In last weeks post, I showed you how to use Microsoft Forms and Power Automate to automate employee onboardings across customers. This week, I am going to show you how to do this in HaloPSA leveraging the self-service portal customers can use as a front end. We will be using a webhook in Halo to trigger the workflow automation in Microsoft when a new user form is submitted. This automation performs the following tasks:
- Creates the user in Microsoft
- Adds attributes like job title, department, phone number, etc.
- Assigns a manager to the user
- Assigns a license to the user
- Sends an email to the user’s manager/HR
- Adds the users to groups/sites/Teams
- Mirrors the access of another user (optional)
- Creates automated actions/notifications for Business systems access
- Sends a welcome email to the user including a template to set up Microsoft Authenticator
How much time/money do you spend on new user onboarding?
This will vary by MSP but try to understand the ROI behind this automation. Here is a simple equation to follow:
Cost of Onboardings = Average # of Onboardings X Average Time of Ticket X $ Blended Rate of a Technician X .5 (thinking we will not be able to automate the entire task list in most cases)
Ex:
Average # of Onboardings = 75/m
Average Time of Ticket= 2 hr.
$ Blended Rate of A Technician = $34/hr
75 X 2 X 34 X .5 = $2,550/m or $30,600/Annually
Outside of the financial savings, we also have to factor in the following:
- Hours saved to perform other tasks (75 in our example per month)
- Tailored client experience
- Consistency in process to avoid human error
The Architecture
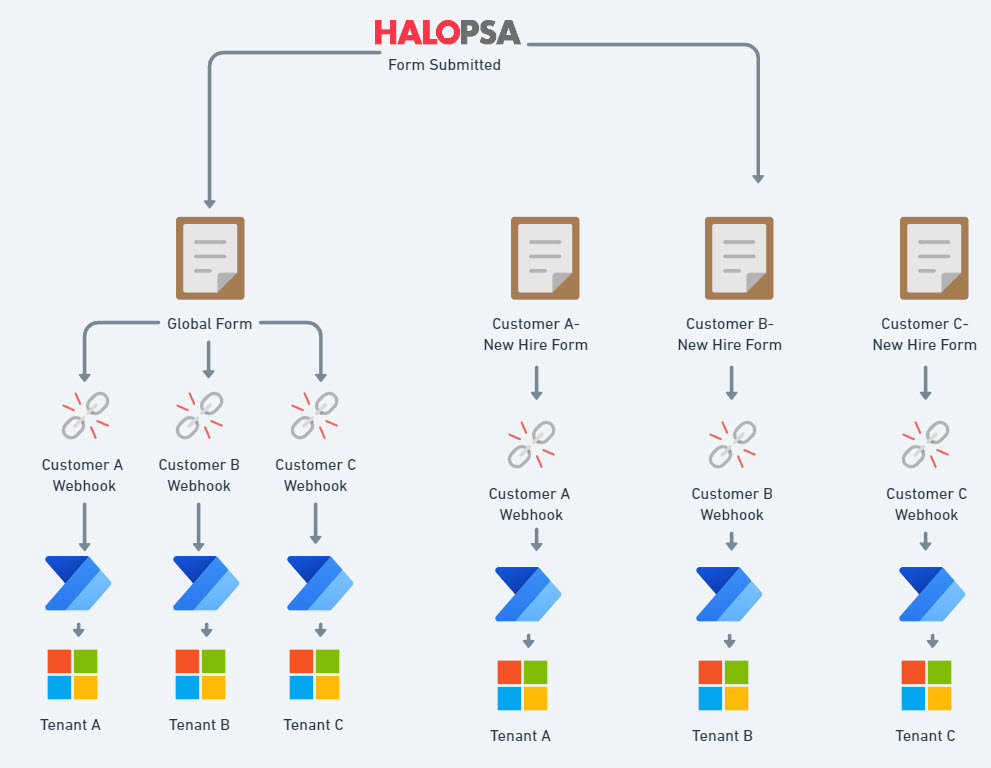
Its important to note we will be creating an automation in each client’s Microsoft environment. In Halo, I am formatting this for two options:
- You have a Global Form that can be used for all customers. You can customize the field groups for the form.
- Each customer gets their own webhook that points to a Power Automate flow in their Microsoft tenant
- You create a custom form per customer that also still points to a unique webhook as well.
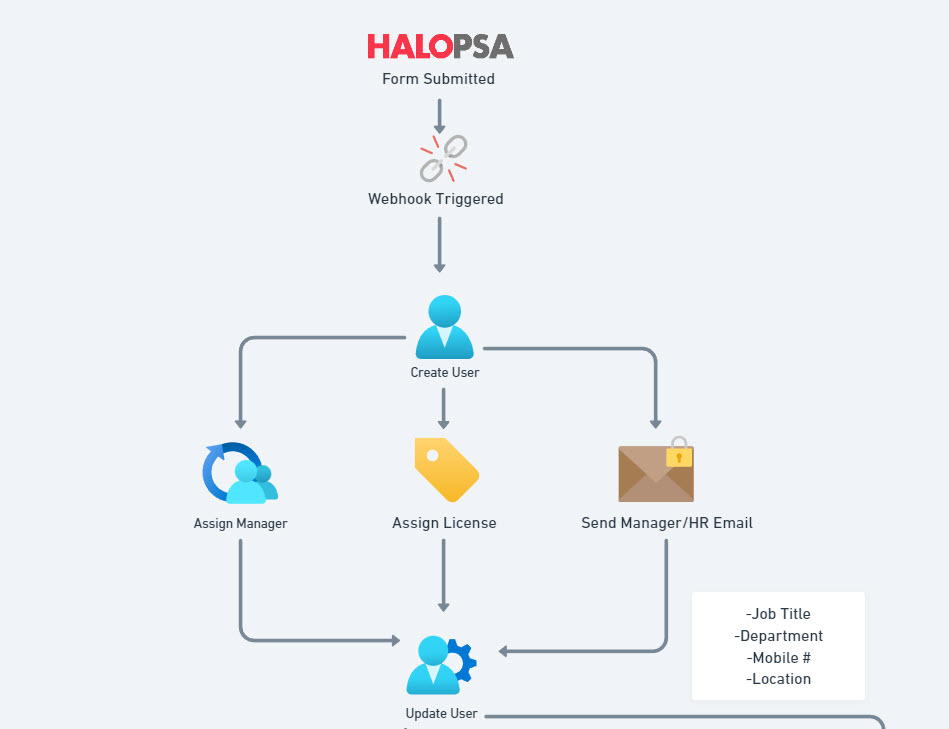
The Steps:
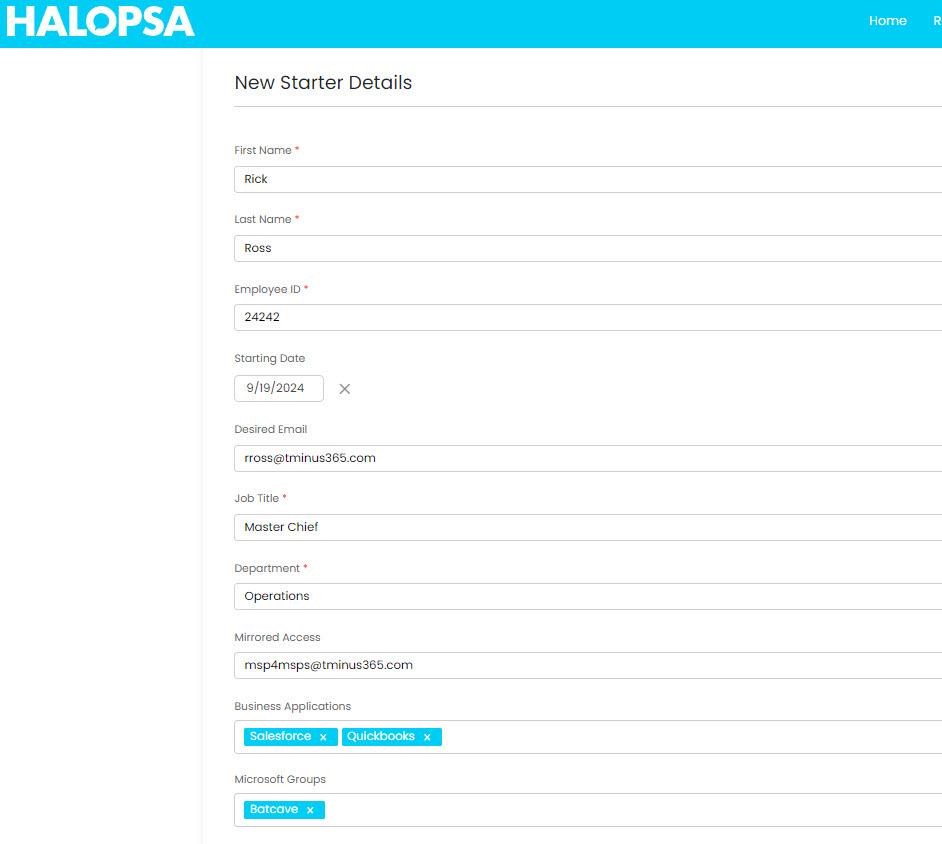
- A Customer fills out a New Hire form from the Self-Service Portal
- A webhook is triggered which kicks off the Power Automate Flow in their tenant
- A User is created in Microsoft. They are assigned a Managed, put into a license group, and updated to reflect proper attributes
- An email is sent from a Shared Mailbox to their manager, HR, or both letting them know the user details, including their password. The email itself is encrypted
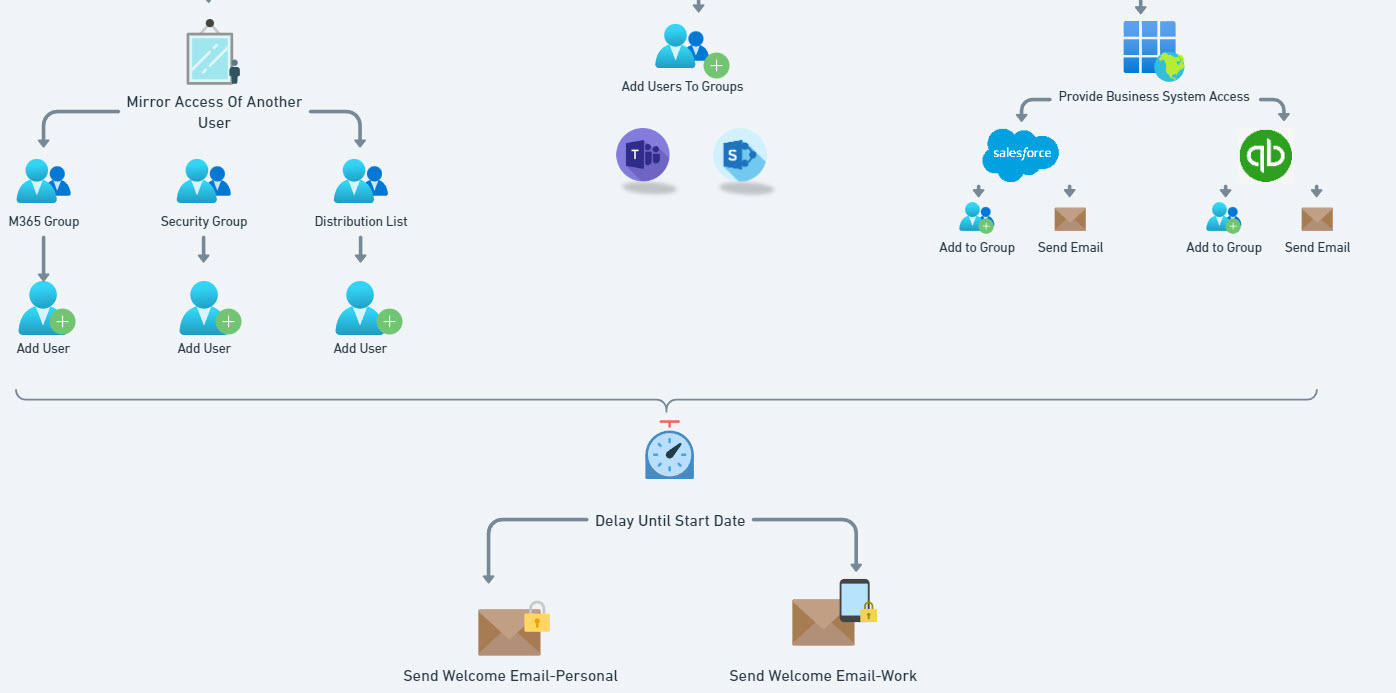
5. Users are added to groups/Sites/Teams based on groups designated or mirroring the access of another user
6. Specific actions can be chained to Business Systems like email notifications.
7. A delay is instituted until the users start date
8. A welcome email is sent to both their personal email and work email. The work email contains the MFA setup guide.
Prerequisites
- You need to have admin rights in Halo to:
- Create/Modify Field Groups
- Create Webhooks
- In the customers M365 Tenant:
- Create a Service Account for the Power Automate Flow. Can call this something like automation@<Customerdomain.com>
- License this user with a Power Automate Premium License (cost $20/m) but is needed for the Webhook trigger
- Assign the User and Group Admin Role to the service account. We need these rights to perform the actions in the workflow
- Create/Use a Shared mailbox to send auto-generated emails. EX: EmployeeLifecycle@<customerdomain>.com
- We are assigning licenses via group membership so you will need to create a group to assign licenses. Ex. If you use Business Premium, call the group “Microsoft 365 Business Premium Users”
- See more info: https://learn.microsoft.com/en-us/entra/identity/users/licensing-admin-center
- https://learn.microsoft.com/en-us/entra/identity/users/licensing-groups-assign
Integrating HaloPSA and Power Automate
At first I went down the path of looking at the documentation in HaloPSA, which references creating a custom connector:
As you go down this path, you will eventually figure out that this DOES NOT WORK. Seems to be a limitation of the authorization code character limit in Microsoft that Halo has not fixed yet. Ref:
Instead, I made a webhook since Power Automate can support that. Pros and Cons of this method over the custom connector:
- The Webhook acts as a trigger when the form is submitted, so its actually way better for our use case on the initial kickoff of the flow
- The custom connector is basically allowing us to tab into the Halo API as actions in Power Automate. I would love for the flow to support writing back what we did to the ticket using the custom connector. You COULD overcome this with an HTTP trigger in Power Automate (which I will show in a future post) which is just you effectively calling the API as part of the flow instead of using the custom connector. I just don’t like it as much because its more clunky and we have to figure out how we can pass in secrets to generate a token securely like using Azure Key Vault. TLDR: We increase the number of actions we have to take 10x.
Configuring a Webhook
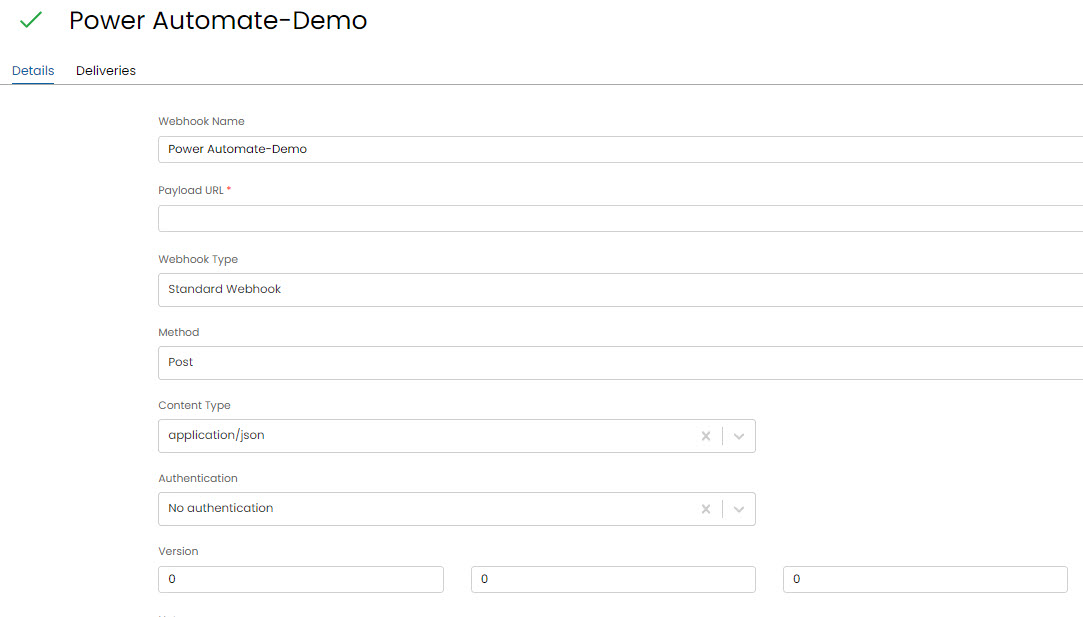
- In Halo, go to Configurations>Integrations, Webhooks>New
- Here you will leave all fields as default except for the Payload URL (which we will get from Power Automate) and Events
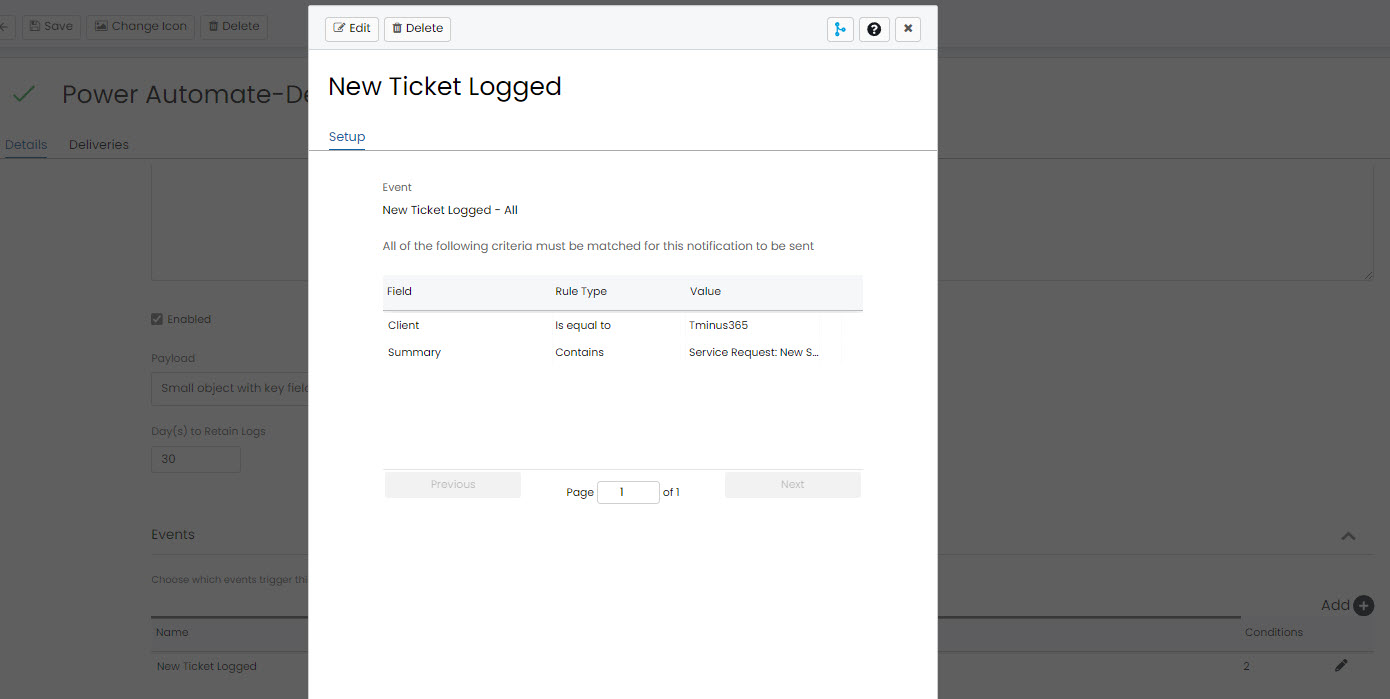
- In the Events, you will add an event for “New Ticket Logged”
- Event Triggers:
- Client Name is equal to <Client You want this webhook to be for>
- Summary containsService Request: New Starter Request (or whatever you form is called)
In Microsoft
- Go to https://make.powerautomate.com/
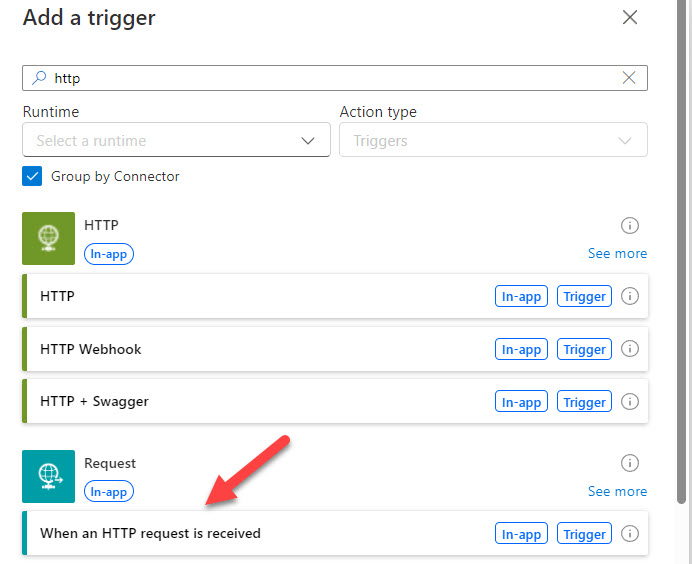
- +Create > Automated Cloud Flow>Skip the starter steps
- For the Trigger, search for HTTP and select When a HTTP request is received
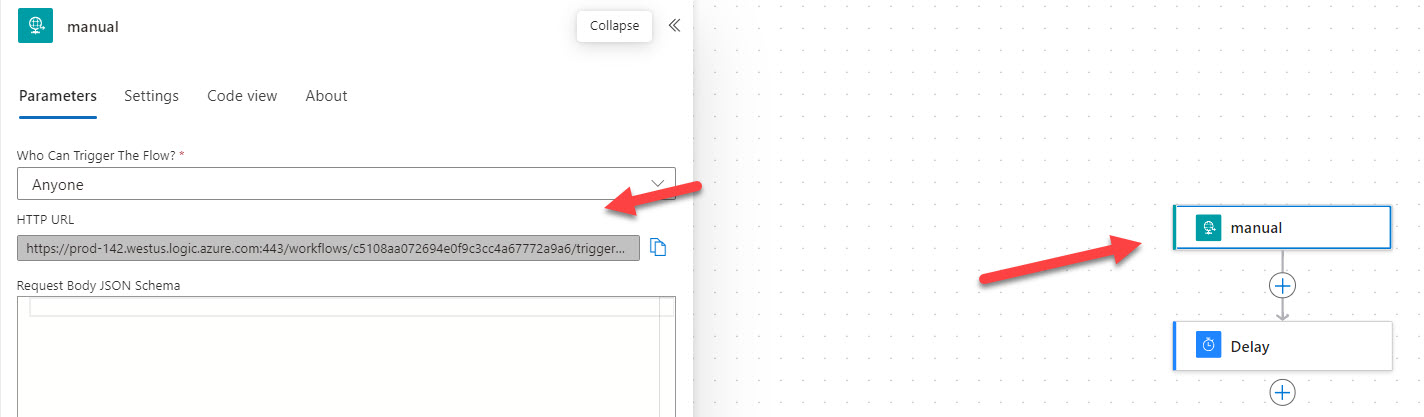
4. Change the “Who can trigger the flow” to Anyone.
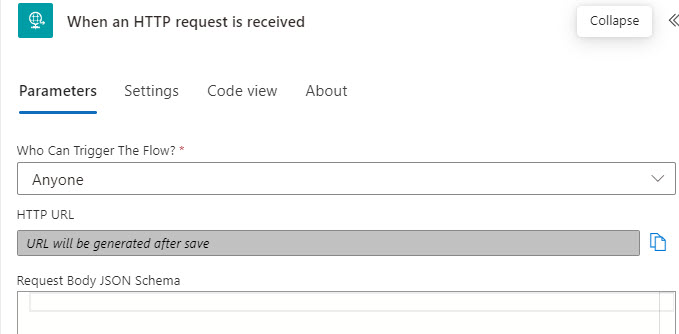
5. We have to generate at least one action in the workflow to be able to save any get our webhook URL. I like to just search for “Delay” and add a delay of 30 sec as a placeholder till we can get this done.
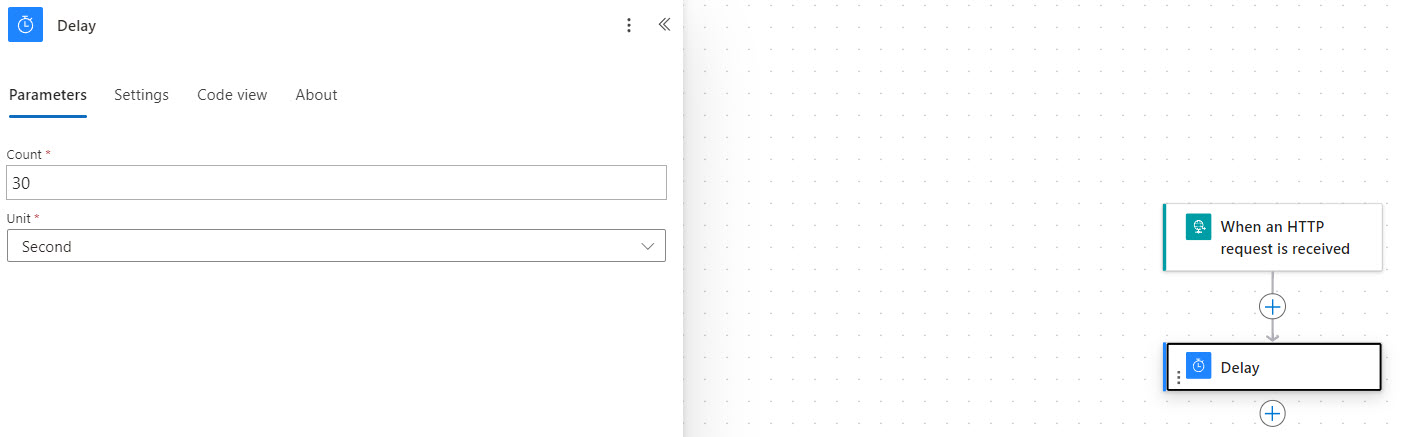
6. After you click Save, a URL will be generated in your HTTP action. Copy this and past it back into Halo. Have the webhook in Halo
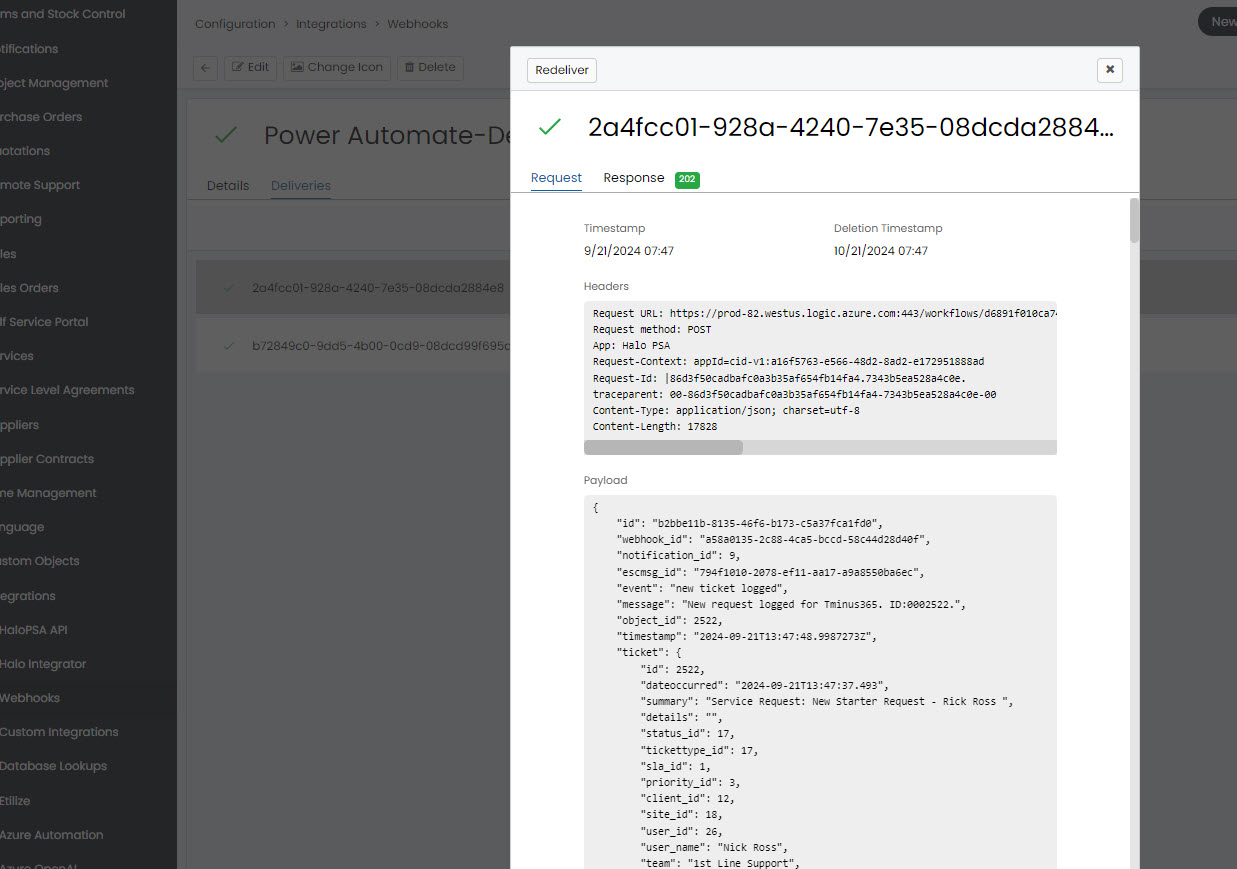
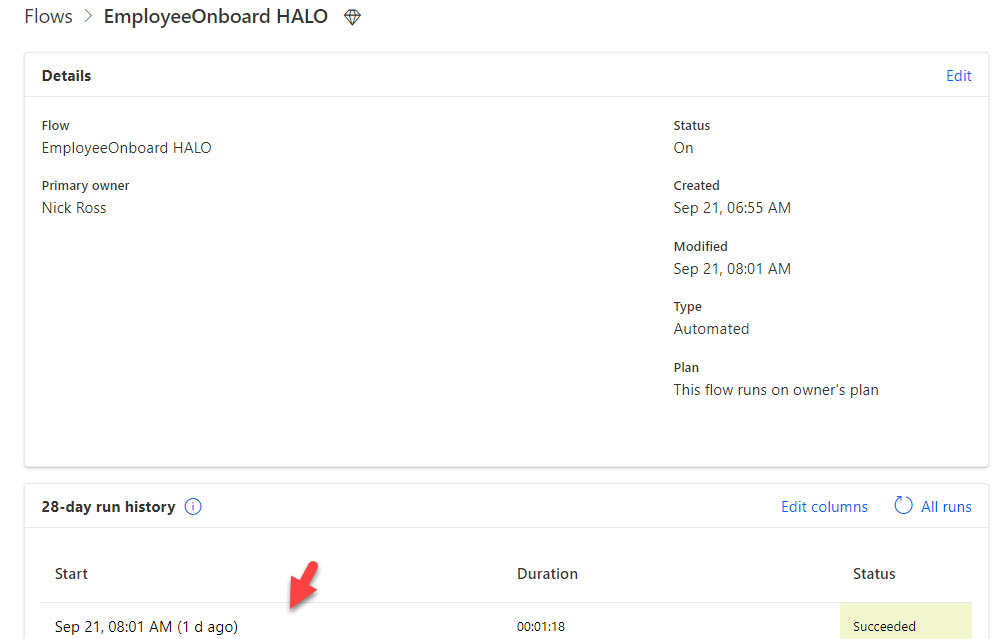
7. You can test the webhook by submitting a form tied to the trigger. After you do, you will be able to see the results both in Halo and In Power Automate.
Configuring Halo forms
I am going to assume most of you out there who use Halo are more familiar than me on creating forms. Specifically, I am using:
- Custom Objects => Used to create form fields like “Manger”, “Microsoft Groups”, etc
- Field Groups => Use to bundle my custom objects
- Ticket Types =>Used as the Global form or could be used to create forms on a per customer basis
I am about 2 weeks in to learning Halo so if there is anyone out there who has a better way, let me know 🙂
Power Automate Template
I built a template you can use to upload in customer environments and test. You can upload the following template into a tenant and customize. Check out the full tutorial video below to see how I create all of these actions.
A Quick Call Out on More Advanced Functionality:
If I spent more time with this flow, here are the other potential things I would include:
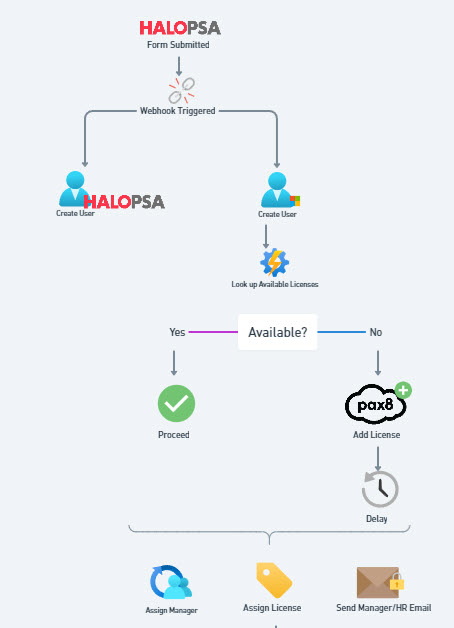
- HALOPSA API => Using an HTTP request, I could interact with the HALOPSA API. I would use this to create the user as a contact in Halo at the time of creation (let me know if this already natively exists)
- PowerShell with Azure Automation=> Our flow uses a group to license users. This breaks down if we are out of licenses. I would integrate an Azure automation which would use PowerShell to look up and see if there were available licenses and assign them this way vs the group membership
- Pax8 Integration => Leveraging the Pax8 API, I would update the license count if there was not automatically one available and wait till it fully provisions to assign the license to the user.
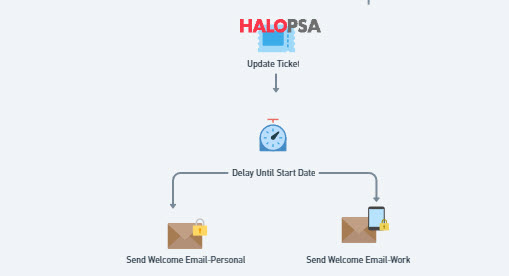
- HALO API Ticket Update => I would also like to use the API to update the ticket with details of what the automation performed.
Given the complexity of the tasks we are bolting on, a tool like Rewst starts to become more of a better fit given most of this integration comes out of the box. Benefits:
- Integration capabilities with the customers M365 Tenant (using your GDAP rights)
- Single management portal vs needing to put all of these automations in each clients tenant (makes it easier if they offboard from you as well)
- Integration to Halo, Pax8, Twilio, and other MSP tools.

