In today’s digital age, cyberattacks are constantly evolving, and one of the fastest-growing threats in the Microsoft 365 ecosystem is token theft, also known as token replay attacks. This attack method has surged over 111% year-over-year, and today I’m going to walk you through what token theft is, how it works, why it’s a threat to your business, and, most importantly, the top four security policies you should implement in Microsoft 365 to protect and mitigate these attacks.
What is token theft?
Token theft is an insidious type of attack where a cybercriminal hijacks a user’s authentication token to gain unauthorized access to their account. The scary part? Multi-factor authentication (MFA) won’t necessarily protect you from this. Even if users have MFA enabled, once an attacker has stolen the authentication token, they can bypass MFA entirely and act as if they are the legitimate user.
In this post, we’ll break down how token theft works and what steps you can take to reduce your risk.
How Token Theft Works
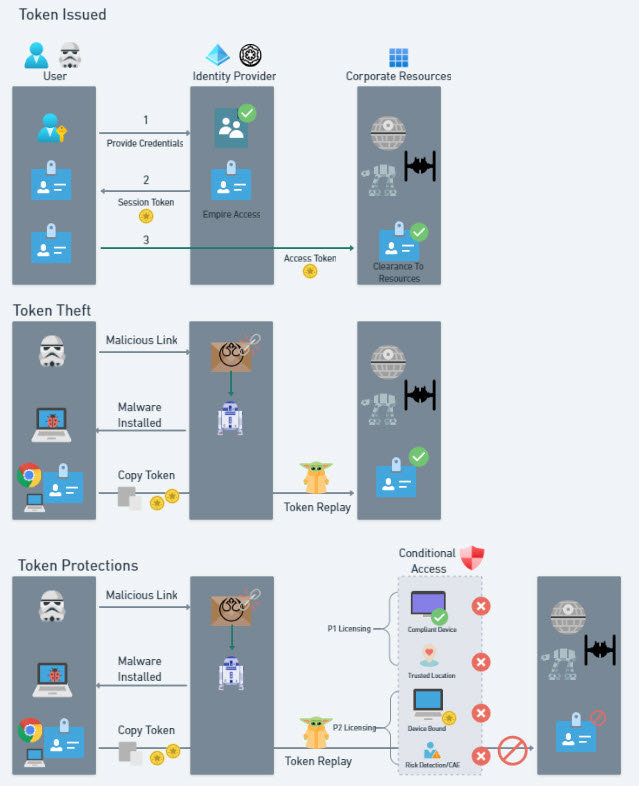
Think of a session token as a digital badge that proves you’ve already authenticated yourself to access certain resources in Microsoft 365, like email, SharePoint, or Teams. Once issued, a token allows users to access these resources without having to re-enter their username, password, or MFA code each time.
Imagine the Star Wars universe: A Stormtrooper reports for duty and gets their access badge from the Empire. This badge (token) proves they are who they say they are and grants them access to the Death Star and Tie Fighters. But what happens if a rebel (cybercriminal) steals that badge? Now, the rebel can waltz right into the Death Star undetected.
In the same way, token theft allows an attacker to impersonate a legitimate user and gain access to their resources without needing the user’s credentials again. The attacker can steal tokens by:
- Installing malware on a user’s device.
- Grabbing session cookies from web browsers like Chrome.
- Using phishing techniques to steal the tokens.
Once they have the token, they can “replay” it on their own device, making it seem like they’re the legitimate user.
Risks to your Business
Once an attacker has successfully stolen a token, they can:
- Access corporate resources (email, documents, Teams).
- Move laterally across the organization by sending internal phishing emails to other employees.
- Exfiltrate sensitive data, such as intellectual property or confidential customer information.
- Set up inbox rules to forward sensitive emails, often used for data exfiltration.
These attacks can have significant consequences for your organization, leading to financial losses, reputational damage, and legal liabilities. So, how can you defend against token theft in Microsoft 365?
Top 4 Security Policies to Protect Against Token Theft
1. Enforce Device Compliance
One of the best ways to mitigate token theft is by ensuring that only compliant devices are allowed access to corporate resources. This means that any device accessing Microsoft 365 must meet your organization’s security standards, such as having antivirus protection, being enrolled in Intune, and using proper encryption.
Use device management and define Conditional Access policies to require that users access resources from a compliant device. Compliance policies we recommend to reduce the risk of successful token theft from devices include:
- To help prevent accidental infection with token-stealing malware, require users running on Windows to run as standard users rather than with device admin rights and require that all devices run up to date anti-malware and virus tools.
- Use storage encryption to protect device content, including tokens, in case someone steals the device itself.
- Enable Local Security Authority (LSA) protection to help protect Entra ID tokens in LSA memory. LSA protection is on by default for new devices and can be enabled for other devices via Intune.
- Use jailbreak or rooting detection for mobile devices. Jailbroken devices are more likely to expose tokens and cryptographic secrets to potential attacks.
Managed Devices shall be required for authentication | Tminus365 Docs
To be clear, this method does not prevent/stop a token from being replayed. This only reduce the chances that the theft will occur to begin with.
2. Use Conditional Access with Strict Location Continuous Access Evaluation
You can further protect your environment by setting up conditional access policies that limit access to Microsoft 365 based on trusted locations (e.g., the corporate network or a VPN). This way, even if a token is stolen, the attacker won’t be able to access corporate resources unless they’re logging in from an approved location. This conditional access policy allows you to configure trusted locations that are strictly enforced with conditional access policies. This policy would protect you in the examples of AiTM and pass-the-cookie attacks. If a users token or cookie were stolen, it would immediately block the attacker since they would be trying to access resources outside of a trusted location immediately. This provides more protections over traditional CAE as those policies where your default ttl for tokens is 1 hour.
- CAE: Continuous access evaluation in Microsoft Entra – Microsoft Entra ID | Microsoft Learn
- Strict Location CAE: Continuous access evaluation strict location enforcement in Microsoft Entra ID – Microsoft Entra ID | Microsoft Learn
3. Token Binding
For more advanced protection, you can enable token binding, which binds session tokens to a specific device. If a token is stolen and replayed on a different device, it won’t work. This feature, though currently in preview, is a powerful way to stop attackers from leveraging stolen tokens on their own devices.
Public Preview: Token Protection for Sign-In Sessions – Microsoft Community Hub (Requires P2 License)
4. Risky Sign In + CAE
Continuous Access Evaluation (CAE) is a feature that monitors session activity and re-evaluates the security of the session periodically. If suspicious activity is detected (e.g., a sudden change in location), CAE forces a re-authentication, which can help catch attackers in the act. If you have Entra P2 licensing, you get many more risk detection data points that are being evaluated. You can also set up conditional access policies to block user sign in when the risk detection is medium or high.
Closing Thoughts: Protecting Your Microsoft 365 Environment
Token theft is a growing threat, but by implementing these security policies, you can dramatically reduce the risk of an attacker gaining unauthorized access to your organization’s resources. Remember, no single solution is perfect—it’s about layering your defenses.
