
Purpose
The purpose of this article is to explain Security Defaults and end of life for baseline policies. I give you recommended actions to take to replace these policies and how to manage security defaults for you customers in the future.
Full Video Walk-through
For those of you who need more of a visual.
Highlights/Considerations
Enforced February 29th, 2020
Enforcing MFA for all User in a Tenant
Blocking Legacy Authentication
End of Life For Baseline Policies
What are Baseline Policies?
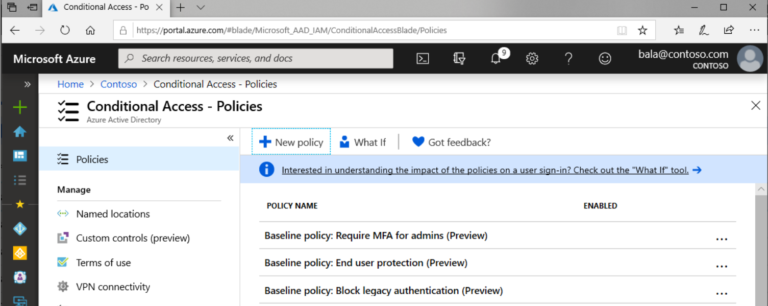
Baseline Policies are part of Microsoft’s conditional
access. These polices allowed you perform management task such as requiring MFA
for all admin users or blocking legacy authentication across a tenant in a
couple of clicks. The main reason MSPs would have added these policies was due
to Microsoft’s enforcement of the Secure Application Model, back on August 1,
2019. These requirements made you enable MFA for all of your Partner Center
user accounts. MSPs may have enabled these policies across some of their
customer’s tenants as well in efforts to heighten security. In some cases, they
may not have enforced these baseline policies and simply enabled MFA manually
in their tenant accounts. Baseline policies were a part of conditional access
which is a feature only seen in tenants with M365 Business, EMS+E3, and Azure
Active Directory Plan 1.
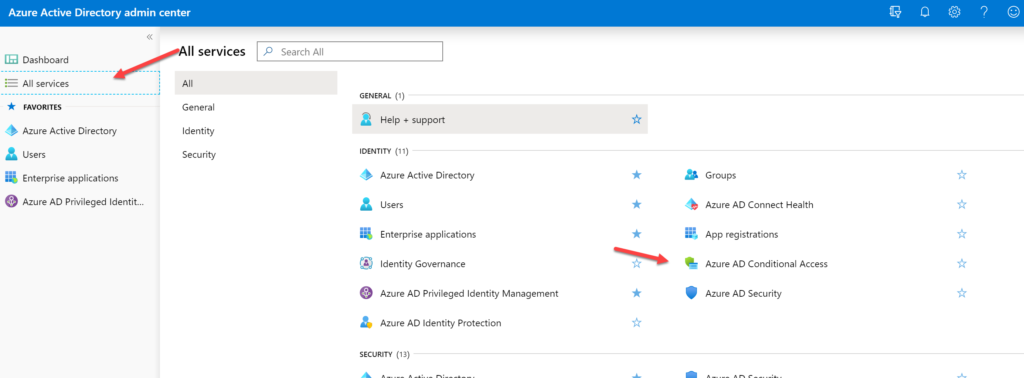
You can navigate to these policies is a couple of different ways. One of the easiest ways would be the following:
Portal.office.com>Login a Global Admin>Admin Centers>Azure Active Directory>All Services>AD Conditional Acces
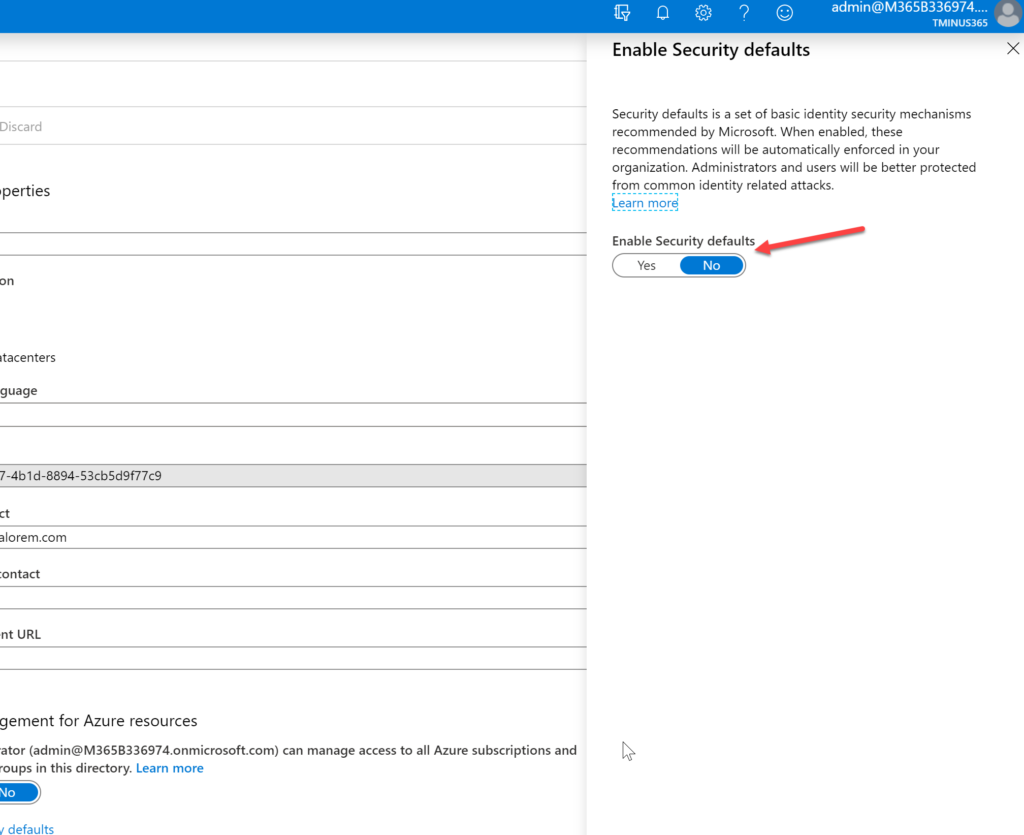
Security Defaults
Microsoft Relayed the Following Email:
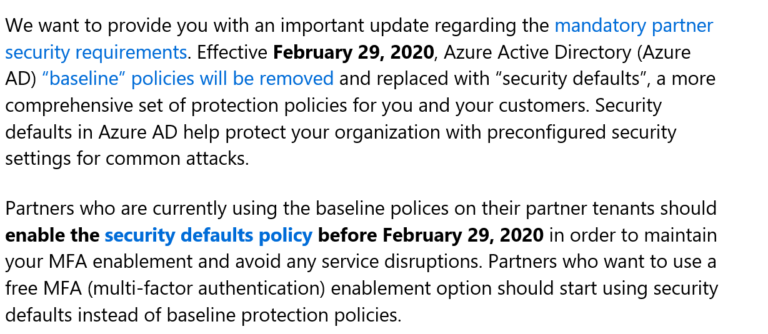
Navigation To Security Defaults
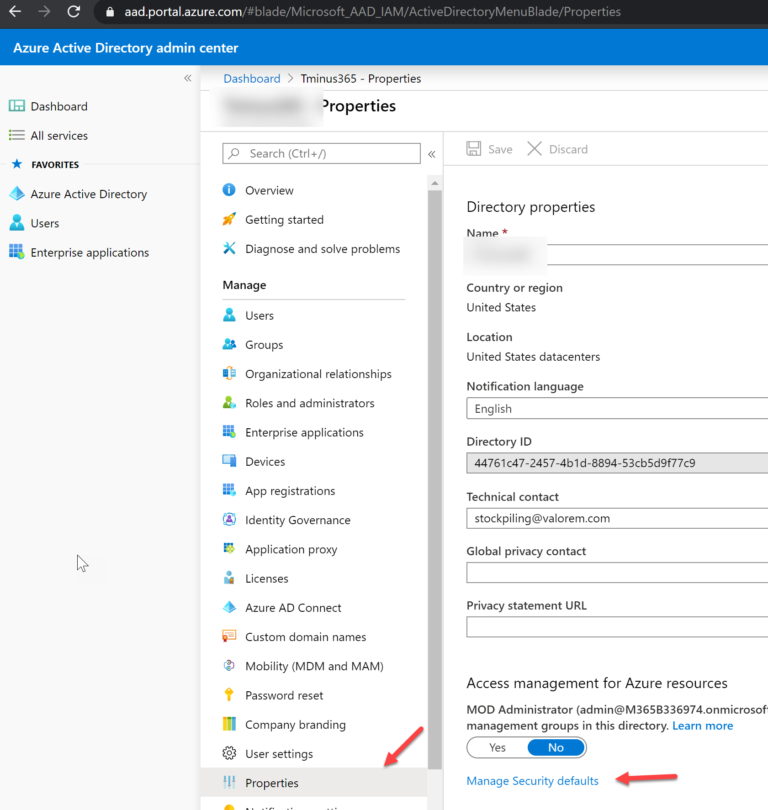
You can navigate to these policies is a couple of different ways. One of the easiest ways would be the following:
Portal.office.com>Login a Global Admin>Admin Centers>Azure Active Directory>Propoperties>Manage Security Defaults
Highlights
- Mandatory Partner Requirement not Customer
- Enforcing MFA Across all Users in the Tenant
- Blocking Legacy Authentication(IMAP/POP/SMTP Protocols)
- Enforcing MFA for users who access the Azure Portal, Azure Powershell, Azure CLI
- Click Here for the Full Article
Concerns
- On by Default in Net New Tenants
- Users have 14 days to enroll in MFA
- Microsoft Authenticator App only 2nd factor method available
- Printers/Copies with SMTP Relay will break
- Exchange Online Powershell Cmdelts will not work
- Ticketing Systems/Apps that use IMAP/POP will receive disruption in service
Recommended Actions
Ok so some huge concerns here! Since this is manadatory for Partner requirements we need to make sure this isn’t going to affect our ticketing systems or other apps we may be using to block legacy authentication. It may be best to use app passwords for those applications if we do not have the licensing for conditional access. I will be going over a couple different solutions here depending on your licensing.
Option 1: Turn on MFA and Implement App Passwords for Legacy Authentication
Applies To:
- All Partner Center User Accounts
- Customer Tenants without Conditional Acces
Licensing Considerations:
This doesn’t require a conditional access policy so all 365 license types should work here. We are simply enabling MFA and using App Passwords to bypass mfa on apps that have legacy authentication
Steps:
Instead of turning on the Security Defaults, we can simply enforce MFA and add App Passwords. For Partner Center Accounts that require Security defaults or Conditional access policies to be turned on you can create the app passwords for your legacy authentication apps. This also would also ensure that our users don’t only have the Microsoft Authenticator app to chose from when enrolling in MFA. Microsoft references the following in their security requirement documentation:
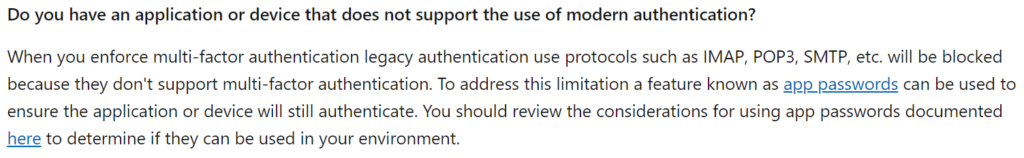
For more on App Passwords, click here
How to Create A New App Password
*NOTE* While we recommend this as a temporary fix, please take note that support for legacy auth is ending in October of this year:
Microsoft announced back in 2018 that end of support was coming for Basic Authentication and we’ve been updated with an official date of Oct 13,2020.
“Today, we are announcing that on October 13th, 2020 we will stop supporting and retire Basic Authentication for Exchange Active Sync (EAS), Post Office Protocol (POP), Internet Message Access Protocol (IMAP), and Remote PowerShell (RPS) in Exchange Online. This means that new or existing applications using one or more of these API’s/protocols will not be able to use Basic Authentication when connecting to Office 365 mailboxes or endpoints and will need to update how they authenticate.”
“Please note this change does not affect SMTP AUTH and we will continue to support Basic Authentication for it in Exchange Online at this time. With the large number of solutions, devices, and appliances that use SMTP for sending mail we are working on ways to further secure SMTP AUTH and will continue to update you as we make progress.”
Turn on MFA for Users
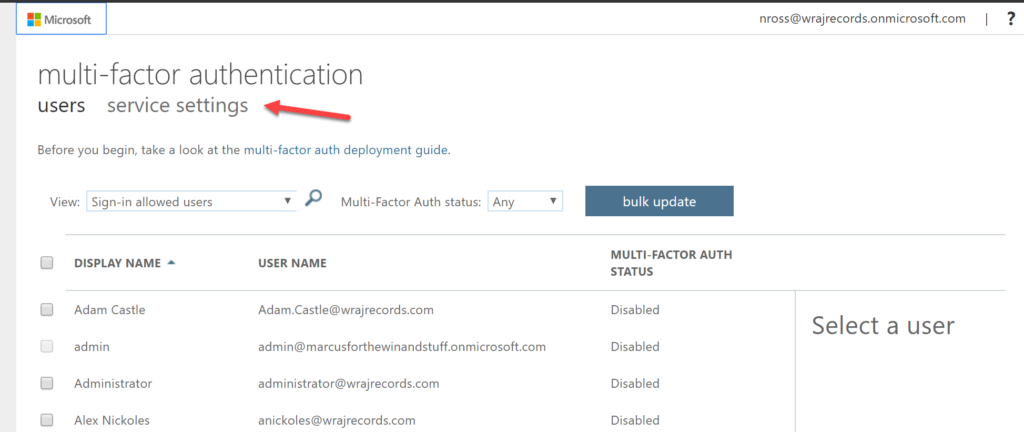
Navigate to Portal.office.com>Click Admin Centers>Azure Active Directory
Click Azure Active Directory>Users>…Multi-Factor Authentication
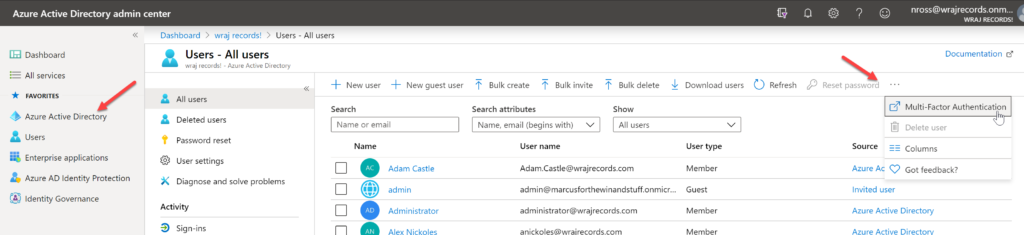
From this portal, you can enable MFA on demand for users and control the settings with Service Settings:
Option 2: Set up Conditional Access Policies
Applies To:
- All Partner Center User Accounts
- Customer Tenants with Conditional Access Licensing
Licensing Considerations:
- EMS+E3\E5
- Azure AD P1 or P2
- M365 Business
- M365 E3/E5
If you have a tenant with Conditional Access I would definitely recommend to use this option. Either Security Defaults can be turned on or you can add Conditional Access policies. Both cannot be on at the same time. If you try to create a Conditional Access policy in a tenant with Security Defaults on, it will not allow you to save until you turn off the settings. Conditional Access allows use to bypass MFA on trusted networks and bypass MFA for certain applications. Ideally you would you this to whitelist legacy authentication apps and login credentials on your network that you use for SMTP relay (printers/scanners) or Exchange Online Powershell Cmdlets. Click Here for my full tutorial on Conditional Access policies
Steps: Turning on MFA for Users, Bypassing MFA for Legacy Auth, Bypass MFA on trusted Network
Navigate to Portal.office.com>Click Admin Centers>Azure Active Directory

Click All Services>AD Conditional Access
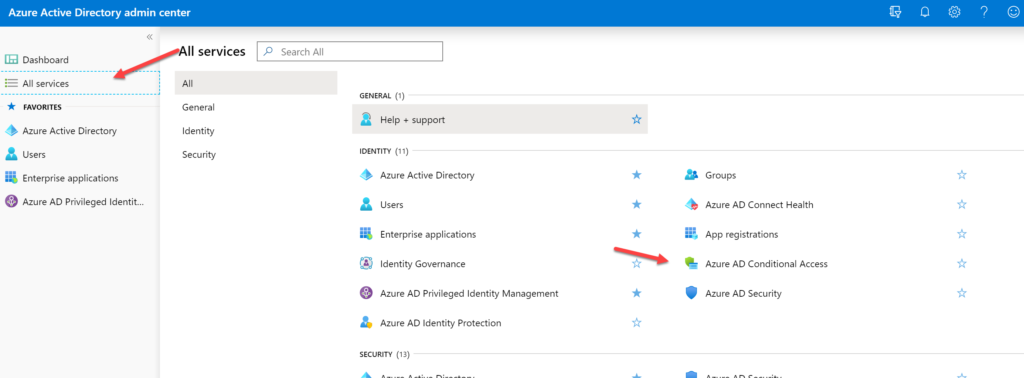
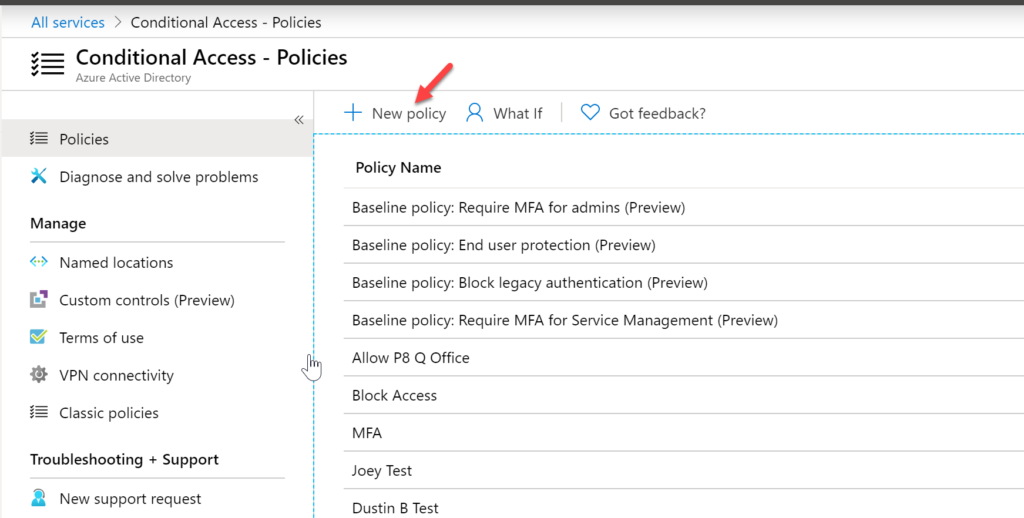
Click +New Policy
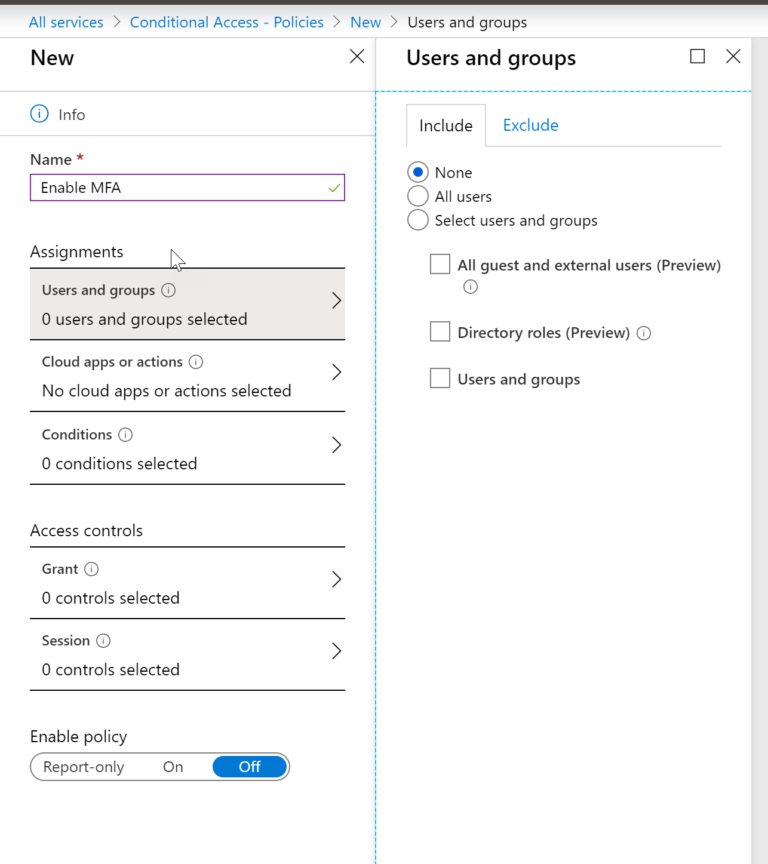
Here we can name our policy and define our scope. You can apply this to all users, certain groups, or to certain directory roles
Next you can define you scope of Apps that apply. If you have legacy authentication apps in your tenant, you can either choose to exclude them using that tab here or you can give them an app password as defined earlier in this guide.
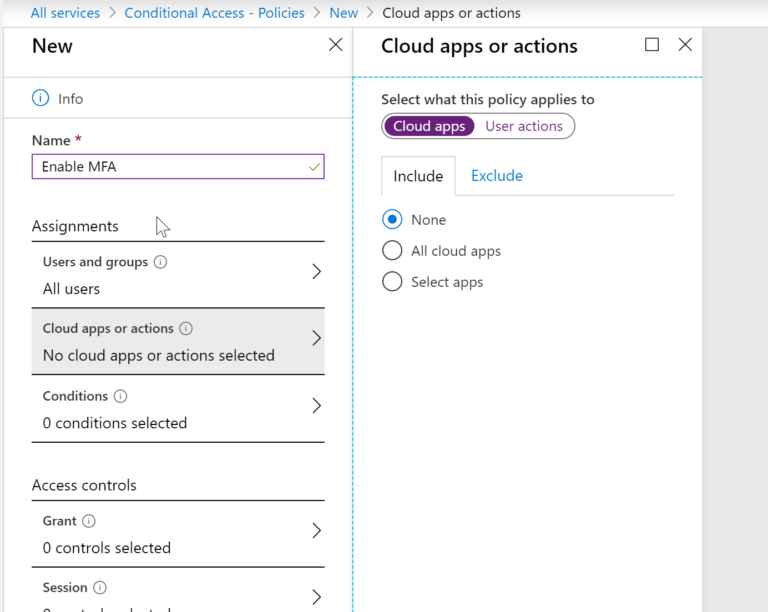
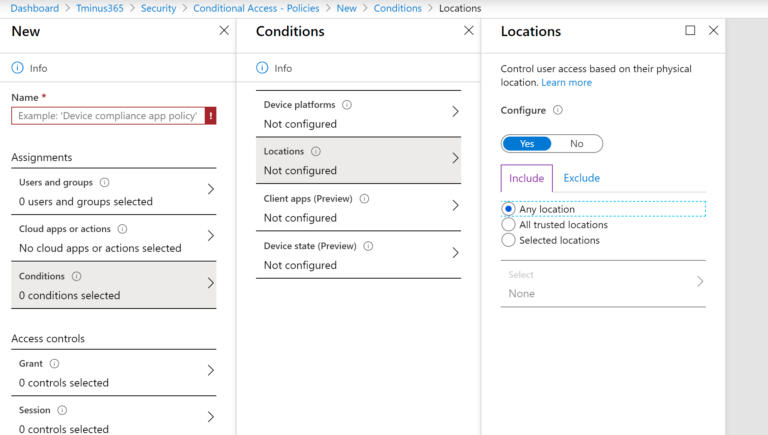
On the home page of Conditional Access, you can click on Named Locations to Add a trusted network. In the conditions section here you can include all locations and exclude trusted locations. This is how you would bypass MFA on a trusted network for printers using SMTP relay or Exchange Online Powershell cmdelts.
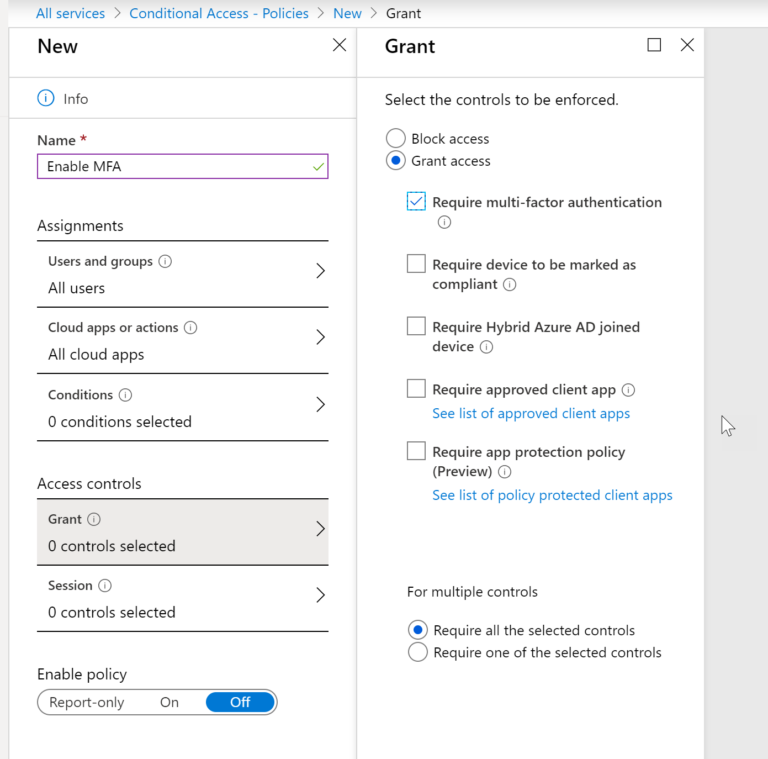
On the Grant Tab, we can select to Require MFA and then choose to enforce the policy to save.
Blocking Legacy Authentication and White-listing a certain App
Printer, Scanner, Copier Considerations
I would recommend using the conditional access policies i mentioned here to bypass MFA when you are on your trusted network. In addition, i would recommend Direct Send, Option 2 Listed in the following support article: Click Here
FAQ
Q: What license do I need for Conditional Access?
A: You need Azure AD P1 ($6), EMS+E3/E5 ($8.75), M365 Business ($20), M365 E3/E5 ($32, $64)
Q: Is MFA turned on by Default in new tenants?
A: Yes, after Feburary 29th, 2020, Security Defaults will be on by default in all net new tenants
Q: What methods of enrollment for MFA are available to end users with Security Defaults?
A: Only Microsoft Authenticator App
Q: Is MFA required for all user with Security Defaults turned on?
A: Yes, MFA is required and will be strictly enforced after 14 days after the users first sign-in
Q: Is this a hard enforcement for Customer Tenants?
A: No, the hard requirement is for Partner Tenants to meet Partner Security Requirements
Q: How do I turn off/on security defaults in customer tenants?
A: Sign in as a global admin to Office.com>Admin Centers>Azure Active Directory>Azure Active Directory>Properties>Manage Security Defaults
Q: How do I avoid Security defaults blocking legacy authentication to my ticketing system or other apps using these protocols?
A: Either Use App passwords or a conditional access policy to bypass MFA. Steps for these detailed in this article.
Q: How do i allow for SMTP relay at my customer sites with Security Defaults turned on?
A: Bypass MFA with a conditional access policy or consider Direct Send
Q: What is the difference between modern authentication and legacy authentication?
A: Legacy authentication refers to protocols that use basic authentication. Typically, these protocols can’t enforce any type of second factor authentication. Examples for apps that are based on legacy authentication are:
Older Microsoft Office apps
Apps using mail protocols like POP, IMAP, and SMTP
Single factor authentication (for example, username and password) is not enough these days. Passwords are bad as they are easy to guess and we (humans) are bad at choosing good passwords. Passwords are also vulnerable to a variety of attacks like phishing and password spray. One of the easiest things you can do to protect against password threats is to implement MFA. With MFA, even if an attacker gets in possession of a user’s password, the password alone is not sufficient to successfully authenticate and access the data.
Modern authentication is an umbrella term for a combination of authentication and authorization methods between a client (for example, your laptop or your phone) and a server, as well as some security measures that rely on access policies that you may already be familiar with. It includes:
-Authentication methods: Multi-factor authentication (MFA); smart card authentication; client certificate-based authentication
-Authorization methods: Microsoft’s implementation of Open Authorization (OAuth)
-Conditional access policies: Mobile Application Management (MAM) and Azure Active Directory Conditional Access
