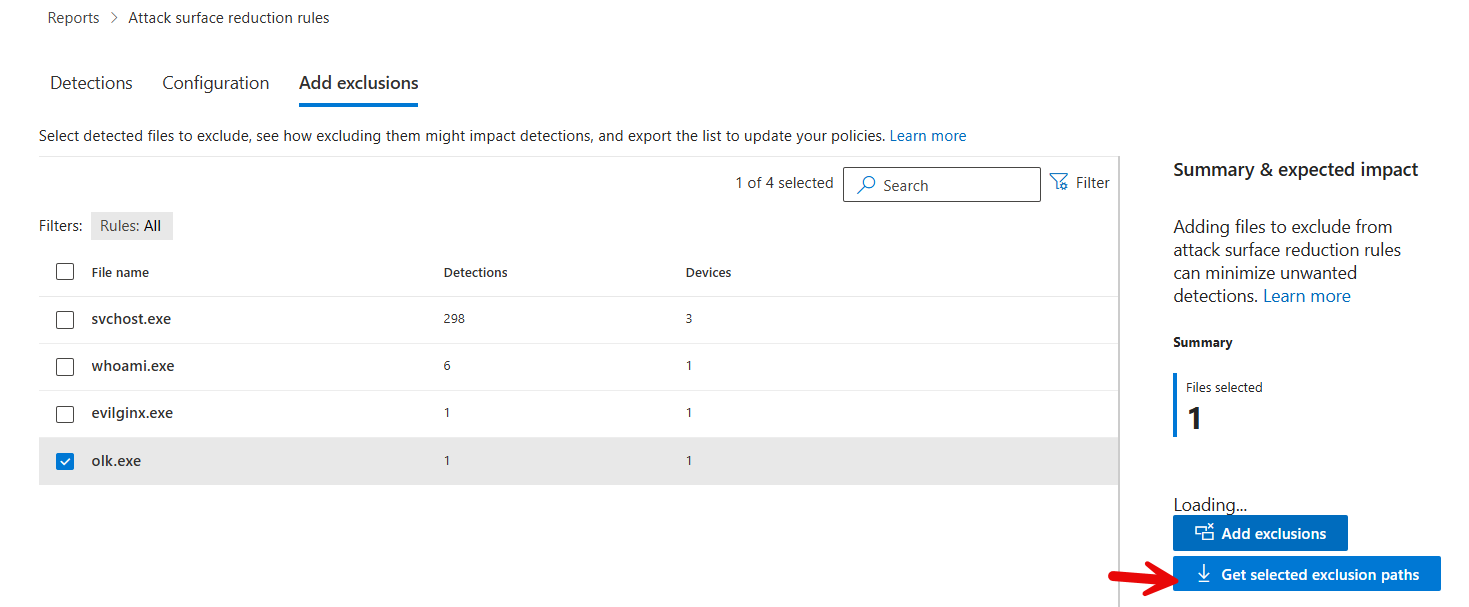
In the “Add Exclusions” tab you can actually get the exclusion paths you can add to the ASR Rule
VS
The Risk of Misconfiguration: Don’t Let ASR Rules Cripple Your Business
While ASR rules are an incredibly effective defense mechanism, rolling them out incorrectly can lead to significant disruptions. For example, a financial department’s use of macros to process payroll could be flagged as a threat, potentially halting business operations.
How to Mitigate the Risk of False Positives
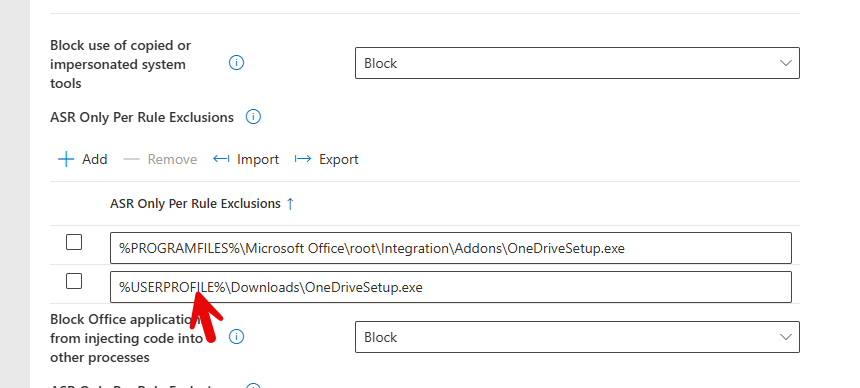
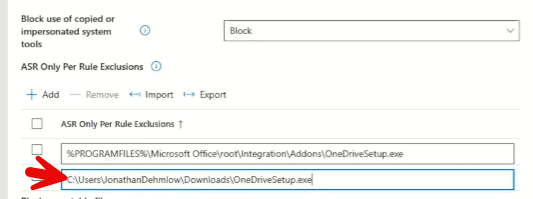
One of the major challenges with ASR rules is dealing with false positives. These are legitimate applications or processes that are mistakenly flagged as malicious. The solution? Use the exclusion feature within Microsoft Defender to whitelist specific processes, files, or directories that you trust.
For instance, if OneDrive’s setup file gets flagged during deployment, you can exclude it from detection while maintaining the broader security policy. This way, you can prevent interruptions to legitimate workflows while still securing your endpoints from malicious activities.
Conclusion: Start Small, Scale Smart
When it comes to implementing ASR rules, the key is to start small. Begin with auditing, review the results, and gradually adjust until you’re confident in your configuration. By taking this phased approach, you can effectively defend against threats without crippling your organization’s business applications.
For managed service providers (MSPs) and IT teams, it’s crucial to implement these rules in your security baselines as soon as possible. Doing so will help you prevent attacks that traditional antivirus solutions may miss, and protect your organization from the growing threat of ransomware and other cyberattacks.
If you’re ready to take the next step in securing your organization’s endpoints, start with ASR rules and make them part of your security strategy today.
Helpful Resources:
- Microsoft Defender for Endpoint attack surface reduction rules deployment overview – Microsoft Defender for Endpoint | Microsoft Learn
- Attack surface reduction rules reference – Microsoft Defender for Endpoint | Microsoft Learn
- Settings list for the Microsoft Intune security baseline for Microsoft Defender for Endpoint – Microsoft Intune | Microsoft Learn
