Imagine you had a window in your house with a broken lock. Anyone could open it and climb right in. Now imagine your neighbor posts about it on Next Door for everyone to see. Would you quickly try to fix the lock? Most likely!
This is the same mindset we need when managing software vulnerabilities across workstations. Unpatched or unknown applications can act as entry points for attackers—and most environments have hundreds of them. In today’s article, I am going to break down how you can get 24/7 active vulnerabilities scanning across all of your workstations under management using Microsoft Defender. Additionally, I’ll show you some of my top tips for prioritizing remediation.
Why it matters:
Vulnerabilities can and will arise on existing software. Not having an approved inventory can lead to exploits of users, devices, and apps which can ultimately create loss for the business.
Hackers exploit outdated software to gain access, steal data, or install ransomware.
Even strong security tools can’t protect you if an attacker walks through an unpatched application.
Cyber insurers and compliance frameworks often require software to be kept up to date.
If your team is unknowingly using vulnerable apps, your business is carrying risk without realizing it.
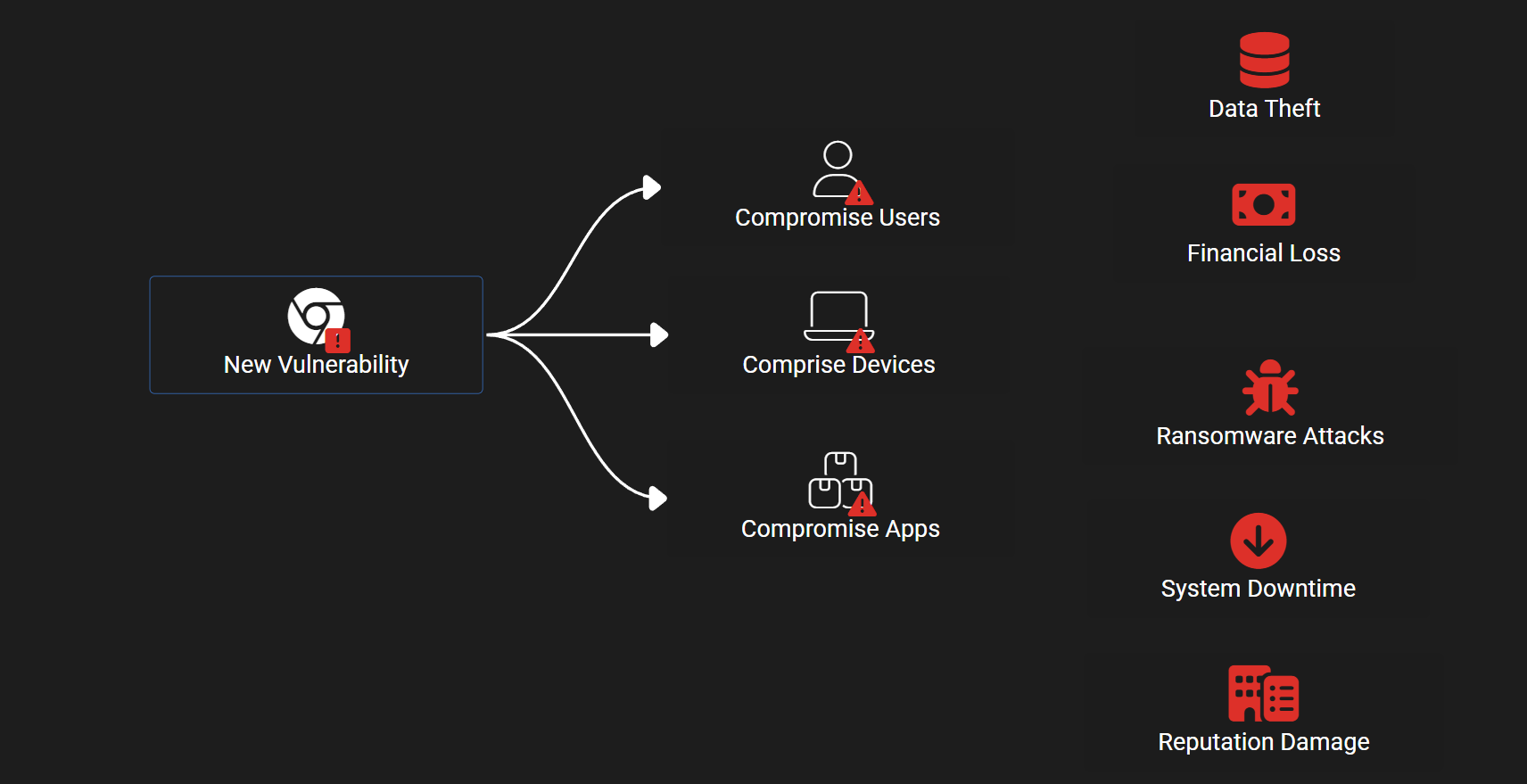
Maintaining visibility and control over installed software is hard—especially at scale. But failing to do so creates real risk: data breaches, ransomware, financial loss, and downtime. Some applications might not have known vulnerabilities but can still be used maliciously (e.g., Quick Assist in social engineering attacks).
This is where an approved software inventory and continuous vulnerability scanning come in. Together, they form a baseline for reducing risk and improving operational control.
Microsoft Defender for Business: Built-In Protection
If you’re using Microsoft 365 Business Premium or Defender for Endpoint Plan 2, you already have access to native vulnerability management tools. Here’s what that includes:
24/7 software vulnerability scanning
An exposure score dashboard
Detailed insights into app versions, patch age, and severity
Built-in remediation recommendations
Make Sure Devices are Enrolled
🛠️ Step 1: Turn It On
Head to the Microsoft 365 Defender portal.
Go to Settings → Endpoints → Onboarding.
Choose your onboarding method:
Intune (preferred for MDM environments)
Group Policy
Local script for testing
Make sure Intune integration is enabled under Advanced Features.
📬 Step 2: Get Alerted
Configure email notifications for vulnerabilities. Be aware—Windows OS updates might cause noise if they haven’t hit their patch window yet. Use PSA tools or helpdesk rules to triage these efficiently.
After enrollment is pushed out/activated, it can take around 24 hours for devices to start showing up in the defender admin center.
Navigating the Vulnerability Management Dashboard
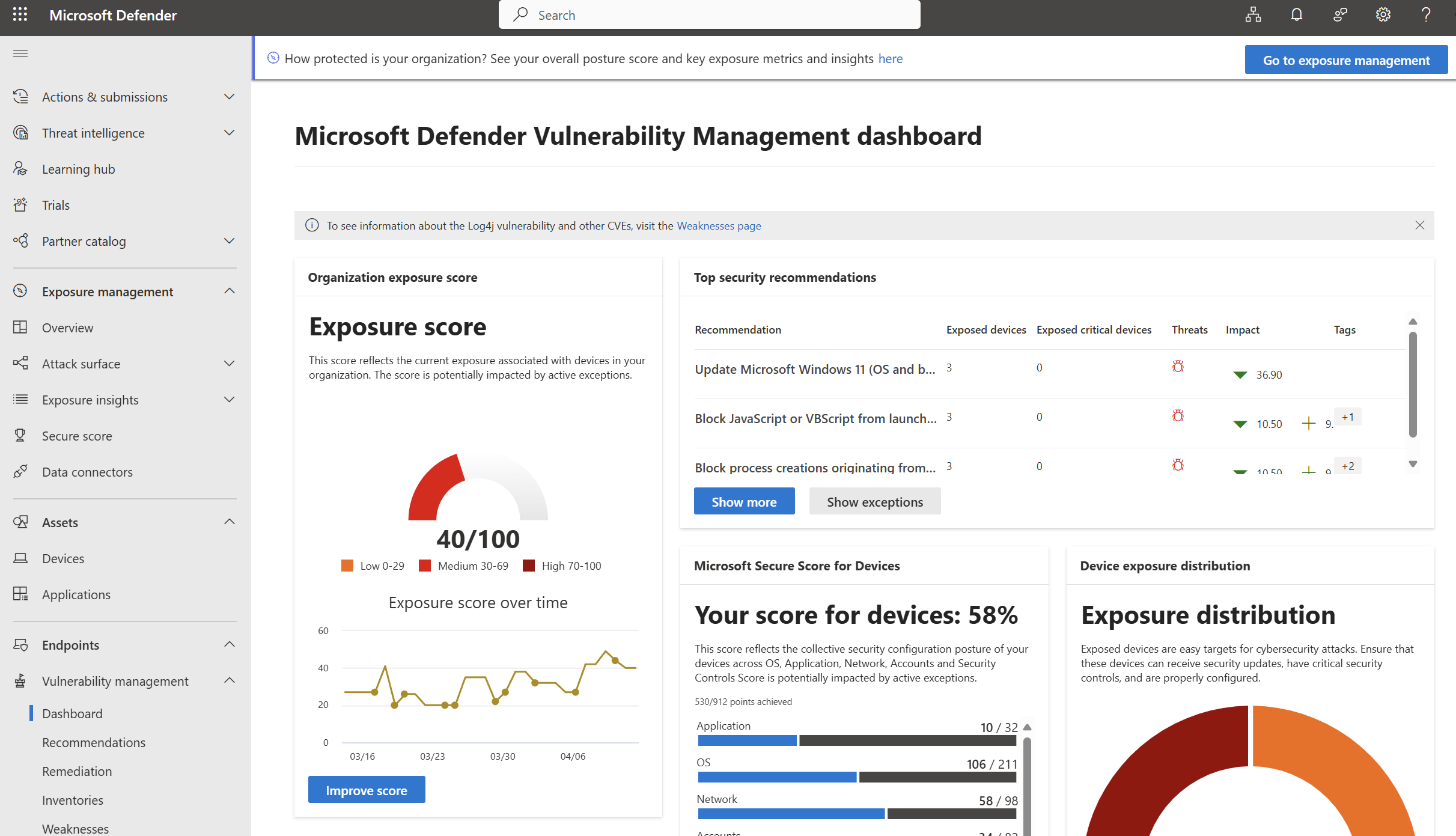
Once Defender starts reporting data, you’ll see the Exposure Score—the higher the number, the more vulnerabilities and security misconfigurations you have across devices.
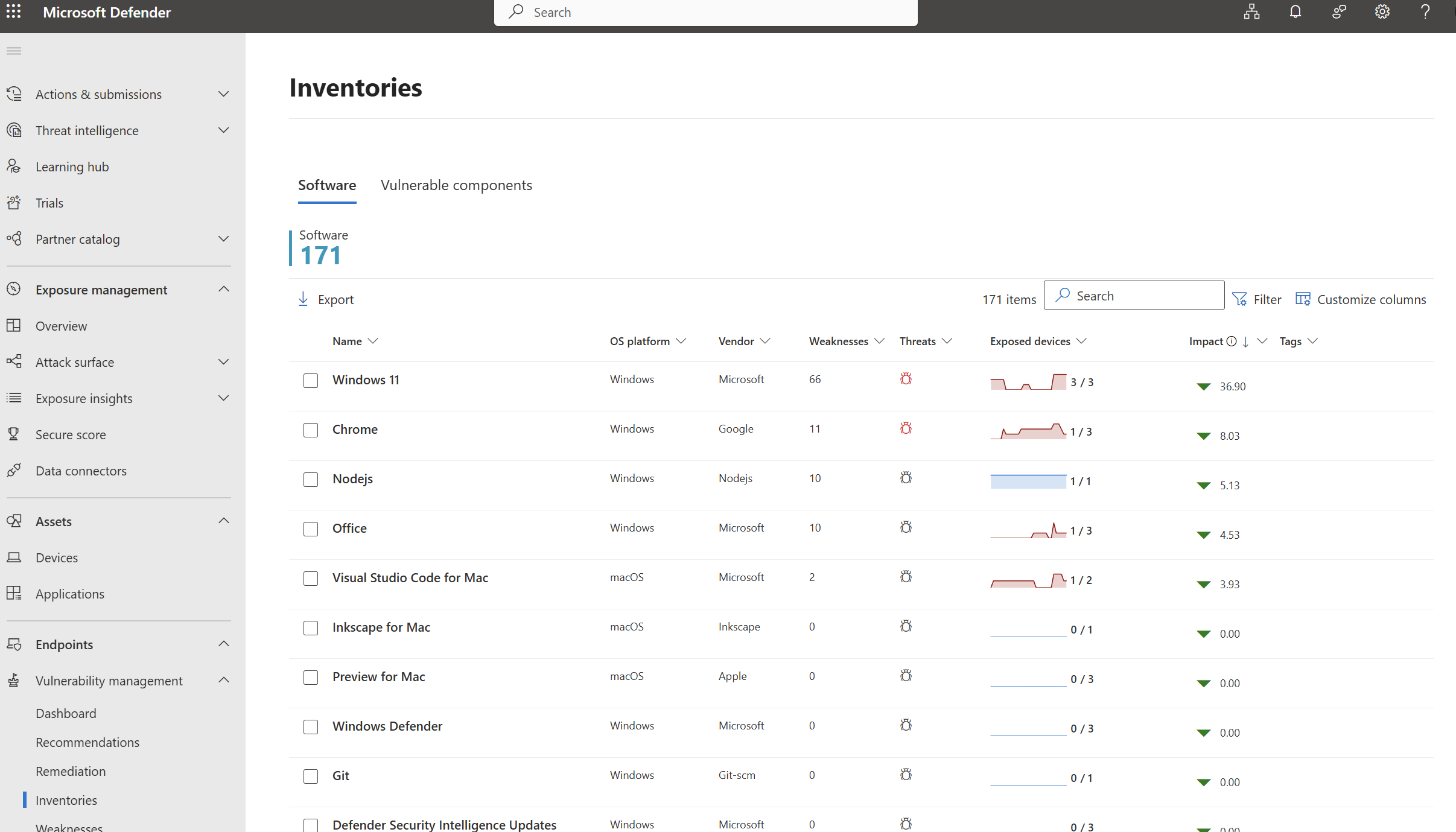
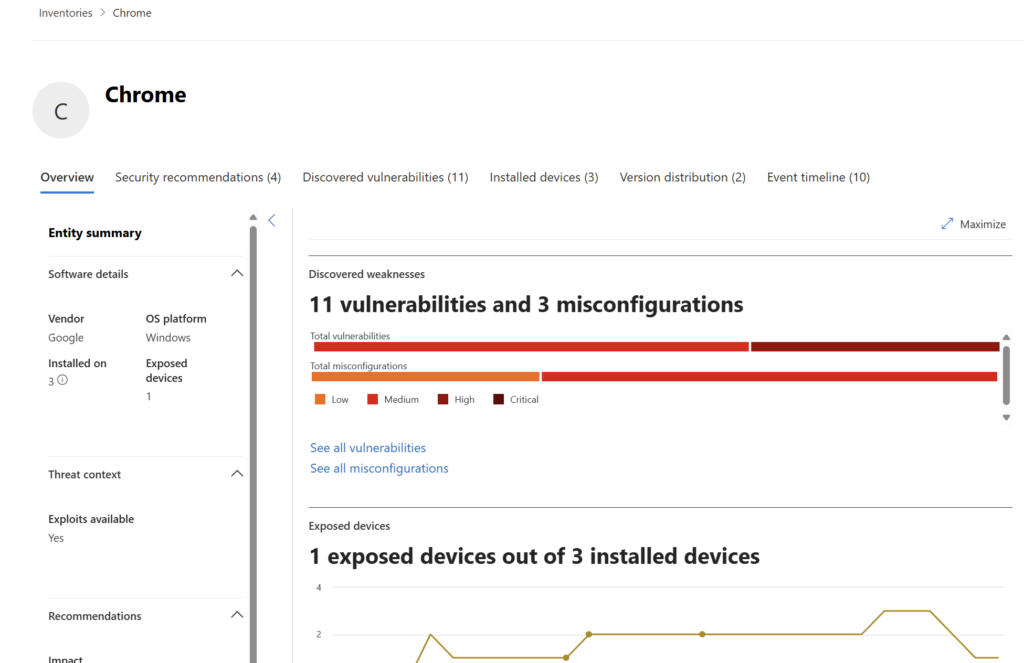
Drill into Inventories on the left to see the list of software. Clicking on a piece of software will allow you to dirll into a software page. Poke around here to get famliar with:
Known vulnerabilities and CVEs
Severity and exploitability
Version distribution across devices
Remediation recommendations
This view helps you prioritize remediation efforts and even surfaces known exploited vulnerabilities automatically.
Building Your SOP: Approve, Remove, Patch
This is where the rubber meets the road. You’re now staring at a list of 300+ apps. What do you do?
I recommend this decision matrix:
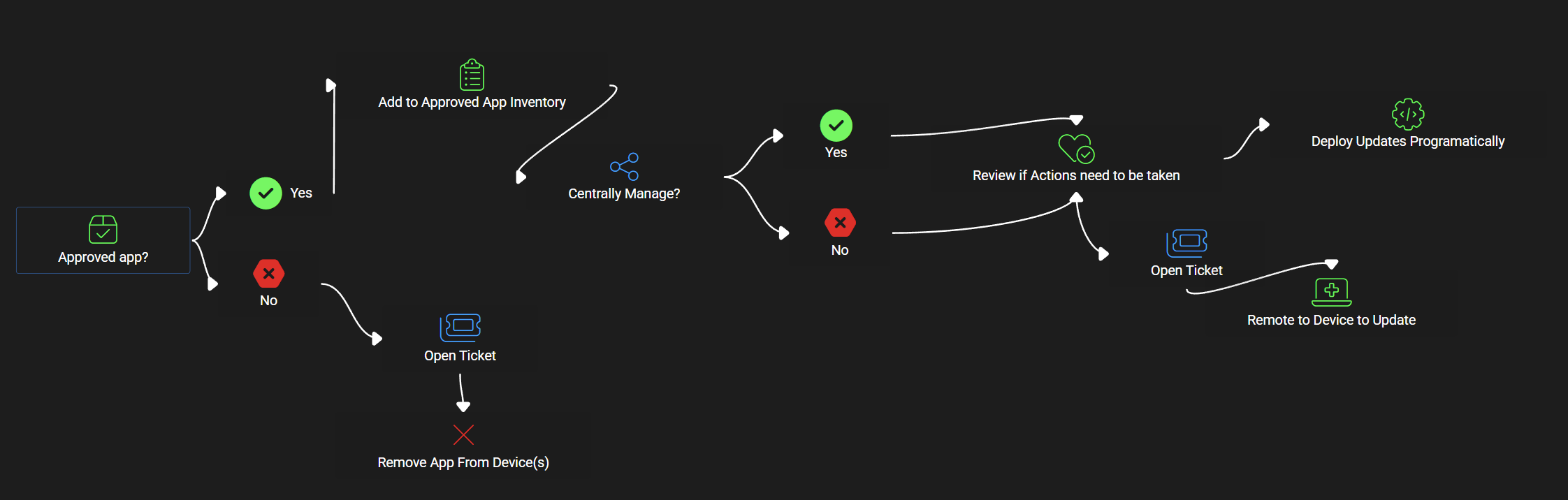
Review all applications in the vulnerability management dashboard that have a public exploit or weakness. Its possible there will be weaknesses and public exploits that have not had enough time to update on their own. (i.e. patch Tuesday for OS updates and/or CVEs that were just released).
Is it approved?
✅ Yes → Add to your documented inventory
❌ No → Open a ticket to investigate/remove it.
Is it centrally managed?
If yes, deploy updates via RMM/Intune.
If no, consider manual removal or user guidance.
Does it need action now?
Look at the age of the vulnerability and version distribution.
Focus on older versions and high-priority threats first.
Prioritizing What Matters
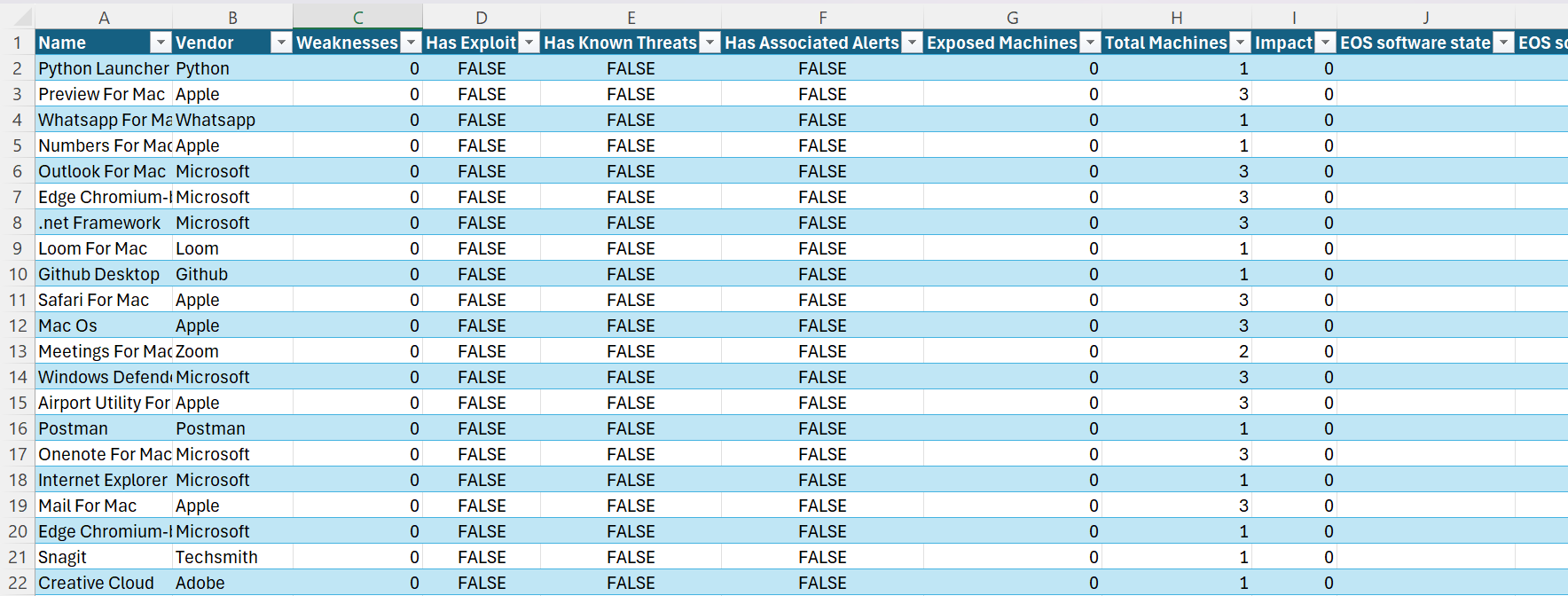
You can export your software inventory from the Inventories tab in Defender, here are a few ways to filter and act quickly:
Obviously start with any software with public exploits or weaknesses as priority
Sort by number of devices installed — higher count usually means higher priority.
Filter out Microsoft and Apple — hone in on third-party software vs a bunch of noise natively installed on the device
Search for red flags — remote tools, file-sharing apps, password managers, unknown vendors.
Example: If Dropbox is installed on 100+ devices but you’ve standardized on OneDrive, it’s time to start that shadow IT cleanup.
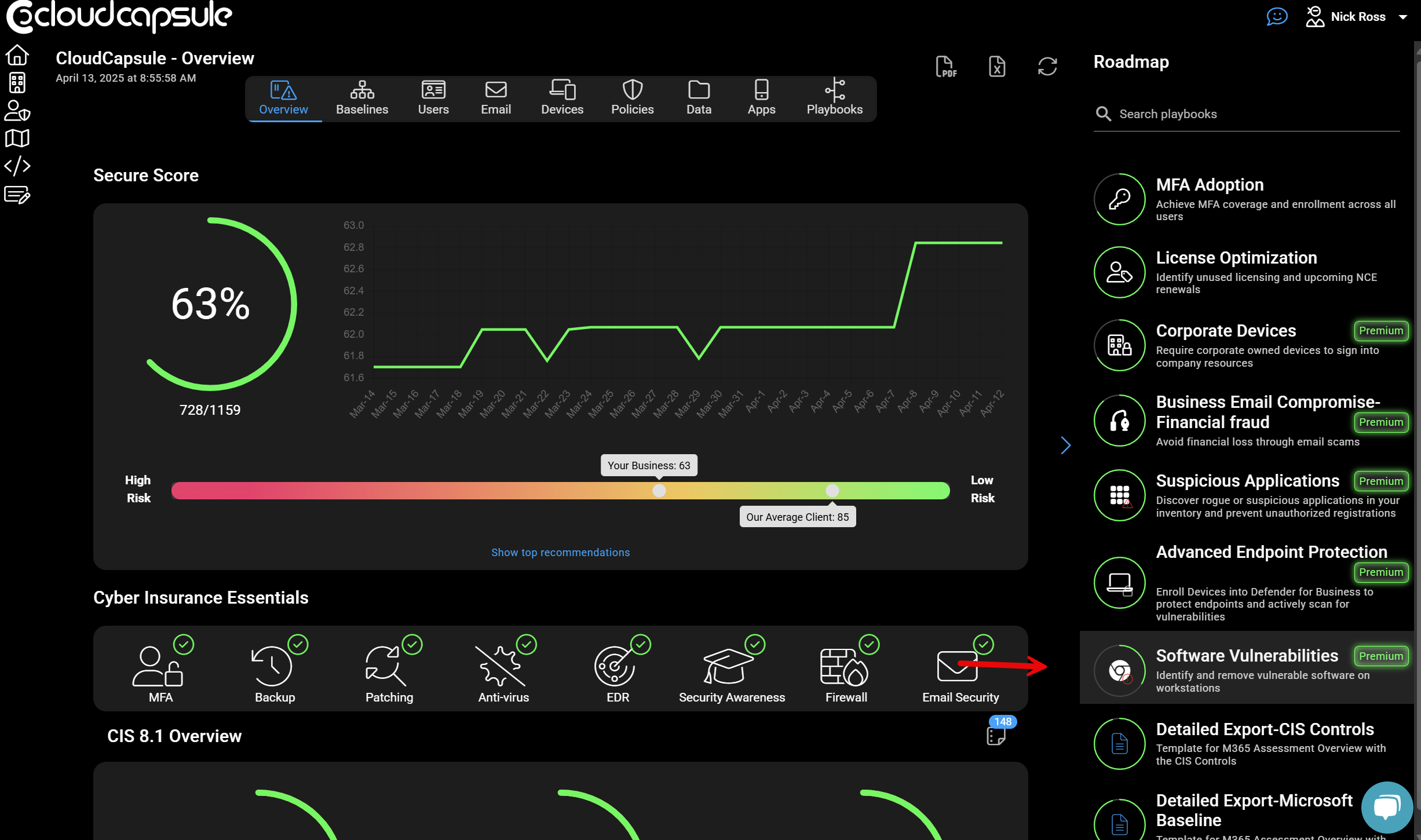
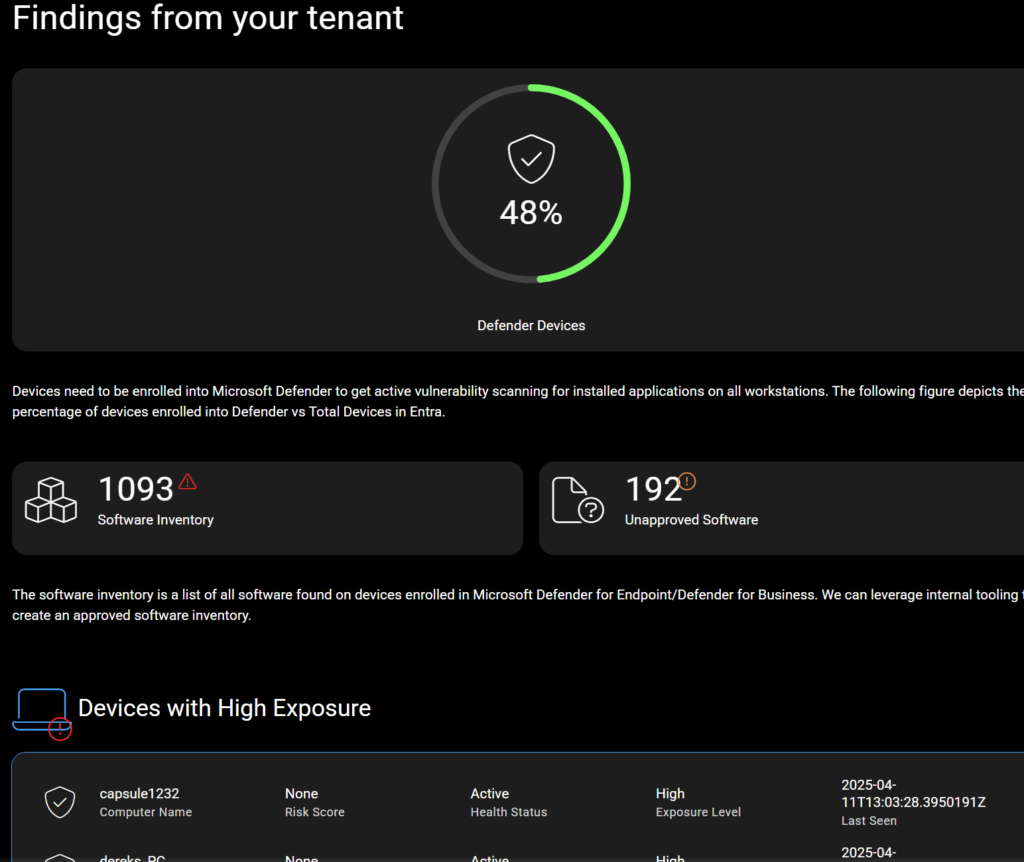
Pro Tip: Use CloudCapsule to Streamline It All
I’ve built CloudCapsule to help MSPs and IT teams manage this workflow efficiently:
Visualize all of your applications across customers
Approve or unapprove apps in bulk
Have pre-defined proposals to clean up software inventory
Export reports for QBRs or security reviews
Final Thoughts: This Is a Journey, Not a Sprint
You won’t clean up your inventory in a day. But with the right tools and a clear SOP, you can chip away at it over time—and turn a sprawling, risky app landscape into a well-governed, secure environment.
Start with:
Layered protections (i.e. no local admin rights, App Control policies, etc.)
24/7 vulnerability scanning via Defender
A living, breathing approved software inventory
…And you’ll be far ahead of the curve.
